Contents:
A fake Android app called ‘SafeChat’ is used by malicious actors to infect devices with spyware malware that allows them to steal call logs, text messages, and GPS locations from phones. The spyware appears to be a variant of “Coverlm,” known for its ability to steal data from communications apps such as Telegram, Signal, WhatsApp, Viber and Facebook Messenger.
Cybersecurity researchers have identified the Indian hacking group ‘Bahamut’ APT as responsible for this campaign. The group mainly uses spear phishing messages on WhatsApp to deliver the malicious payload directly to their victims.
CYFIRMA analysts have also identified some similarities in tactics, techniques and procedures (TTP) with another Indian state-sponsored threat group known as ‘DoNot APT’ (APT -C-35). This group was already involved in spreading spyware via fake chat apps on Google Play.
In a previous incident, the Bahamut group used fake VPN apps for Android that contained extensive spyware functionality.
How Does “Safe Chat” Android Spyware Work?
The analysis of the attack does not address the specific social engineering tactics used by the hackers. However, it is common for victims to be convinced to install the chat app because they believe it provides a safer platform for their conversations, explains Bleeping Computer.
Safe Chat app has a deceptive interface that resembles a real chat application and guides the victim through a seemingly legitimate user registration process that adds credibility and serves as camouflage for the spyware.
A crucial step in the infection process is obtaining permissions to use the accessibility services, which are then exploited to automatically grant additional permissions to the spyware.
With these additional permissions, the spyware gains access to the victim’s contact list, SMS messages, call logs, external device storage, and accurate GPS location data.
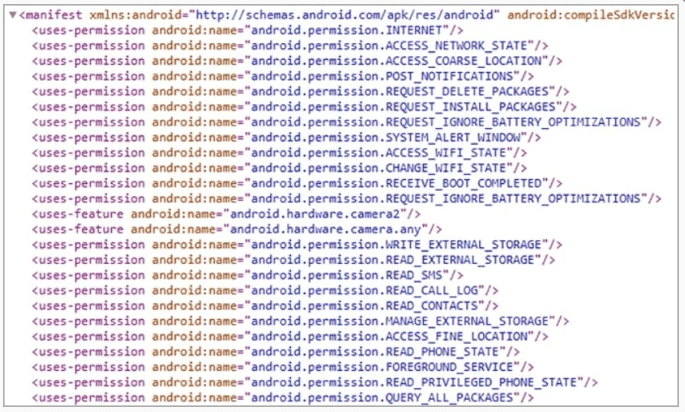
Permissions
The app also asks for the user’s consent to be excluded from Android’s battery optimization subsystem, which ensures that background processes remain active even when the user is not actively interacting with the app.
Another snippet from the Android Manifest file shows that the threat actor designed the app to interact with other already installed chat applications. The interaction will take place using intents, OPEN_DOCUMENT_TREE permission will select specific directories and access apps mentioned in intent.
The spyware contains a special data exfiltration module that transfers the stolen information from the infected device to the attacker’s command and control (C2) server via port 2053.
To protect the stolen data, the app encrypts it using various modules that support RSA, ECB and OAEPPadding. Additionally, the attackers use a “letsencrypt” certificate to avoid intercepting network data during their activities.
The analysts conclude the report by stating that there is strong evidence that the Bahamut group is working on behalf of a specific state government in India.
In addition, the use of the same certificate authority as the DoNot group APT, similar methods of data theft, a common target area, and the use of Android apps for infections indicate a possible overlap or close collaboration between the two hacker groups.
Read the full analysis here.
If you want to learn more about spear phishing, check out this article: What is Spear Phishing? Definition, Examples, Prevention Strategies.
If you’re looking for more information on Mobile Device Management, read this piece: What Is Mobile Device Management? Role in Endpoint Security and Benefits.
If you liked this article, follow us on LinkedIn, Twitter, Facebook, and Youtube, for more cybersecurity news and topics.


 Network Security
Network Security
 Vulnerability Management
Vulnerability Management
 Privileged Access Management
Privileged Access Management
 Endpoint Security
Endpoint Security
 Threat Hunting
Threat Hunting
 Unified Endpoint Management
Unified Endpoint Management
 Email & Collaboration Security
Email & Collaboration Security