Contents:
A new technique for spreading QBot malware gained popularity among hackers – they are now distributing it through SVG files to perform HTML smuggling, which locally generates a malicious installer for Windows.
In this attack, the target’s browser is tricked into downloading a Base64 encoded version of the QBot malware installer hidden within an SVG file.
Qbot or ‘QakBot’ is a Windows malware that usually arrives through a phishing email that delivers other payloads such as Cobalt Strike, Brute Ratel, and ransomware.
HTML Smuggling via SVG
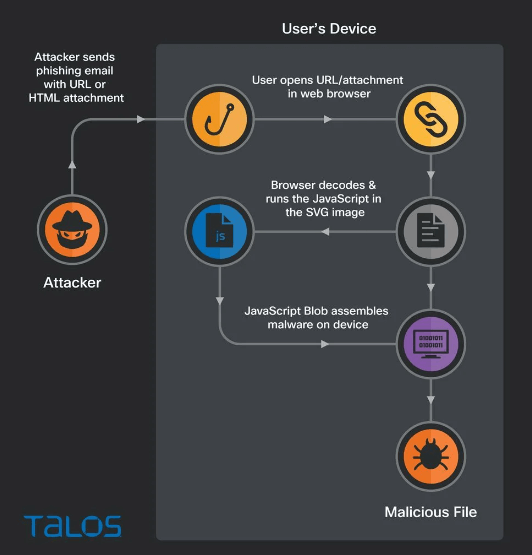
HTML smuggling is a method of “smuggling” encoded JavaScript payloads inside an HTML attachment or website. When the HTML document is opened, the JavaScript is decoded and executed, allowing the script to perform malicious behavior locally, including the creation of malware executables, explains Bleeping Computer.
Threat actors can use this strategy to evade security measures and firewalls that monitor for malicious files at the perimeter.
Cisco Talos researchers discovered a new QBot phishing campaign that begins with a stolen reply-chain email that prompts the user to open an attached HTML file. The malicious code in this attachment is snuck in through an HTML smuggling technique that embeds a scalable vector graphics (SVG) picture that is base64 encoded.
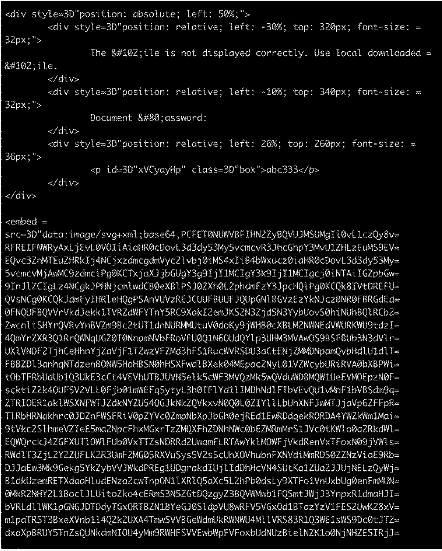
As opposed to raster image formats like JPG and PNG, SVGs are XML-based vector images that can legitimately include HTML <script> tags. When an SVG file is loaded into an HTML document using an <embed> or <iframe> tag, the image is rendered and the JavaScript is executed.
According to the analysts, the SVG blob contains JavaScript code that, once deciphered, turns the JS variable “text” to a binary blob and then to a ZIP archive.
In this case, the JavaScript smuggled inside of the SVG image contains the entire malicious zip archive, and the malware is then assembled by the JavaScript directly on the end user’s device.
Because the malware payload is constructed directly on the victim’s machine and isn’t transmitted over the network, this HTML smuggling technique can bypass detection by security devices designed to filter malicious content in transit.
If the file is opened, an ISO is extracted on the victim’s computer, which then executes the standard “ISO → LNK → CMD → DLL” infection.
It is speculated that the use of an SVG file to conceal malicious code inside an HTML attachment helps further obfuscate the payload and raises the chances of evading detection.
QBot used a Windows vulnerability to evade Mark of the Web security warnings; however, Microsoft addressed this earlier this week with the December 2022 patch.
If you liked this article, follow us on LinkedIn, Twitter, Facebook, Youtube, and Instagram for more cybersecurity news and topics.


 Network Security
Network Security
 Vulnerability Management
Vulnerability Management
 Privileged Access Management
Privileged Access Management
 Endpoint Security
Endpoint Security
 Threat Hunting
Threat Hunting
 Unified Endpoint Management
Unified Endpoint Management
 Email & Collaboration Security
Email & Collaboration Security










