Contents:
The Aurora information-stealing malware was delivered through an in-browser Windows update simulation in a recent malvertising campaign.
For more than a year, Aurora has been advertised on various hacker forums as an info stealer with extensive capabilities and low antivirus detection rates. Malicious ads are being used to redirect users to what appears to be a Windows security update. The scheme is very well designed, since it relies on the web browser to display a full screen animation.
Certainly Not a Windows Update
Popunder are ads that launch behind the active browser window, staying hidden until the main window is closed or moved. According to BleepingComputer, Google reported last December that popunders were used in an ad fraud campaign that attracted hundreds of thousands of visitors.
A threat actor came up with a popunder that renders a full-screen browser window simulating the Windows system update screen. Windows users are quite familiar with system updates, often interrupting their work or surfacing suddenly. When this happens, they just want to install what needs to be installed and get back to work.
Researchers tracked more than a dozen domains used in the campaigns, many of them appearing to impersonate adult websites, that simulated the fake Windows update.
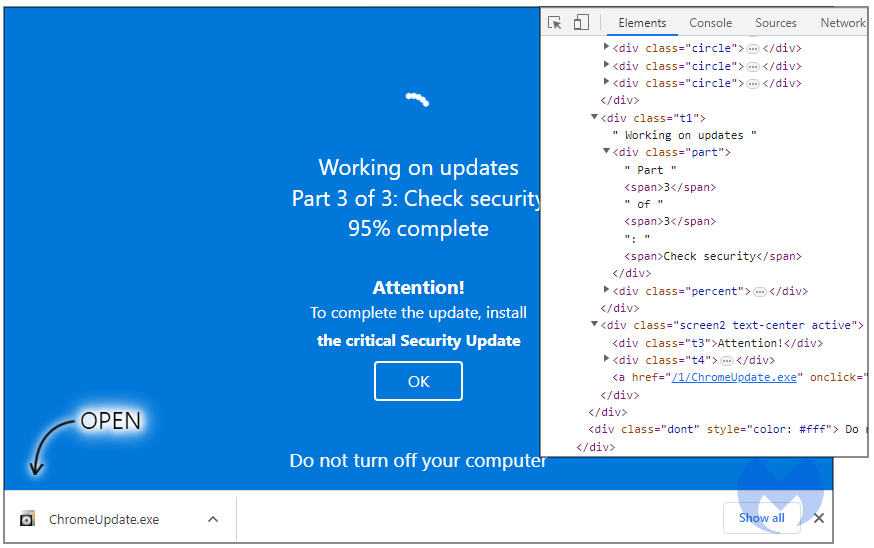
Invalid Printer Loader
The Chrome updater is a so called fully undetectable (FUD) malware loader identified as Invalid Printer that seems to be used exclusively by this particular threat actor.
Another report describes this loader as using a surprisingly simple yet highly effective evasion technique. It leverages the usage of CreateDXGIFactory function of dxgi.dll library to query the vendor ID of the graphics card installed on a system. The purpose of this is to determine if it’s running on a virtual machine or in a sandbox environment. If it’s not, it unpacks and launches a copy of the Aurora information stealer.
Researchers argue that the threat actor behind this campaign appears to be particularly interested in creating hard-to-detect tools, and they are constantly uploading new samples on Virus Total to check how they fare against detection engines.
Furthermore, the APT is using a panel to track high level stats about visitors to the fake system update web page, with 27,146 potential unique victims and 585 of them reportedly downloading the malware during the past 49 days.
If you liked this article, follow us on LinkedIn, Twitter, Facebook, and Youtube, for more cybersecurity news and topics.










 Network Security
Network Security
 Vulnerability Management
Vulnerability Management
 Privileged Access Management
Privileged Access Management  Endpoint Security
Endpoint Security
 Threat Hunting
Threat Hunting
 Unified Endpoint Management
Unified Endpoint Management
 Email & Collaboration Security
Email & Collaboration Security







