Contents:
Hackers are making use of stolen reply-chain emails in a wave of phishing attacks targeting Ikea’s employees.
Reply-Chain Email Cyberattacks Targeting Ikea
According to BleepingComputer publication, the company has started to inform its employees in a set of internal emails of these new reply chain phishing attacks that have the internal Ikea mailboxes as targets. According to the company’s emails towards employees, it seems that these are filled with seven digits links. The Ikea’s IT team also advised employees to not open the emails and to report them right off to the IT department.
There is no confirmation for the moment if internal servers were compromised.
There is an ongoing cyber-attack that is targeting Inter IKEA mailboxes. Other IKEA organizations, suppliers, and business partners are compromised by the same attack and are further spreading malicious emails to persons in Inter IKEA. (…)This means that the attack can come via email from someone that you work with, from any external organization, and as a reply to an already ongoing conversation. It is therefore difficult to detect, for which we ask you to be extra cautious.
BleepingComputer also mentions that the publication managed to identify the Ikea cyberattack relating this with the URL that can be found in the body of the emails. It seems that if somebody clicks on the provided URL, they will be directed to perform a ‘charts.zip’ file downloading. Inside this zip file, there is a compromised Excel document. In order to view it, users should activate the option ‘Enable Content’ or ‘Enable Editing’. Clicking on these buttons will only lead to the execution of malicious macros. These macros have the role to download from a remote site several files dubbed ‘bestb.ocx’, ‘besta.ocx,’ or ‘bestc.ocx’ and then these will be saved to C:\Datop folder.
The OCX files are basically deprecated ActiveX Controls that are renamed and the malware payload installation happens after these are executed by means of the command regsvr32.exe. The publication also mentions that campaigns employing the Qbot trojan and also maybe Emotet have used the same method as it’s used now in this Ikea phishing campaign.
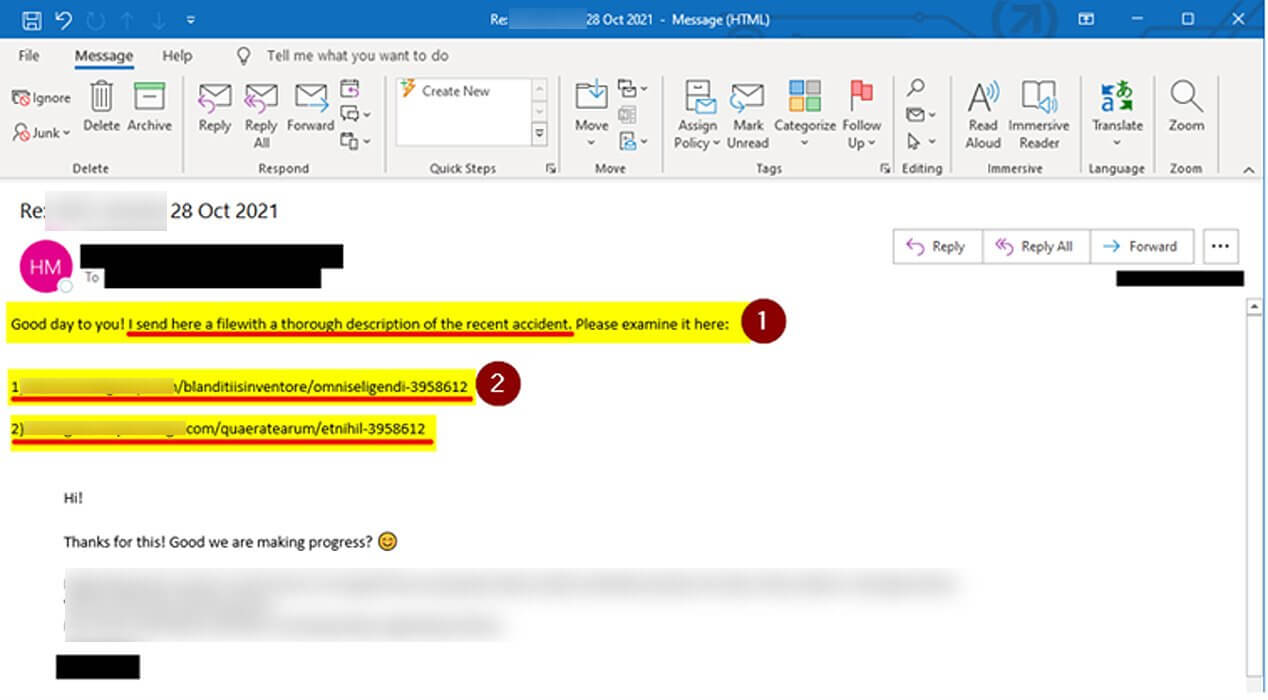
What Is a Reply-Chain Attack?
In these types of cyberattacks, cybercriminals usually perform theft of legitimate corporate emails. What follows next is that they reply to these emails with messages that contain compromised links. When this link is opened, the malware is deployed on the host device. These are legitimate e-mails from an organization so the recipients won’t doubt their trustworthiness, making them an efficient phishing scheme.
How Can Heimdal™ Protect You?
Heimdal™ has always the most efficient solutions ready to help secure your organization’s critical infrastructure. You can use tools like Email Security and Email Fraud Prevention. The first protects against mail-delivered threats and supply chain attacks by means of a combination of proprietary e-mail threat prevention and Office 365 support, the second keeps Business Email Compromise (BEC), CEO fraud, and phishing away through its 125 vectors of analysis.
Did you enjoy this article? Follow us on LinkedIn, Twitter, Facebook, Youtube, or Instagram to keep up to date with everything we post!


 Network Security
Network Security
 Vulnerability Management
Vulnerability Management
 Privileged Access Management
Privileged Access Management
 Endpoint Security
Endpoint Security
 Threat Hunting
Threat Hunting
 Unified Endpoint Management
Unified Endpoint Management
 Email & Collaboration Security
Email & Collaboration Security










