Contents:
Before I tell you how to DDoS someone, I want to make a few issues clear. Launching a Distributed Denial of Service attack for any other reason than security testing is illegal.
In ethical hacking, DDoS attacks can be used as part of security testing and vulnerability assessment activities. If that is the case, make sure that strict guidelines and legal agreements are in place before you get to work.
You will need the explicit consent of the organization being tested, and you should be able to control the attack carefully, to avoid causing real harm. Unauthorized DDoS attacks are illegal and can result in serious legal consequences.
What Is a DDoS Attack?
A DDoS attack is a denial of service (DoS) attack that uses a botnet to flood the target with malicious traffic.
Hackers launch DDoS attacks to disrupt or put down a website or service. They achieve this by sending the web server more requests than the target website can process. Because of DDoS attacks, an organization’s users will either:
- not be able to access the information they need anymore,
- will have to deal with a very slow-working application.
While DoS attacks use only one source to send the information, a DDoS attack uses thousands, or hundreds of thousands of infected devices to flood its target. Thus, DDoS attacks hit harder than DoS ones.
The Purpose of a DDoS Attack
Threat actors use DDoS attacks for various purposes. Unlike in ransomware attacks’ case, there are no fast-financial gains expected when planning a DDoS attack. However, it might happen that hackers try to extort a company by using DDoS as a weapon. Here below are the reasons why hackers launch DDoS attacks:
DDoS as an Obfuscation Technique
In many cases, hackers use DDoS attacks as smokescreens. By putting the target’s web server down, they try to hide the real endgame: malware deployment or data exfiltration.

Source – New DDoS Attacks Waves
Putting down competitors
Cybercriminals might use DDoS attacks as a blunt weapon against competitors. For instance, they might want to bring down a site hosting a cybersecurity tool or bring down a small online shop operating in the same niche.
Extortion attempts
Malicious actors sometimes ask their victims to pay a fee in order for the distributed denial of service to stop.
Hacktivism
Hacktivists are activists that use cybercrime as a protest tool. DDoS attacks are cheap, and relatively easy to pull off, since there are plenty of free DDoS tools available. So, they became a favorite way for certain activism groups to make a point. Their goal is to disrupt online services and websites belonging to target organizations in order to draw attention.
Hacktivists use DDoS attacks also because they can launch them anonymously, so authorities will have a hard time finding out who did it.
Not all hacktivists fight for a good cause. State-supported hackers, like pro-Russia KillNet threat group, use DDoS attacks to disrupt other governments’ activities. Like targeting healthcare organizations.
Fun and glory
Sometimes, the attacker might not even have a motive. He just does it for the “giggles”, seeking to test his abilities or just to cause mayhem. So, no matter how small and allegedly insignificant an organization seems, there is a possibility that hackers target it in a DDoS attack. This means that all CIOs or CTOs of a company should take the appropriate security measures to avoid a DDoS attack.
System Testing
In red teaming exercises, ethical hackers simulate real-world attack scenarios, to assess an organization’s overall security posture. These may include DDoS attacks. The activity can be part of a broader set of tactics to evaluate how well an organization can defend against multiple attack vectors.
Ethical hackers use controlled and limited DDoS attacks to test a system’s resilience and ability to handle a sudden influx of traffic. This helps them identify weaknesses in the infrastructure:
- inadequate network bandwidth,
- poorly configured load balancers,
- insufficient server resources.
How to DDoS Someone
There’s more than one way of carrying out a denial-of-service attack. Some methods are easier to execute than others, but not as powerful. Sometimes, the attacker might want to go the extra mile, to really be sure the victim gets the message, so he can hire a dedicated botnet to carry out the attack.
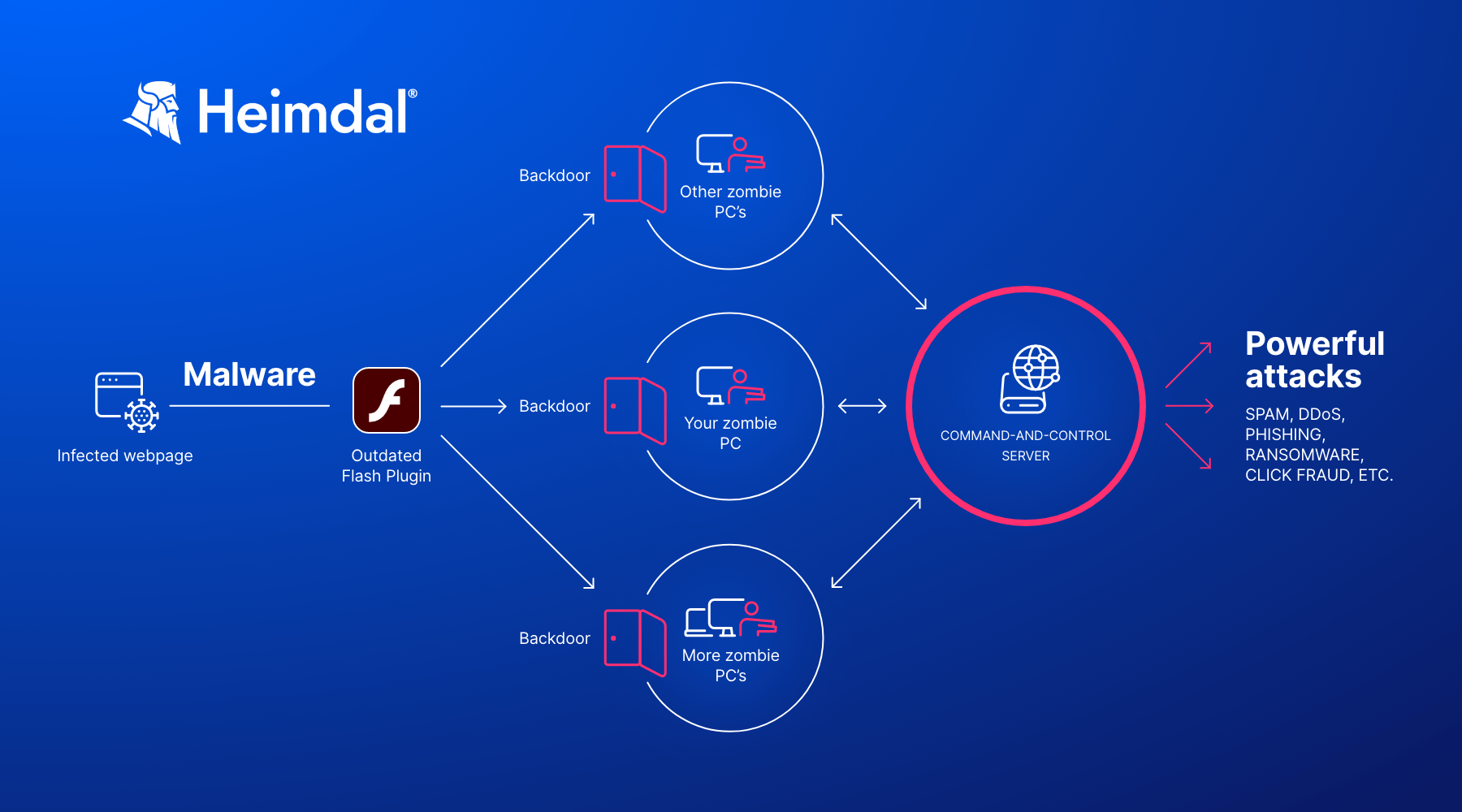
Botnets
A botnet is a collection of computers or other Internet-connected devices that have been infected with malware, and now respond to the orders and commands of a central computer, called the Command-and-Control Center.
The big botnets have a web of millions of devices, and most of the owners have no clue their machines are compromised. Besides multiple computers, a botnet can also include IoT devices.
Usually, botnets are used for a wide variety of illegal activities, such as pushing out spam emails, phishing or cryptocurrency mining.
Some, however, are available to rent for the highest bidder, who can use them in whatever way seems fit. Oftentimes, this means a DDoS attack. Read more about how to protect your business against botnet attacks in my colleague’s article.
DDoS programs and tools
Small scale hackers who don’t have access to botnets, have to rely on their own computers. This means using specialized DDoS attack tools, that can direct Internet traffic to a certain target.
Of course, the amount of traffic an individual computer can send is small, but crowdsource a few hundreds or thousands of users, and things suddenly grow in scope.
This particular Distributed Denial of Service tactic has been successfully employed by Anonymous. In short, they send a call to their followers, asking them to download a particular tool, and be active on messaging boards, such as IRC, at a particular time. They then simultaneously launch a DDoS attack, bringing the target website or service down.
Here’s a sample list of DDoS attack tools that malicious hackers use to carry out denial of service attacks:
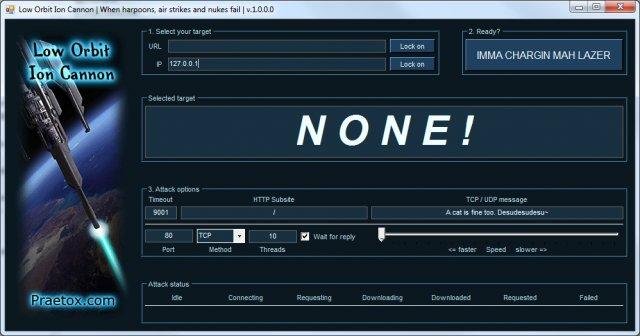
- Low Orbit Ion Cannon, shortened to LOIC.
- XOIC.
- HULK (HTTP Unbearable Load King).
- DDOSIM – Layer 7 DDoS Simulator
- R-U-Dead-Yet.
- Tor’s Hammer.
The HTTP/2 Rapid Reset Vulnerability
The HTTP/2 Rapid Reset attack takes advantage of a vulnerability of the protocol. Researchers discovered it in October 2023, but hackers had been exploiting it as a zero-day since August.
CVE-2023-44487 allows hackers to cancel requests immediately after sending them. Consequently, the server will start processing each request only to quickly have them canceled.
So, what the attackers do to disrupt servers is open and cancel many request streams within a single connection. CVE-2023-44487 is in fact a key feature of the HTTP/2 protocol, that differentiated it and made it a progress from old HTTP1. The multiplexing feature makes HTTP/2 faster and more efficient by sending multiple streams of data through a single TCP connection. On the other hand, this is also a vulnerability, when hackers use it.
This DDoS attack method forces the server to do a lot of work for each canceled request. However, it is very easy and light on resource consumption for the attacker. The impact is huge. One of the largest HTTP/2 Rapid Reset DDoS attacks exceeded 398 million requests/second.
With HTTP/2 Rapid Reset you don’t need a huge botnet anymore to inflict as much damage. You can only use 30 or 40% of the botnet you usually needed to run a DDoS with a certain impact.
Read the whole interview with cybersecurity expert Robertino Matausch to get a comprehensive perspective over the HTTP/2 Rapid Reset DDoS attack method.
How to DDoS an IP using cmd
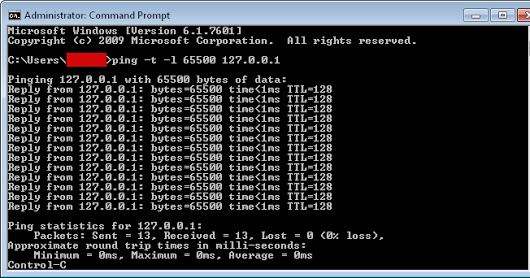
One of the most basic and rudimentary denial-of-service methods is called the “ping of death” and uses the Command Prompt to flood an Internet Protocol address with data packets.
Because of its small scale and basic nature, ping of death attacks usually works best against smaller targets. For instance, the attacker can target:
- A single computer. However, in order for this to be successful, the malicious actor must first find out the IP address of the device.
- A wireless router. Flooding the router with data packets will prevent it from sending out Internet traffic to all other devices connected to it. In effect, this cuts the Internet access of any device that used the router.
In order to launch a ping denial-of-service attack, the malicious hacker first needs to find out the IP of the victim’s computer or device. This is a relatively straightforward task, however.
A ping of death is small in scale, and fairly basic, so it is mostly efficient against particular devices. Nevertheless, if multiple computers come together, it’s possible to bring down a smallish website that doesn’t have the proper infrastructure to deal with this threat.
Using Google Spreadsheet to send countless requests.
An attacker can use Google Spreadsheets to continuously ask the victim’s website to provide an image or PDF stored in the cache. Using a script, he will create a neverending loop, where the Google Spreadsheet constantly asks the website to fetch the image.
This huge number of requests overwhelms the site and blocks legitimate traffic.
Unlike other denial-of-service tactics, this one doesn’t send large information packages to flood the website, but instead, it makes data requests, which are much, much smaller.
In other words, the attacker doesn’t need to rely on sizeable botnet or thousands of other users to achieve a similar effect.
Teardrop attacks
In most cases, the information transmitted between a client device and the server is too big to be sent in one piece. Because of this, the data is broken into smaller packets, and then reassembled again once it reaches the server.
The server knows the order of reassembly through a parameter called “offset”. Think of it as instructions to building a LEGO toy.
What a teardrop attack does, is to send data packets at the server that make no sense and have overlapping or dysfunctional offset parameters. The server tries, and fails, to order the data according to the malicious offset parameters. This quickly consumes available resources until it grinds to a halt, taking down the website with it.
Amplifying a DDoS attack
To maximize every data byte, malicious hackers will sometimes amplify the flood by using a DNS reflection attack.
This is a multiple-step process:
- The attacker will assume the identity of the victim by forging its IP address.
- Using the forged identity, he will then send out countless DNS queries to an open DNS resolver.
- The DNS resolver processes each query, and then sends the information back to victim device who had its identity stolen. However, the information packets the DNS resolver sends out are much bigger than the queries it receives.
What happens during amplification is that every 1 byte of information becomes 30 or 40 bytes, sometimes even more. Amplify this further using a botnet with a few thousand computers, and you can end up sending 100 gigabytes of DDoS traffic towards a site.
The types of DDoS attacks
Denial-of-Service attacks fall in two broad categories, depending on their main attack vector:
- Application layer.
- Network layer.
Network layer attacks
A network layer attack works by flooding the infrastructure used to host a website with vast amounts of data.
Many providers nowadays claim they offer “unmetered” bandwidth, meaning you should theoretically never have to worry about excessive amounts of traffic taking down your site. However, this “unmetered” bandwidth comes with strings attached.
To put things into perspective, a website with some 15,000 monthly pageviews and hundreds of pages requires around 50 gigabytes of monthly bandwidth to operate optimally. Keep in mind that this traffic is widely dispersed over the course of an entire month. A site like this has no chance to stay online if a DDoS attack rams it with 30 or 40 gigs of traffic in a one-hour period.
As a self-defense measure, the hosting provider itself will simply cut off hosting you until the legitimate traffic normalizes. Although this might seem harsh, this prevents spill-over effects that might affect other clients of the hosting provider.
These kind of DDoS attacks themselves come in multiple shapes and sizes. Here are a few of the more frequent ones:
- SYN Attacks. SYN is a shorthand for “synchronize”, and is a message that a client (such as a PC) sends to the web server for the two to be in sync.
- DNS reflecting.
- UDP amplification attacks.
Application layer attack
Application layer attacks are much more surgical in nature compared to network ones. These work by targeting certain programs or software that a website uses in its day-to-day functioning.
For instance, an application layer attack will target a site’s WordPress installation, PHP scripts or database communication.
This type of software can’t handle anywhere near the load of wider network infrastructure, so even a comparatively small DDoS attack of a few megabytes per second can take it down.
HTTP flood activities are typical application layer attacks. They work by abusing one of two commands, POST or GET. The GET command is a simple one that recovers static content, like the web page itself or an image on it.
The POST command is more resource-intensive, since it triggers complex background processes with a greater impact on server performance.
An HTTP flood will generate a huge amount of internal server requests that the application cannot handle, so it then flops and takes down the entire site with it.
How to Detect a DDoS Attack?
Analyze the traffic to see if you’re confronting a usage spike or an attack.
Traffic spikes are a frequent occurrence and can actually be big enough to take down poorly prepared websites. A site designed to cope with an average of 30-40 concurrent users will come under strain if a spike brings up the number to 600-700 users at the same time.
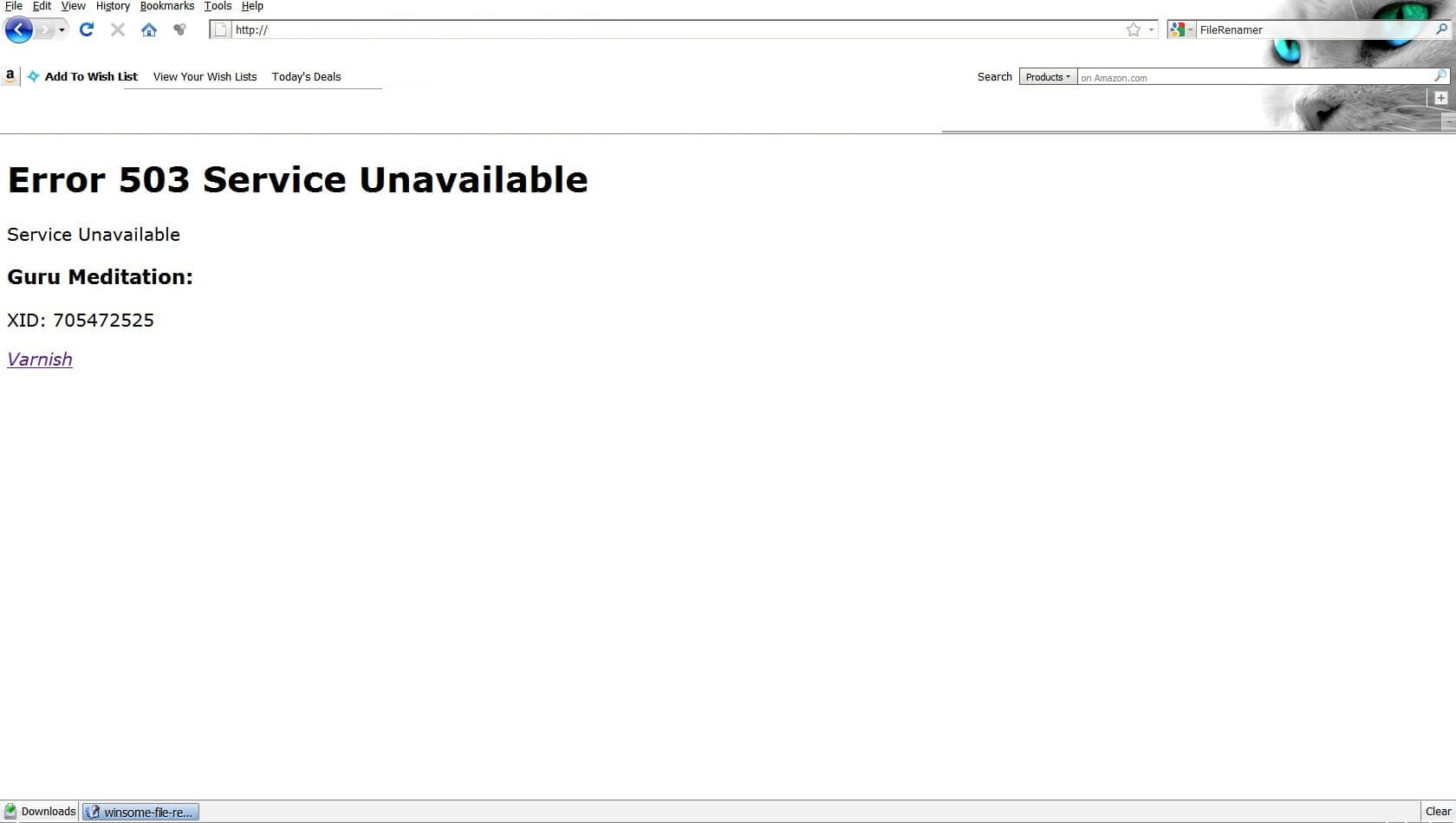
The first sign of a DDoS attack is a strong slowdown in server performance or an outright crash. 503 “Service Unavailable” errors should start around this time. Even if the server doesn’t crash, critical processes that used to take seconds to complete now take minutes.
Wireshark is a great tool to help you figure out if what you’re going through is a DDoS. Among its many features, it monitors what IP addresses connect to your PC or server, and how many packets it sends.
Of course, if the attacker uses a VPN or a botnet, you’ll see a whole bunch of IPs, instead of a single one. Here’s a more in-depth rundown on how to use Wireshark to figure out if you’re on the wrong end of a denial-of-service.
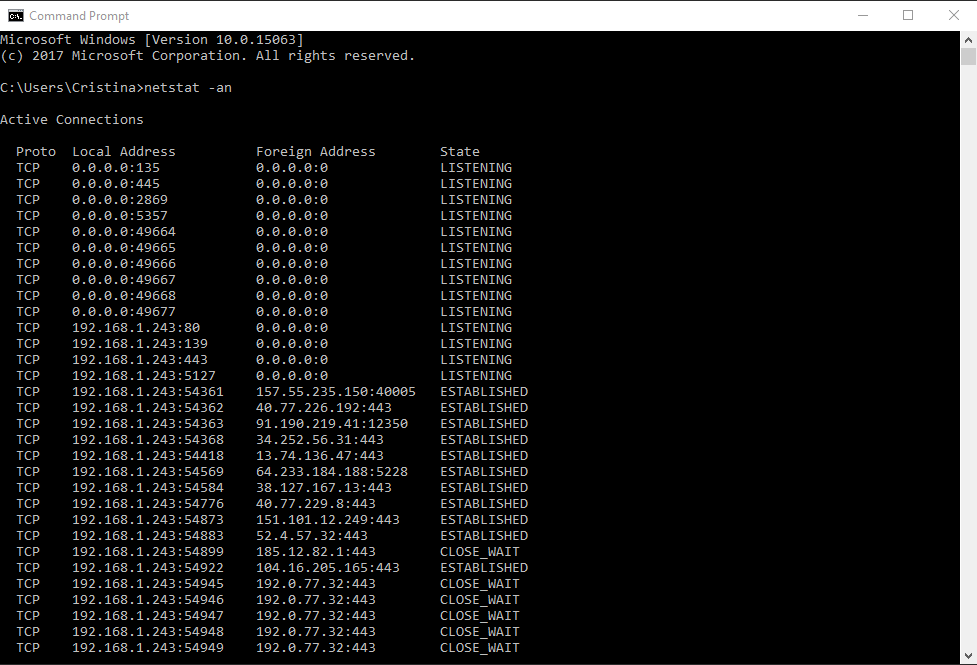
Microsoft Windows also comes with a native tool called Netstat, which shows you what devices are connecting to your web servers, and other similar statistics.
To open the tool, write cmd in the Start menu search bar, and then type in netstat –an. This will take you to a screen showing your own internal IP in the left-hand column, while the right-hand column holds all of the external IPs connected to your device.
The screenshot above is for a normal connection. In it, you can see a few other IPs that communicate normally with the device.
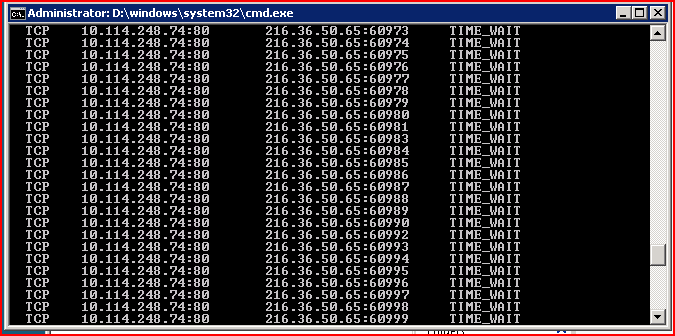
Now, here’s how a DDoS attack would look like:
On the right side, you can see that a single external IP repeatedly tries to connect to your device. While not always indicative of a DDoS, this is a sign that something fishy is going, and warrants further investigation.
Conclusion
DDoS attacks will only get more frequent as script kiddies get access to more sophisticated and cheap DDoS tools and attack methods. Fortunately, denial-of-service attacks are short-lived affairs, and tend to have a short-term impact. Of course, this isn’t always the case, so it’s best to be prepared for the worst-case scenario.
If you liked this article, follow us on LinkedIn, Twitter, Facebook, and Youtube, for more cybersecurity news and topics.

Heimdal® Network DNS Security
- No need to deploy it on your endpoints;
- Protects any entry point into the organization, including BYODs;
- Stops even hidden threats using AI and your network traffic log;
- Complete DNS, HTTP and HTTPs protection, HIPS and HIDS;










 Network Security
Network Security
 Vulnerability Management
Vulnerability Management
 Privileged Access Management
Privileged Access Management  Endpoint Security
Endpoint Security
 Threat Hunting
Threat Hunting
 Unified Endpoint Management
Unified Endpoint Management
 Email & Collaboration Security
Email & Collaboration Security



 Source
Source



