Contents:
During the journey of protecting our Heimdal users, we’ve seen plenty of ways in which they can get malware infections.
From movies to fishy Kodi repositories and uTorrent spreading malvertising, they have one thing in common: online piracy.
It’s a very scary name for a very basic desire: go home, relax, watch your TV show and recharge for a new workday.
With the rise of paid subscriptions like Netflix, Hulu or Amazon and the veritable cornucopia of award-winning TV content, more and more online users turn to piracy in order to keep up with that content (and not break the bank by doing so!).
Unfortunately, this means they turn to google “watch free movies”.
Then, they end up on domains like “fmovies”, “popcorntime” or “putlocker” with ever-changing extensions and their PC gets exposed to malware that would make any Antivirus do a triple take (if the software even detects that infection!).
According to the latest research, the more time a user spends on a piracy site the higher are the chances to get a malware infection.
Here’s what Rahul Telang from Carnegie Mellon University found out, after tracking more than 250 users for over a year:
“In particular, we estimate that doubling the time spent on infringing sites leads to 20 percent increase in total malware files and 20 percent increase in malware files after removing potential adware. We also find no evidence that users who visit infringing sites more take more precautions. In particular, users visiting infringing sites are less (not more) likely to install an antivirus (AV) software.”
The fact that users don’t rely on antivirus to keep them fully safe is not new, especially because the reactive nature of antivirus makes it very difficult to detect and fight against new malware.
However, I was curious to see what kind of pirate-related domains Heimdal™ Threat Prevention blocked before the compromised traffic could reach your PC.
I’ll tell you, it was a long list with more than 200.000 domains. Here are a couple of keywords I investigated.
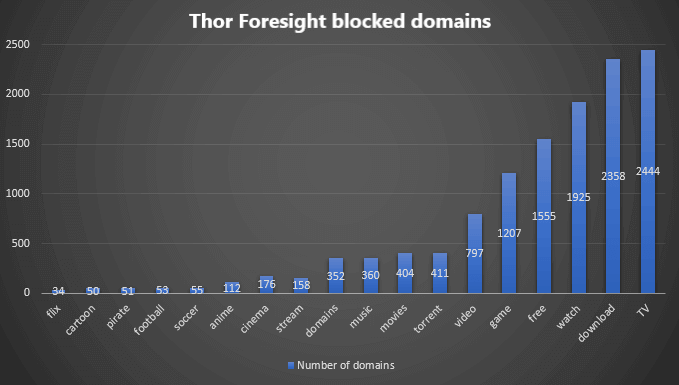
The chart makes it pretty clear that everyone wants to watch TV online and that’s when the risk of malware increases.
Since YouTube, Spotify Free and other streaming services make music available essentially free, you’ll see that there are very few domains Heimdal™ Threat Prevention blocked in that area.
With the World Cup happening these days, our users haven’t clicked a lot of compromised links when trying to watch the games. This could be explained by the fact that broadcasters really do invest in stopping pirates from streaming their content. What’s clear is that the majority of domains are related to video content streaming, which really shows how attractive they are as a host for malware.
Out of a total of 12,602 piracy-related Heimdal™ Threat Prevention blocked domains, a whopping 2,444 domains contained the word “TV” in their name. 1,925 promised users to let them “watch” content. Surprisingly, there are only 34 Netflix-clones on the list.
What about Kodi player or old-fashioned torrenting sites?
Last summer, a Checkpoint report revealed that users could get infected with malware not just by visiting compromised websites but also by loading translations.
Usually, you run the risk of clicking on a compromising link when visiting suspicious websites for downloading subtitles. However, software like VLC or Kodi can let you download subtitles right there, without visiting an additional website.
And that’s a very good target for malware.
“These subtitles repositories are, in practice, treated as a trusted source by the user or media player; our research also reveals that those repositories can be manipulated and be made to award the attacker’s malicious subtitles a high score, which results in those specific subtitles being served to the user. This method requires little or no deliberate action on the part of the user, making it all the more dangerous.
Unlike traditional attack vectors, which security firms and users are widely aware of, movie subtitles are perceived as nothing more than benign text files. This means users, Anti-Virus software, and other security solutions vet them without trying to assess their real nature, leaving millions of users exposed to this risk,” explains Checkpoint.
Updates were deployed to eliminate that vulnerability but consider this:
VLC has been downloaded 2,567311646 times (as of writing this article).
Yes, that’s more than two billion versions of VLC floating on users’ PCs. If you look at the official stats page, it’s obvious that not all of the users are updating their software so cybercriminals have plenty of vulnerabilities to target.
In January 2018, Kodi had 19 million active users, one Fmovies domain registered 26.35 million unique visitors and, dwarfing them all, the classic The Pirate Bay boasted 62.21 visitors.
Meanwhile, the AV-Test Security Institute says it registers over 350,000 new malware and potentially unwanted applications daily.
Scary, right? Just as troubling is the fact that a lot of torrent users still rely on uTorrent to open files downloaded from piracy websites. In 2015, uTorrent deployed a version that contained a cryptocurrency-mining tool, without revealing it to users properly. A year ago, uTorrent was showing an ad that was using a flash exploit to install malware, as spotted by these users.
In February this year, famous researcher Travis Ormandy warned that uTorrent had a vulnerability so serious that it could have allowed others to remotely control an infected PC.
And let’s not forget about that time when Cerber ransomware spread via pop-under ads targeted those who wanted to find a Game of Thrones episode on The Pirate Bay.
If you check for uTorrent on VirusTotal, you’ll see that some anti-viruses, including Microsoft’s, consider it to be potentially malicious software.
Popcorn Time, for example, was shut down after a copyright infringement suit but was so popular that a ransomware strain was named after it.
A great report by The Independent shows just why digital piracy is so linked to cybersecurity risks, and why it’s very profitable for both hackers and bootleggers.
How to avoid malware infections
Of course, the best answer would be to “stop pirating”. However, we know digital piracy is a topic that can be debated for a decade. We also know that this particular advice can sometimes fall on deaf ears, so it’s best to just give you the tools (and recommended security guides) to avoid malware infections.
If you or your friends/family engage with sites like fmovies / vumoo / downloadflix, use uTorrent or stream via Kodi, here are the essential steps for online security:
- Install a proactive security tool like a traffic-scanner to stop malware, ransomware, malvertising, and other threats that commonly go unnoticed by Antivirus;
- Use a well-known antivirus as a reactive security measure or at least let Windows Defender do its job;
- Tweak your browser security settings and use an adblocker like uBlock Origin to stop malvertising and cryptojacking scripts;
- For torrents, consider using a VPN – it will protect your privacy against both legitimate and fake copyright infringement notices;
- If downloading videos, stick to standard formats like AVI and MKV to avoid the trap of downloading infected codecs;
Always keep your software updated, as malware commonly exploits older versions;
[Tweet “How to safely #stream content without risking a #malware infection”]This setup will keep you safe for web browsing in general, not just for video streaming and other activities. However, nothing quite beats prevention!
If you don’t want to risk your data, it’s wiser to stick to Netflix or Hulu and split the subscription cost with a friend. If you suspect your risky browsing might have lead to a malware infection, use this guide to find out if there’s the reason for concern.


 Network Security
Network Security
 Vulnerability Management
Vulnerability Management
 Privileged Access Management
Privileged Access Management
 Endpoint Security
Endpoint Security
 Threat Hunting
Threat Hunting
 Unified Endpoint Management
Unified Endpoint Management
 Email & Collaboration Security
Email & Collaboration Security