Contents:
GravityRAT, a Remote Access Trojan, is being spread in the wild once more, this time disguised as SoSafe Chat, an end-to-end encrypted chat application.
GravityRAT is a spyware-type of malware that enables threat actors to steal data from compromised machines. The malware’s developers target users of Windows, Mac OS X, and Android.
The trojan has been actively developed by what appears to be Pakistani cybercrime organizations since at least 2015, and it has been used in targeted operations against Indian military entities.
The most recent operation’s telemetry statistics reveal that the targeting extent hasn’t changed, and the RAT is still targeting high-profile people in India, such as officers in the Armed Forces.
Posing as a Chat App
The spyware was originally targeting users through an Android app called ‘Travel Mate Pro,’ but because traveling became challenging because of the pandemic, the cybercriminals had to adapt to the new situation.
The application is now known as ‘SoSafe Chat,’ and it is advertised as a safe messaging app having end-to-end encryption.
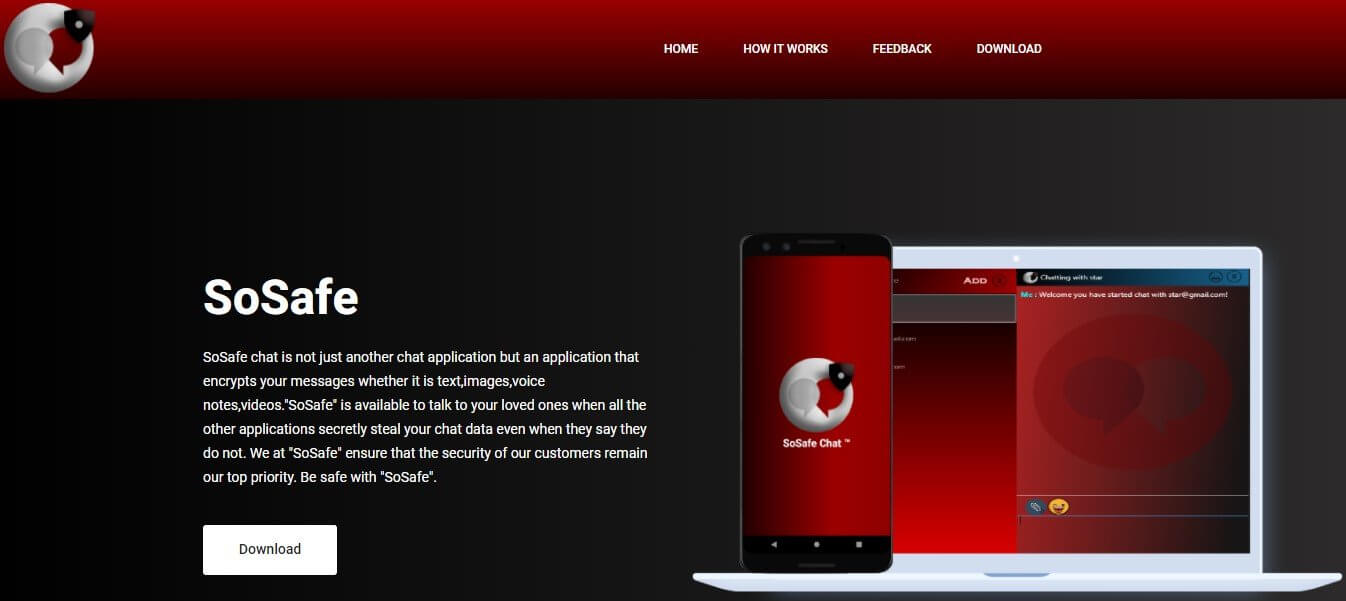
The website that probably helped spread the application (sosafe.co[.]in) is still up and running, but the download link and registration form are no longer functional.
The distribution process is not known at the moment, although it was most likely accomplished by driving traffic to the site via malvertising, social media posts, and instant messages sent to victims.
GravityRAT Capabilities
GravityRAT may execute a variety of malicious actions as soon as it is deployed on a user’s machine, enabling cybercriminals to steal data, monitor the target, and track their location.
Researches showed that this spyware can steal device information, email addresses, phone and SMS records, and contact lists before delivering them to a hacker-controlled Command and Control (C&C) server.
It can also find and transfer files with the following extensions to the C&C server:.jpg,.jpeg,.log,.png,.txt,.pdf,.xml,.doc,.xls.
As explained by BleepingComputer, the list of permissions that the trojan requests for this functionality is naturally quite extensive, but it may appear justified for an IM app.
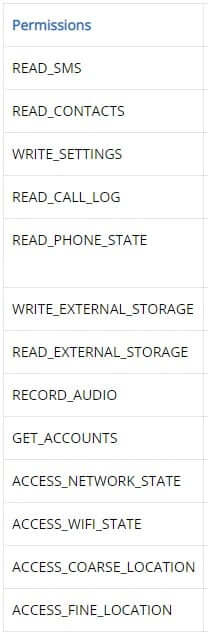
Compared to the previous version, GravityRAT has included the ability to capture audio and mobile-specific functionality such as location fetching and cellular network data exfiltration.
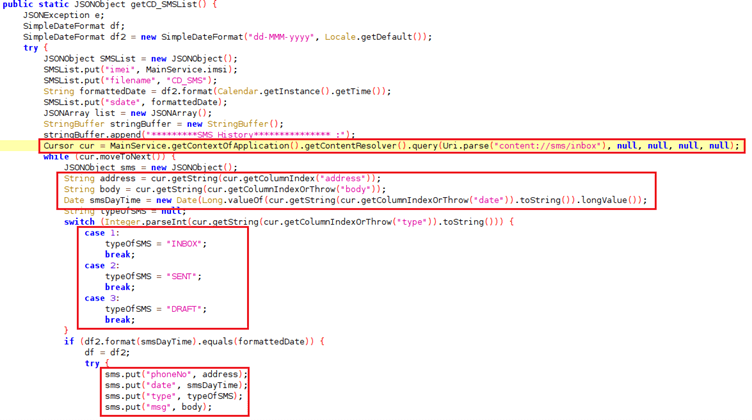
Prior to the 2020 version, GravityRAT could only affect Windows devices, mobile devices being safe from this malware.
The malware’s reappearance, this time targeting mobile devices, shows that its creators are still working on it.
If you liked this article, follow us on LinkedIn, Twitter, Facebook, Youtube, and Instagram for more cybersecurity news and topics.


 Network Security
Network Security
 Vulnerability Management
Vulnerability Management
 Privileged Access Management
Privileged Access Management
 Endpoint Security
Endpoint Security
 Threat Hunting
Threat Hunting
 Unified Endpoint Management
Unified Endpoint Management
 Email & Collaboration Security
Email & Collaboration Security