Contents:
Dark web, deep web, clear web – it’s confusing. That’s before you try and use the thing. Let’s start with how to access Dark Web websites.
So, if you want to learn all about Tor Onion, Silk Road, secret, hush-hush Governmental ops, you came to the right place.
What is the dark web?
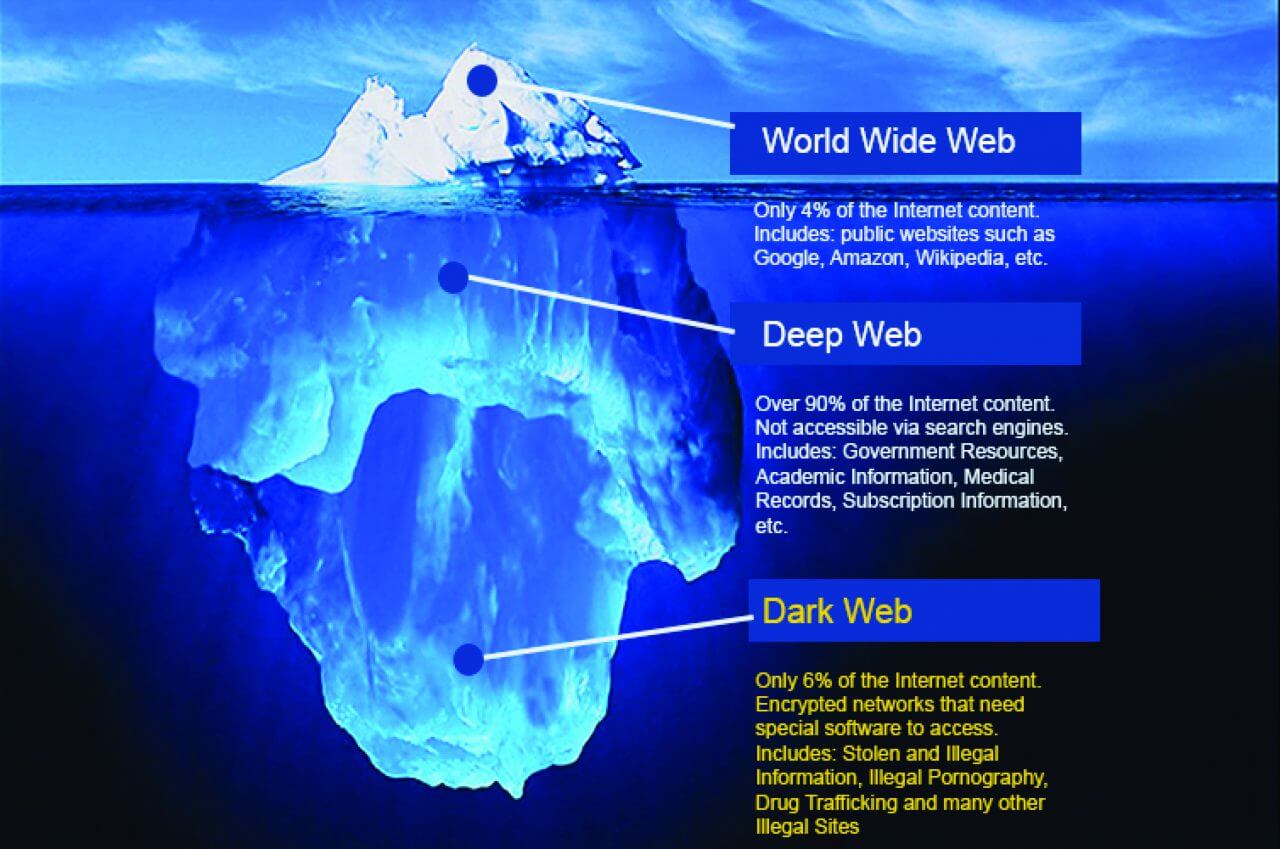
The Dark Web is a hidden part of the internet, completely different from the clear web we all use daily. When you search for something on Google or Bing, you’re using the clear web.
This is where all the cat videos and trending YouTube songs live, easy to find and access. But even though it seems like there’s a lot out there, this only makes up about 4% of the entire internet. So, you might wonder, what about the other 96%?
Deep web vs. dark web
Let’s break down the deep web and dark web in plain terms.
The deep web is just the part of the internet you can’t find with a search engine. It’s not mysterious or spooky; it’s home to everyday things like scientific research, medical records, private financial information, and secure communications.
If you’ve ever checked your medical results online through a portal that required a login, you were navigating the deep web. It’s huge, making up about 90% of the internet, but it’s mostly mundane, hidden behind login screens for privacy and security.
Now, the dark web? That’s a different story.
Think of it as the internet’s wild card. It makes up about 6% of the internet, and it’s where you find everything from illegal marketplaces to forums for whistleblowers.
It’s a mixed bag of the very bad and the potentially good, attracting both criminals and those seeking freedom from surveillance for various reasons.
Privacy and anonymity are the dark web’s hallmarks, thanks to a network of servers that hide users’ identities and locations.
More on Tor Onions
The Tor Onion Browser is essential for accessing the dark web, designed for user anonymity. Unlike the regular internet, the dark web doesn’t use standard URLs or search engines. Instead, sites have complex .onion addresses, making them difficult to find without the exact URL.
This part of the internet is notorious for illegal activities, facilitated by the anonymity it offers. Crimes range from data theft and selling illegal goods for cryptocurrencies to human trafficking and more severe offenses.
Understanding the dark web, including safe navigation with the Tor Browser, is crucial for anyone interested in internet privacy and security issues, highlighting the balance between anonymity and the potential for misuse.
Preparing to Set Sail
Source: WikiHow
#1. Install a VPN
Navigating the dark web requires extra layers of privacy, not just because of its content but due to legal scrutiny. The US Supreme Court has indicated that even casual browsing could lead to legal consequences.
A VPN hides your internet activity, making it harder for your connection requests to be traced back to you. It’s a precaution to protect yourself before diving into the dark web. For recommendations on choosing a VPN, look for expert reviews and articles.
#2. Install an Adequate Browser
Don’t use standard browsers like Chrome or Firefox for the dark web. These browsers have tracking technologies that compromise anonymity.
Instead, download Tor, the most secure and user-friendly option for accessing .onion sites. Despite some skepticism about its origins and privacy due to its military development, Tor remains the preferred choice for safe dark web navigation.
How Tor and VPNs protect you on the dark web
Choosing Tor over standard browsers is crucial for dark web navigation due to its unique privacy features.
Unlike regular browsers that directly connect to websites via your ISP’s DNS, Tor anonymizes your journey by routing your request through several relays before reaching its destination.
Tor relays are servers run by volunteers, designed to keep your activities private and untraceable.
By using Tor, and especially in combination with a VPN, your internet signal is encrypted, making it invisible to your ISP. It knows you’re accessing Tor but can’t see beyond that.
This multi-layered redirection ensures your actions leave no trace, offering a high level of anonymity.
Should I only use a VPN to access the dark web?
No, you need more than a VPN to enter the dark web safely. There’s no broad consensus on dark web safety, but you at least need to use Tor and VPN together. Once you have those, there are several ways to tunnel through the dark web.
Method I – Tor over VPN
Sounds very techie, doesn’t it? Well, it’s really not that complicated – using the Tor over VPN method means connecting to a VPN service before using the Tor browser. Have to say that this is the most popular and safest method to access onion links, and, on my part, a marriage made in Heaven: Tor’s an excellent ‘anonymizer’, while VPN safeguards your privacy.
When using this method, Tor will encrypt your request, which will pass through your ISP unhindered. From there, it will go through a VPN server that conceals your IP and wipes geo-locations tags and other elements your Government or ISP might use to track the request.
Next step – your request will be transferred to Tor entry nod which in turn transfers to one or more Tor relays. From there, it gets slingshot to several Tor exit nodes. Afterwards, your request will be matched with the appropriate website. Tricky, but effective; that’s why it’s, by far, the best method to access dark web content.
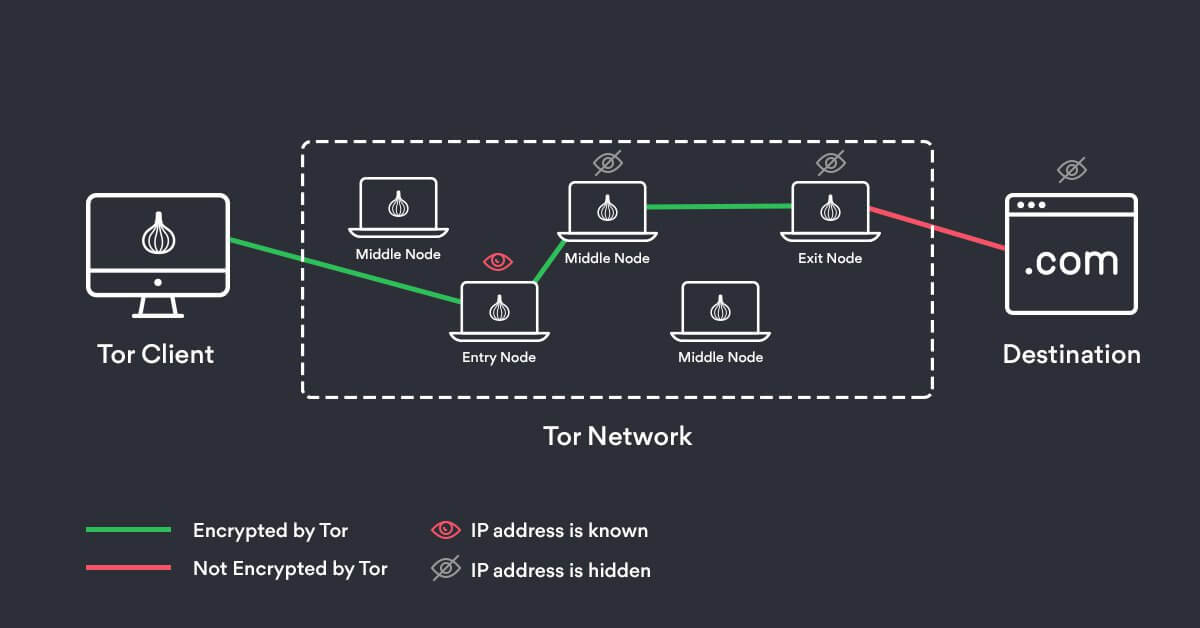
Source: NordVPN
Pros of using Tor over VPN:
- Session logs are not stored (metadata, IP address).
- Traffic’s completely encrypted.
Con(s):
- It doesn’t offer protection against malicious Tor exit nodes.
Method II – VPN over Tor
Not very safe, but it’s still useable. Recall how Tor oven VPN works? Well, VPN over Tor is basically its opposite – instead of going through the VPN first, the signal passes through the Tor network, before going through the VPN. Why is this method so unpopular? Because it’s not as safe as Tor over VPN.
If the signal goes through the Tor network first, your ISP will be able to see that you are attempting to connect to a Tor node. Though no one should bat an eye just because you’re attempting to access the dark web, keep in mind that in some countries, like the United States, even a simple foray can get you in trouble.
Pro(s) of using VPN over Tor:
- Great if you trust your ISP, but not the VPN provider.
- Can bypass blocked Tor nodes.
Con(s):
- ISP can see you trying to access onion content.
- Susceptible to end-to-end timing attacks.
Now, if you want to see what lurks in the dark corners of the Internet but don’t really trust Tor, there are alternatives.
Here is a couple of them:
- I2P – great privacy protection and can access hidden onion links.
- Matrix.org – an open-source project just like Tor. Great for IoT data transfers, chats, and WebRTC signaling.
- Orbot – basically a Tor for Android.
- Globus Secure Browser – paid Tor alternative. VPN-powered. It allows the users to select preferred geolocation. If you want to take it for a spin, Globus features a five-day trial period.
- Comodo Ice Dragon – Firefox offspin. Employs multiple malware safeguards. Open-source project.
- FreeNet – open-source project. Sports the Darknet and OpenNet anonymous browsing technologies.
#3. Install a VM or Disposable OS
I strongly recommend surfing on the dark web using virtual machine software instead of your locally installed Windows. Why? Because it’s easier to contain malware in a virtual environment, which can be fully controlled.
It’s like in those movies where the doctors are experimenting on deadly viral strains from behind the safety of a glass enclosure. And, as it happens, there are plenty of VMs to choose from: Oracle VM Virtualbox, VMware Fusion and Workstations, QEMU, Red Hat Virtualization, Microsoft Hyper-V, Citrix XenServer, and Xen Project, just to name a few.
Now, if you really want to take the physical storage devices out of the equation, you can use what I like to call a disposable operating system – easy to deploy and to get rid of if you by chance you run into any trouble. All you’ll need is an 8GB thumb drive, an installation package, and a couple of minutes to get things up and running.
Let’s dig in.
How to install Tails OS
Source: TechSpot
Step 1. Get yourself a thumb drive; 8GB will do, but you can buy one with more space if you plan on using it for anything else. Nothing will happen to the stick (probably).
Step 2. Hop on the web and download the installation package for Tails OS.
Note: Tails is a Linux-based live operating system which can be booted from a USB stick or DVD. I recommend using a stick since DVDs have a read-only function after you’re done burning well and accessing the dark web required a bit of writing.
Chill, because nobody will ever find a record of you ever fiddling around the darknet. Note that Tails’ installation package is the .img format, which means that you’ll need software capable of burning images on your thumb drive.
My recommendation is Universal USB Installer, which is very intuitive. You can also go along with Rufus. The choice is yours. For this tutorial, I’ve used Universal.
Step 3. Insert the stick and do a quick format. Be sure to use FAT32 to root out any compatibility issues. It shouldn’t take longer than a few seconds.
Step 4. Download and install Universal USB Installer or Rufus.
Step 5. Fire up Universal USB or Rufus.
Step 6. Under “Step 1: Select a Linux Distribution from the dropdown to put on your USB” select Tails.
Step 7. Under “Step 2: Select your ubuntu*desktop*.iso”, click on the browse button and select the downloaded Tails .img file.
Step 8. Under “Step 3: Select your USB Flash Drive Letter Only”, use the dropdown box to select your thumb drive’s letter. If it doesn’t show up, check the “now showing all drives” option.
Step 9. Review the info and hit Create when you’re done.
Note that the process can take anywhere from 5 to 30 minutes depending on your machine. Sit back, relax, and wait until the installation’s done. When you’re ready, hit the Close button and you’re all set.
Now what? Well, now it’s time to fire up Tails and do a little bit of tinkering.
How to boot from USB and configure Tails
Bogged about your first boot? No worries. It always hurts the first time. Just follow these steps.
- Keep the thumb drive in the USB.
- Restart your computer.
- After the splash screen appears, press the appropriate Boot Menu key. If you’re tired of randomly pressing keys each time you perform this action, check out this article on hotkeys for the boot menu.
- Use your keyboard to select the corresponding drive letter. When you’re done, hit Enter.
- Wait for Tails OS to boot. Since this is the first time, it may take a while. Just be patient.
- Configure Tails and deploy Tor + VPN. Yes, the latest version of The Onion Router has an in-built VPN.
- Get ready to discover the dark and sometimes creepy wonders of the dark web.
3 steps to get on the dark web
So How Do You Get on the Dark Web?
All done installing and configuring Tor? Great! Fire it up and let’s surf. At first glance, Tor doesn’t look that different from your regular browser – it has a search bar, lots of quick-launch icons, the peeled onion icon smack in the middle of the screen. So, now what? Well, let’s start small.
Although content on the dark web is not as ‘indexed’ compared to the one on the clear web, you can still use search engines to find stuff. The Hidden Wiki and Grams are the heavyweights here.
Yay, now I found everything my heart longs for. Not quite: since the dark web relies on privacy and anonymity, search engines like the Wiki and Grams frequently return false results. No matter – good or not, the Hidden Wiki is a great place to start exploring.
The Hidden Wiki & Co.
Think of the Hidden Wiki as Wikipedia’s evil twin – looks more or less the same, but contains links to various dark web categories: editor’s picks, volunteer, introduction points, financial services, commercial services, email/messaging, drugs (yes, it’s the real deal), blogs & essays, hosting providers, hacking services, darknet radio (nothing shady about that; just some weird electronic tunes and, occasionally, a bit of jazz), literature (mostly resources on hacking, both ethical and black hat).
You can also find quick links here to the stuff that makes the dark web pitch-black dark: contract killers, rape, torture, or murder on demand, child pornography.
Fortunately, in Hidden Wiki, every website is followed by a brief description so that the user knows what to expect. My advice to you would be to stick with the editor’s pick. You can also take a look at the blogs & essays section if you want to find some nifty coding resources.
If you’re feeling chatty, you can always access a chat room. Services like Random Chat connects you with random people using the same service. What happens after that, it’s all to you.
You should stay away from everything labeled “porn”, “card skimming services”, “PayPal hacks”, “firearms”, “real fake IDs and passports”. Believe me – there are plenty to go around and each and every one of them are being kept under surveillance. Not to mention the fact that you’ll get exposed to some stuff that will definitely make you take several cold showers.
Hidden Wiki’s not the only search engine online.
Here are a couple of alternatives in case you get bored with Wiki.
- DuckDuckGo – also available on the clear web. The best thing about DuckDuckGo is that it doesn’t track your searches. One can say that it’s the Google of the dark web.
- Torch – considered the first dark web search engine, Torch boasts a database of several million onions links. Works just like Yelp. It even comes with recommendations, although most of them append websites like the infamous Silk Road.
- WWW Virtual Library – if Torch and Hidden Wiki are old, the triple-W Virtual Library is Cthulhu-old; as in the elder god of search engines. What’s even better is the fact the WWW Virtual Library contains info dating back to the beginning of the Internet: logs, documents, pictures, and everything in between.
Fun fact: The Virtual Library was founded and, for a very long time, curated by none other than Tim Berners-Lee, the George Washington of the Internet. So, if you’re looking for obscure Internet facts, very old documents, Berners-Lee’s brainchild is the way to go.
- Uncensored Hidden Wiki – think regular Hidden Wiki is bad? Wait till you see the uncensored version. As the name suggests, it emphasizes very illegal activities like human trafficking, drugs, pornography went wrong, and other things that fester in the dark corners of the human mind.
- ParaZite – do you know the “want to get Lucky?” button in Google’s search engine? The one that takes you on a random clear web site? Well, ParaZite does the same thing. Sure, you can use it like any run-of-the-mill search engine, but if you’re feeling curious, you can also try the “feeling (un)lucky” feature. Proceed with caution and prepare to eject and torch the thumb drive.
- Daniel – Daniel, whomever that may be, is here to guide you through the dark web. It hosts more than 7000 .onion categorized links that you can explore. A built-in feature shows you if a certain dark web site is online, so you don`t have to open and load every one of them to see if it works.
- Comic Book Library – those of you who have a passion for comic books will be thrilled to stumble upon this little dark web corner. Here are literally thousands of comic books about… well quite about anything, that you can download.
Commercial Services
Believe it or not, the dark web even has online shops. And no, they don’t all sell drugs or firearms. Some of them are, reportedly, legit and have great bargains. For instance, if you want to buy a laptop or a smartphone, you can try your luck in one of these shops. Of course, all transactions are anonymous and Bitcoin-driven. Sure, you can use other cryptocurrencies if Bitcoin’s not your cup of tea.
The major issue with these websites is that a whopping 50 percent are fake, and there’s no way of telling for sure if they’ll deliver or not. By the way, most have shipping services.
Of course, you can’t use your home address for dark web drop-offs, but apparently, they can ship all over the world, minus some Middle Eastern countries and North Korea. To tell you the truth, I was tempted into purchasing a Samsung Galaxy S10 Plus; it was only 250 bucks. My advice: look, but don’t touch (buy).
Here are a couple of commercial services you can check out while you’re browsing the dark web:
- CStore – any kind of electronics. You can make purchases in cryptocurrency or gift cards. They even accept full escrow.
- Apple Palace – everything Apple: laptops, desktops, phones, and accessories. All at ludicrously low prices.
- EuroGuns – the name says it all: guns sold on the European market. The website even boasts that it’s the number one European arms dealer.
- Kamagra for Bitcoins – if your boomstick ain’t working no more, you can try Kamagra, which is the dark web and cheap version of Viagra.
- Gold & Diamonds – site offers ‘real’ diamonds and gold. (Un)fortunately, it only ships to Germany and the United States.
- PirateSec – legit hackers, at your service!
- Fake Passports – I think it’s self-explanatory.
- SOL’s United States Citizenship – sells American citizenships; go figure.
- Digital Gangster – the most gangsta way to hack someone’s computer. Apparently, these are Ronin hackers who can be hired for exploits, web hacking, password retrieval, and all-purpose espionage.
- Onion Identity Services – summer discounts for IDs and passports. Bitcoins only.
Email clients
Always remember that the dark web is a people-centric community. So, it’s only natural to find ways to keep in touch with your darknet buddies and/or customers. There are several email and IM services which you can use, and it’s highly recommended to pick one if you want to step up your dark web game.
In terms of functionality, I don’t think there are too many differences between regular IMAP, POP3, and SMT services and the stuff you can use to communicate on the dark web. Let’s start with the email clients.
- secMail – full-fledged email service. Pretty simplistic in design: you can compose, send, and receive emails. All the great things about an email client, minus the tracking, eavesdropping, and other privacy issues.
- RiseUp – this one offers secure emailing services and also comes with a chat option. It doesn`t store communication records and you need to get an invitation code before you can create an account.
- Lelantos – pay-to-use email service. Great security and privacy features, but it has one of the most unreliable and sidetrackable registration forms. Proceed at your own risk.
- Bitmail.la – another pay-to-use email client. Has many features like IMAP, SMTP, and POP3 support, and a 500MB mailbox. Apparently, a lifetime membership costs $0.60.
- Mail2Tor – a free email service which, reportedly, works on both dark and clear web.
- Guerilla Mail – creates a disposable email address.
- AnonInbox – pay-to-use email client. Supports IMAP, SMTP, and POP3; charges around 0.1 BTC per year.
- Protonmail – has both paid and free subscriptions. Boasts the browser-encrypted email technology.
Dark Web Chat/Social Networks
Right. Let’s now talk about social media and instant messaging. Believe it or not, Zuckerberg’s Facebook has a darknet version. People mostly use it for covert communication, anonymous tips submission, and stuff like that.
Sure, it’s not as secure as the clear web version, but it’s there and totally legal to use. Hidden Facebook is hardly the only social media client on the dark web. Check out the list below for the ‘hottest’ dark web clients.

- BlackBook – works pretty much the same way as Facebook: you can chat, send pictures and friend requests, post status updates, and join groups. Though competing head-to-head with Facebook Onion, BlackBook’s prone to hacking. Reportedly, the client was disabled at least a couple of times in 2018.
- Torbook – very similar to BlackBook. Some claim that both of them rose at around the same time, despite the creators not knowing each other.
- The Campfire – gather around the campfire, folks to hear the tale of tales. The name’s rather suggestive – a big chatroom; everybody can join, and the topics can be anything from the latest trends in the music industry to how you can hide a human body.
- Lucky Eddie’s Home – scripted chat room that sports one of the most efficient file-uploading system on the dark web. Just like any IM app, you can send or receive messages, join or create groups, and send files.
- MadIRC Chat Server – if you’re over 30, you certainly remember the mIRC era. Surprisingly enough, IRC off-spins are still being used today, mostly for covert conversations or intranet communication. MadIRC Chat works just like a regular IRC – no or subscription required. Just pick a username and join in on the fun. I know sharing is caring, but in this case, I would advise you not to share any personal details because you may never know who’s on the other side of the line.
- Chat with strangers – think Omegle, but on the dark web. Just fire up the client, connect to a chat room, and that’s it. You can’t send or receive files. Still, if you’re lucky, perhaps you can partake in a scintillating conversation.
Journalism and Advocacy Groups
As I’ve mentioned, the dark web isn’t just a place of eternal torment, teeming with drug dealers, human traffickers, and a hitman. It’s also used by journalists, advocacy group members, and political refugees in hiding. Reuters, Fox, NBC, CNN – all of them keep open dark web channels to receive anonymous tips from whistleblowers.
Advocacy groups are also reaping the advantages of the darknet because, here, the term of censorship is as popular as HTTPS. And finally, we have political outcasts, refugees, and people who want to get in touch with the outside world, being from a totalitarian country that suppresses all means of communication and information.
Of course, there are your run-of-the-mill congregations, which will worship anything from Lucifer to the Flying Spaghetti Monster.
If you’re interested in subversive journalism, here are a couple of sites you can try visiting:
- Soylent News – a trans spectrum darknet news aggregator. Features webmaster-moderated forums on which you can submit comments. You can also get involved by either submitting tips or writing news.
- ProPublica – historically, ProPublica’s the first major news outlet to feature well, a darknet outlet. With an activity spanning almost four years, ProPublica managed to expose power abuses and blow the lid on covert activities conducted by governmental institutions. Although quite young compared to other darknet news outlets, ProPublica’s work was rewarded with five Pulitzer Prizes for Feature Writing. The last one was awarded to Hannah Dreier, the investigative journalist who covered the gangs of Los Angeles.
- BBC Tor Mirror – In March 2022, after invading Ukraine, Russia removed BBC World News from broadcast. On the list of censored media services were also Deutsche Welle, Radio Free Europe/Radio Liberty, and Voice of America. Allegedly, the giant media companies were ”spreading false information about war in Ukraine”. But for the moment, you can still get a hint of what`s going on around the world (and Putin doesn`t appprove) via BBC Tor Mirror. If you live or travel in a country that frowns upon freedom of speech and insists on naming a war a „special military operation”, there`s your breath of fresh air.
More on How to Stay Safe on the Dark Web
We already went through VPNs, anonymizing web browsers, and disposable operating systems, so I won’t bother reminding you about those.
Here are some other things you can try to bolster your security:
1. Minimize or rescale your Tor browsing window
Sounds rather off, doesn’t it? Well, there’s a reason why it’s recommended to browse with a minimized or rescaled window – you can be tracked based on your active window’s dimensions (yeah, they really can do that). So, do yourself a favor and rescale that Tor window as much as you can before proceeding.
2. Tweak the security settings
Tor has an in-build slider which lets you adjust the level of security. Just click on the onion icon and choose Security Settings. Adjust the slider until the cursor points to the safest. This means that the JavaScript will be disabled by default on every website and some symbols and images will not be displayed.
3. Never use your credit and debit card for purchases
I’ll go further than that and say stay away from darknet shops. Maybe some of them are legit, but are you really willing to take that chance? Still, if you’re really itching to purchase a new phone or God knows whatever, I would advise you to stick with Bitcoins or your favorite crypto coin. Using credit or debit cards for this sort of thing is like painting a big bullseye on your bank account while yelling: “come here and take my money.”
4. Close Tails after finishing your session
When you’re done surfing or shopping on the dark web, don’t forget to shut down Tails. The major advantage of using a live OS such as Tails is that, on shut down, the OS wipes itself from the thumb drive you’ve installed it. That’s why it’s never a good idea to burn Tails on DVD.
5. Don’t stick your nose where it doesn’t belong
Great life advice, but it’s even more valuable where the darknet is concerned. Keep in mind that many criminal organizations use the dark web to communicate or sell merchandise. Some of these channels are under watch. You may very well end up in the middle of a stakeout that could turn ugly. So, if the website looks fishy, close the tab, and forget about it.
If in need for help, ask. We`re here for you with our Heimdal® Threat Prevention Home solution.
Wrap Up
This is where I get off – been a long journey and I hope I’ve managed to at least change your perspective on the dark web. So, to wrap it up nice and tight, remember to take all the necessary precautions. Don`t use your debit or credit card, stay away from dubious groups, and have fun while you’re at it. As always, for comments, rants, ad-libs, or beer donations, shoot me a comment. Cheers!
And if you liked this article, follow us on LinkedIn, Twitter, Facebook, and YouTube for more cybersecurity news and topics.


 Network Security
Network Security
 Vulnerability Management
Vulnerability Management
 Privileged Access Management
Privileged Access Management
 Endpoint Security
Endpoint Security
 Threat Hunting
Threat Hunting
 Unified Endpoint Management
Unified Endpoint Management
 Email & Collaboration Security
Email & Collaboration Security









