Contents:
Cyber crooks have come up with a new way to infect your computer with financial and banking malware.
The process starts by randomly sending users spam emails disguised as a payment confirmation email from Delta Air.
The choice to mask the email as coming from an airline wasn’t random, since many this time of year is when many consumers purchase flight tickets at discounted rates for the summer.
This phishing email has a couple of tell-tale signs that it’s fake:
- The email address isn’t legitimate, it should end with “@delta.com” not “@deltaa”.
- No information about the flight. An airline confirmation email usually contains some information about the flight you just booked. This email has no such thing, in order to increase your curiosity and push you into clicking the link.
- The visual format is different from Delta’s usual emails.
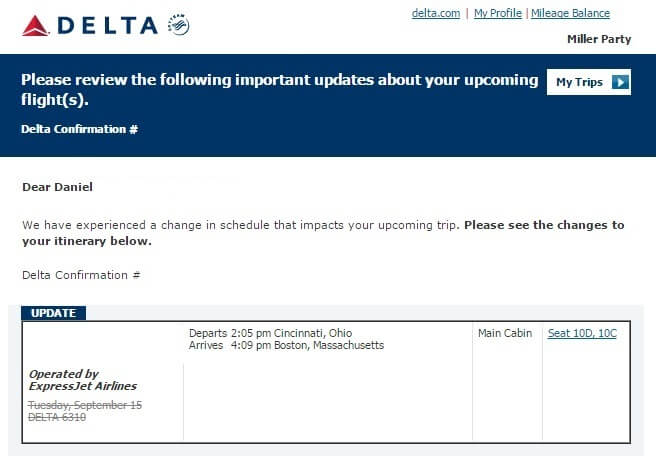
For example, here is how a legitimate email from Delta looks like:
However, no transaction actually took place! The email is designed to scare you into thinking someone bought an airplane ticket using your identity. You then panic and click on one of the links in the email in order to figure out how someone could do an unauthorized purchase with your credentials.
The links then redirect you to several compromised websites, which host Word documents infected with the Hancitor malware.
Hancitor is a versatile malware frequently used in phishing attacks that specializes initially infecting a PC, and then acting as a bridge for further malware downloads.
If you download the malicious Word document and open it, then Hancitor will activate and infect legitimate system processes in your PC using a PowerShell code. Afterwards, your PC will connect to one or more malicious Command and Control (C&C) servers.
These C&C servers will then download additional malware on your PC, which belong to the Pony family.
Pony malware is specifically designed to steal sensitive information such as passwords and usernames from VPNs, web browsers, FTP, messaging apps and many more.
On top of that, the C&C servers also download and spread another Pony-based malware called Zloader. Unlike Pony, Zloader is a banking malware designed to clean up your bank account and steal financial information.
Once the information harvesting is complete, the malware connects to another set of C&C servers and sends them all of your credentials and financial information.
For a more detailed guide on how to protect yourself from financial and banking malware, we recommend you check out our in-depth financial protection guide.
Stay safe!


 Network Security
Network Security
 Vulnerability Management
Vulnerability Management
 Privileged Access Management
Privileged Access Management
 Endpoint Security
Endpoint Security
 Threat Hunting
Threat Hunting
 Unified Endpoint Management
Unified Endpoint Management
 Email & Collaboration Security
Email & Collaboration Security