Contents:
A new malware campaign employs fake OnlyFans content and adult lures to install the remote access trojan ‘DcRAT,’ enabling threat actors to steal data and credentials or deploy ransomware on infected devices.
Using OnlyFans for malicious ends is nothing new; in January 2023, attackers exploited an open redirect on a UK government site to send users to malicious OnlyFans sites.
The new campaign, discovered by eSentire, has been running since January 2023 and involves the distribution of ZIP files that contain a VBScript loader the victim is tricked into manually executing in the belief that they are about to access premium OnlyFans collections.
The Infection Chain
Malicious forum posts, IMs, malvertising, or even Black SEO sites that rank highly for certain search terms could all be links in the infection chain. Eclypsium provided a sample that purports to be naked images of Mia Khalifa, a former actress in adult films.
The VBScript loader is a heavily modified and obfuscated version of a Windows printing script seen in a 2021 campaign discovered by Splunk.
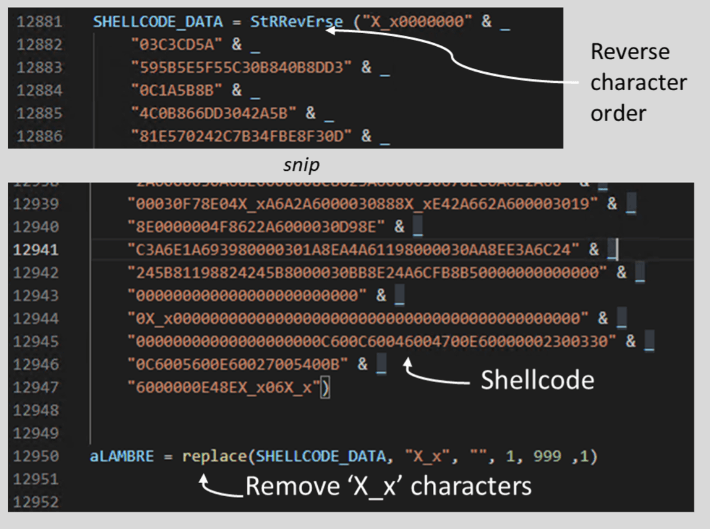
When launched, it uses WMI to determine the OS architecture and spawns a 32-bit process, extracts an embedded DLL file (“dynwrapx.dll”), and registers the DLL with the Regsvr32.exe command. This grants malware access to DynamicWrapperX, a tool that allows functions from the Windows API or other DLL files to be called.
Finally, the payload, dubbed ‘BinaryData,’ is loaded into memory and injected into the ‘RegAsm.exe’ process, a legitimate component of the.NET Framework that is less likely to be detected by antivirus software.
DcRAT’s Capabilities
The injected payload is DcRAT, a modified version of AsyncRAT that is freely available on GitHub and was abandoned by its author after several abuse cases surfaced online. One of these incidents occurred in October 2021, when a politically motivated threat actor dropped it onto compromised systems alongside several other malware families, explains Bleeping Computer.
DcRAT is capable of keylogging, webcam monitoring, file manipulation, and remote access, as well as stealing credentials and cookies from web browsers and stealing Discord tokens.
Additionally, DcRAT includes a ransomware plugin that targets all non-system files and appends the “.DcRat” filename extension to encrypted files.
Users are encouraged to exercise caution when downloading archives or executables from suspect sources, especially those offering free access to premium/paid content.
If you liked this article, follow us on LinkedIn, Twitter, Facebook, and YouTube for more cybersecurity news and topics.


 Network Security
Network Security
 Vulnerability Management
Vulnerability Management
 Privileged Access Management
Privileged Access Management
 Endpoint Security
Endpoint Security
 Threat Hunting
Threat Hunting
 Unified Endpoint Management
Unified Endpoint Management
 Email & Collaboration Security
Email & Collaboration Security










