Contents:
An ongoing spam campaign spreads Knight ransomware among users. The fake emails imitate Tripadvisor complaint messages.
Knight ransomware is the revamp of the Cyclop Ransomware-as-a-Service, starting with July 2023.
The Knight Ransomware Spam Campaign
A researcher at Sophos detected this new spam campaign that spreads Knight ransomware using fake Tripadvisor complaints. The messages include a “TripAdvisorComplaint.zip” attachment that contains a “TripAdvisor Complaint – Possible Suspension.exe” executable.
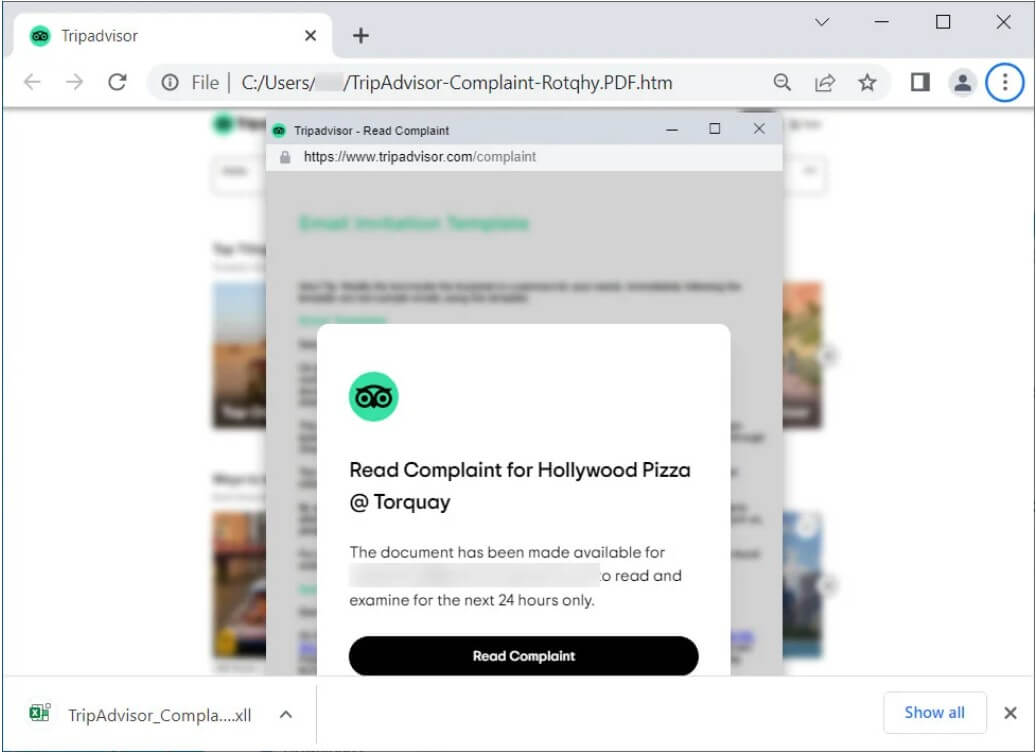
A newer version of this campaign spotted and analyzed by BleepingComputer now includes an HTML attachment named ‘TripAdvisor-Complaint-[random].PDF.htm’.
The HTML file uses Mr. D0x’s Browser-in-the-Browser phishing technique to open what looks to be a browser window to Tripadvisor. The new window displays a fake complaint submitted to a restaurant and asks the victim to review it. But the “Read Complaint” button will download an Excel XLL file named “TripAdvisor_Complaint-Possible-Suspension.xll”.
In order to execute the malware when it is opened, this XLL file was made using Excel-DNA, which integrates.NET into Microsoft Excel.
Microsoft Excel will recognize the Mark of the Web (MoTW), which is appended to files downloaded from the Internet, including email, when you open the XLL. If it recognizes the MoTW, it won’t allow the.NET add-in integrated into the Excel document, rendering the attack ineffective until a user releases the file’s restrictions. But if the MoTW is not present, Excel will allow the user to choose if they want to enable the add-in.
Once enabled the add-in, the Knight ransomware encryptor will be injected into a new explorer.exe process, beginning to encrypt the files on your computer.
All encrypted files will have the .knight_l extension. And a ransom note named “How to Restore Your Files.txt” will appear in each folder on the machine.
What to Do If You Get Infected
The Knight ransomware note in this campaign demands the victims $5,000 for the decryption key. The money should be sent to a Bitcoin address. The note also contains a link to the Knight Tor site.
However, every ransom note in this campaign seen by BleepingComputer utilizes the same Bitcoin address of ’14JJfrWQbud8c8KECHyc9jM6dammyjUb3Z,’ which would make it impossible for the threat actor to determine which victim paid a ransom.
We are still unsure as to whether paying the ransom will procure a decryptor from the Knight affiliate.
Additionally, because threat actors use the same Bitcoin address in all of the ransom notes, someone else can claim a payment as their own, effectively stealing your money.
Because there is a good probability you won’t get a decryptor in this campaign, victims are strongly urged against paying a ransom.
From Cyclop to Knight Ransomware
The Cyclop ransomware emerged in May 2023 on the RAMP hacking forum where they were searching for affiliates for their Ransomware-as-a-Service (RaaS) program.
Cyclop offers encryptors for Windows, macOS, and Linux/ESXi, as well as information-stealing malware for Windows and Linux, which is something different for a RaaS. They designed the “lite” version for spam and pray-and-spray campaigns.
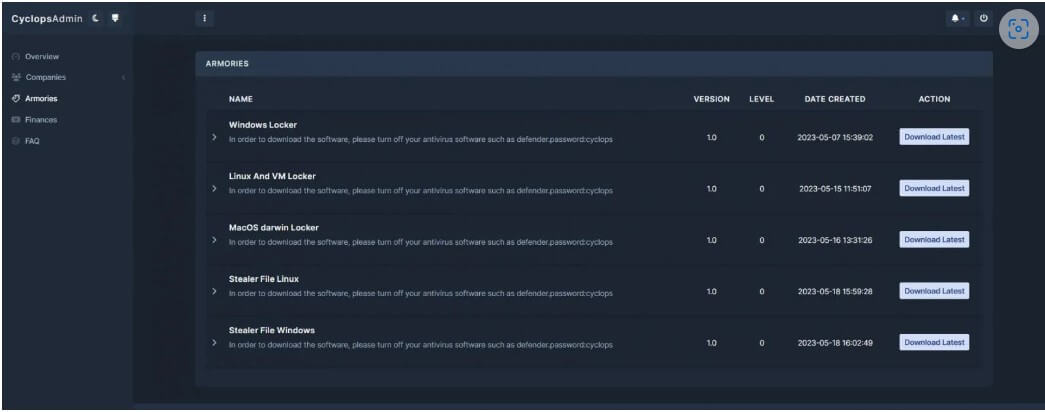
At the end of July 2023, Cyclop changed its name to Knight and announced the introduction of a new data leak website while updating the lite encryptor to accommodate “batch distribution.”
The Knight ransomware data leak site is not currently hosting any victims or stolen material.
If you liked this article, follow us on LinkedIn, Twitter, Facebook, and YouTube for more cybersecurity news and topics.










 Network Security
Network Security
 Vulnerability Management
Vulnerability Management
 Privileged Access Management
Privileged Access Management  Endpoint Security
Endpoint Security
 Threat Hunting
Threat Hunting
 Unified Endpoint Management
Unified Endpoint Management
 Email & Collaboration Security
Email & Collaboration Security