Contents:
A remote code execution (RCE) attack consists of adversaries remotely running code on an enterprise`s assets. Threat actors remotely inject and execute code in the victim`s device or system by using local (LAN), or wide area networks (WAN). The code can access servers or software, open backdoors, compromise data, deploy ransomware, etc.
Threat actors use software or network vulnerabilities in order to perform a remote code execution attack. Because remote code execution attacks can compromise data without the hacker gaining physical access to the network, RCE vulnerabilities are often considered critical and patched asap.
How Does Remote Code Execution Work?
It all starts with adversaries scanning for vulnerable applications. Zero-day vulnerabilities, for example, enable them to silently access and exploit a system. Due to remote code vulnerabilities, threat actors can run malicious code and eventually take over the infected system. Once they gain unauthorized access to the network, they often try to obtain admin privileges.
Most of the time, the code they inject matches the programming language of the victim application: PHP, Java, Python, etc.
We`ll see below several types of vulnerabilities that enable actors to use remote code execution:
Injection vulnerabilities – Poor input checking leads to injection attacks. SQL injection or command injection is a good example. As SQL queries employ user-provided data, the attacker uses the opportunity to provide malicious input. Some of the data he provides will be considered commands and will be executed. This way, the threat actor has his malicious code running on the victim`s system.
Deserialization Attacks – In order to make transmission easier, data sets are packed into a single string of bits. The recipient system will later deserialize all that. Threat actors take advantage of unproperly defined structures of serialized data. They hide malware in the serialized data strings, so the recipient will unsuspiciously accept the malicious code as input and execute it.
Out-of-Bounds Write – This vulnerability happens when the software writes data outside of the buffer or before, compromising data. Usually, the software assigns exact-size pieces of memory for storing data. This includes user-provided data too.
Threat actors could write data outside of the allocated memory storage buffer when the memory assignment process is unproperly done. Their input might then be interpreted as code and executed. The outcome is data corruption or a system crash.
How Is Remote Code Execution Used in Cyberattacks?
- Initial access. Before launching their attack, threat actors usually need to collect data about the network they want to breach. RCE enables them to open a backdoor inside the system. Once they gain a foothold on the victim`s device they can move on to deploy malware, obtain admin privileges, or whatever strikes their fancy.
- Data exfiltration. Attackers also use RCE for data breaching. Remote code execution enables them to install info-stealers or even execute commands that collect and secretly remove data from an endpoint.
- Ransomware. RCE vulnerabilities frequently lead to ransomware attacks. As they enable hackers to gain access to sensitive data and seize the whole system, be sure at some point a ransomware note will also be involved.
- Root level privileges. Obtaining admin access privileges is a critical step for hackers. Privilege escalation could enable them to completely take over a network or a system. Special permissions mean they will be able to control the system at the root level. Elevated privileges also enable the threat actor to obfuscate the attack better and reside inside the system for a longer time.
- Denial-of-Service. Threat actors block servers, networks, or systems by directing to them more traffic than they can process. By running specific commands, they can crash some or all the services hosted on a server.
- Malware deployment. This is one more thing that could result from an RCE attack. It can be any type of malicious software and this includes cryptojacking.
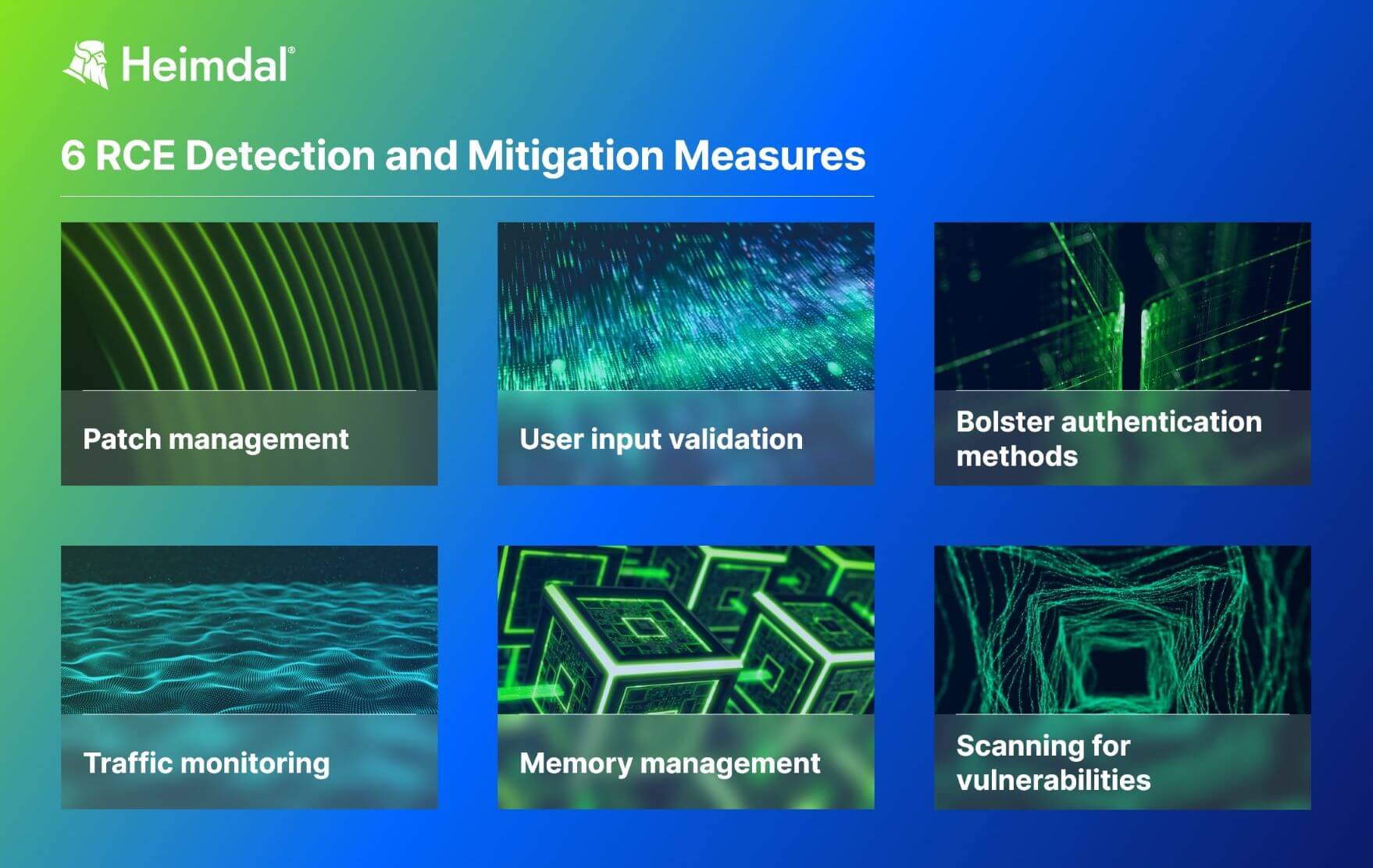
Remote Code Execution Detection and Mitigation Measures
Remote code execution attacks rely on exploiting vulnerabilities residing in various software enterprises use. In order to do that remotely, threat actors need to have an online connection. Network filtering, proper patching, and privilege access management are some of the most effective measures security admins need to take against RCE attacks.
Scanning for vulnerabilities
Exploiting zero-day vulnerabilities are one of the threat actors’ favorite ways of working. Penetration testing and scanning for vulnerabilities might look like an exhausting task for the SecOps team, but in the long run, it will save time, energy, and money. Passively waiting for the attack to happen is just what the hacker wants you to do.
Patch management
Use an automated patch management solution to make sure you never miss an important patch. Once a vulnerability and the means of leveraging it go public, make sure other threat actors will try to exploit it too. So, implement patches and updates as soon as they are available to avoid an RCE attack.
Traffic monitoring
As explained, RCE attacks happen at a network level. So, regularly checking network traffic and endpoints for anomalous queries and content is mandatory. DNS filtering is a strong security tool that keeps malicious activities away from your assets by blocking communication with adversaries.
User input validation
Always check user input before allowing it. Use whitelists, blacklists, and escape sanitization to filter out code injection and deserialization attempts.
Additionally, consider network segmentation as a mitigation measure for RCE attacks, in case a malicious code succeeds to get through.
Memory management
As we previously explained, RCE attacks can also exploit buffer overflows. So, enforce buffer overflow protection and other memory management measures to avoid it. Stop the execution of a program when a buffer overflows and use bounds checking and tagging as protection measures.
Bolster authentication methods
Adopt a zero-trust approach to prevent privilege escalation. This way you will mitigate the impact of a network breach in case it happens.
How Can Heimdal® Help Prevent RCE Attacks?
Aside from patching, one of the most effective security measure you can take against remote code execution is network monitoring. As you know by now, 91% of cyberattacks leverage DNS.
This means threat hackers exploit the fact that in an increasingly digitalized world it is almost impossible to work offline. So, what they do is use the thousands of DNS queries that go back and forth from connected endpoints to achieve their malicious activities.
To protect networks all over the world, Heimdal`s Network DNS Security solution uses cutting-edge DNS filtering and predictive DNS technology to detect and block malicious communication. It enables SecOps teams to prevent, detect and swiftly respond to endpoint, network, and IoT threats. Heimdal`s predictive DNS technology has proven a 96% accuracy in finding and predicting future threats.
Additionally, the DNS filtering engine included in the Threat Prevention Network product effectively prevents ransomware attacks. Let`s imagine threat actors eventually succeeding in deploying malware on a device. In order to encrypt and exfiltrate data, the malware needs to beacon to its command-and-control server. This is where the predictive DNS and DNS filtering engine works its magic. Communicating with the C2 will be immediately spotted and blocked.

Heimdal® Network DNS Security
- No need to deploy it on your endpoints;
- Protects any entry point into the organization, including BYODs;
- Stops even hidden threats using AI and your network traffic log;
- Complete DNS, HTTP and HTTPs protection, HIPS and HIDS;
Wrapping Up
Remote Code Execution attacks can result in a lot of trouble and money loss for a company. Data breaching, compromising servers, privilege escalation and even ransomware are possible due to RCE vulnerabilities.
Patch, apply the zero-trust principle and upgrade your network and endpoint security measures by using a professional DNS filtering solution. That is if you want to avoid an RCE attack. Keep safe!
If you liked this article, follow us on LinkedIn, Twitter, Facebook, and Youtube, for more cybersecurity news and topics.


 Network Security
Network Security
 Vulnerability Management
Vulnerability Management
 Privileged Access Management
Privileged Access Management
 Endpoint Security
Endpoint Security
 Threat Hunting
Threat Hunting
 Unified Endpoint Management
Unified Endpoint Management
 Email & Collaboration Security
Email & Collaboration Security