Contents:
An external penetration test is a type of security assessment that simulates the activities of real-world attackers to assess the resiliency of your organization’s network perimeter.
It is widely regarded as one of the first types of assessments that most organizations will undergo, as most are concerned with addressing their Internet-facing weaknesses first.
That makes sense because you don’t want just anyone to breach your perimeter security, allowing unauthorized access to applications, sensitive data, or, worst of all, an underlying host server.
Here’s an illustration of what external penetration testing looks like:
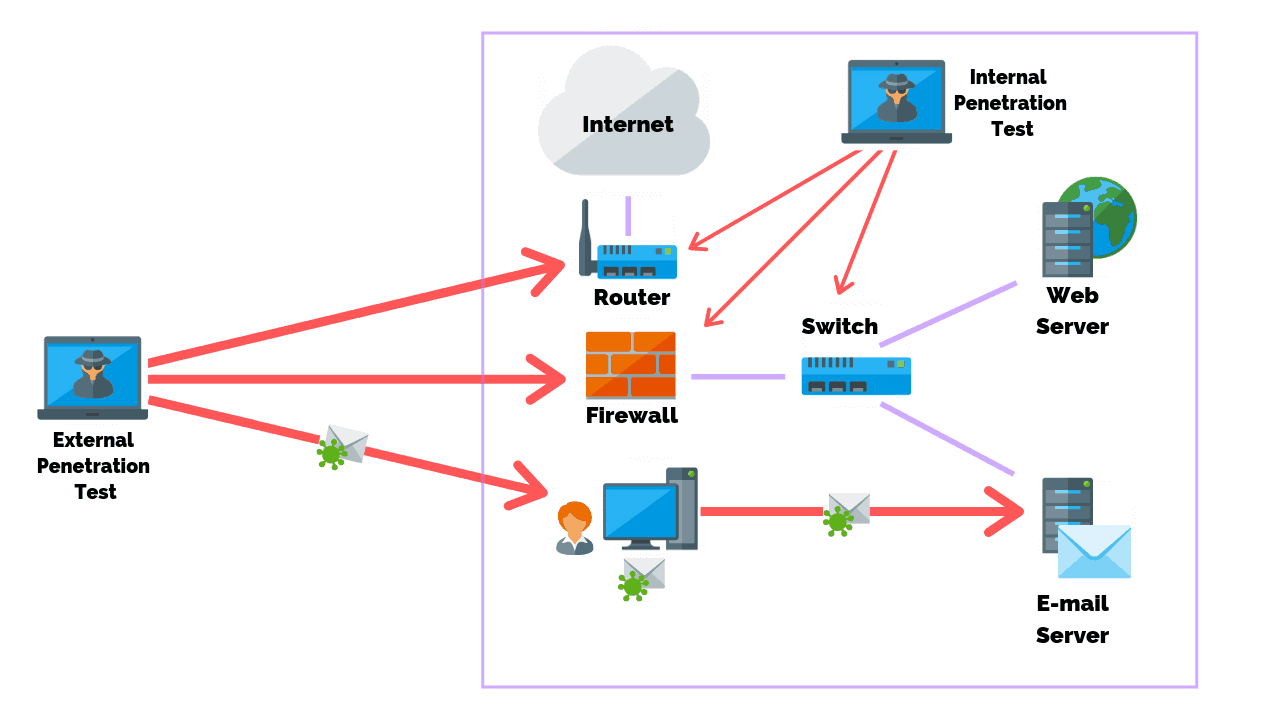
In an oversimplified definition, an external penetration test seeks to find vulnerabilities that aren’t immediately apparent. With this knowledge, you can take precautions to reduce these vulnerabilities’ risks and ensure they are minimalized.
Why Is Penetration Testing Important?
One of the main reasons penetration tests are important to an organization’s security is that they help personnel learn how to handle any break-in from a malicious entity.
In addition, pen tests serve as a way to examine whether an organization’s security policies will be effective. They can be thought of as fire drills for organizations.
Penetration tests offer solutions that help organizations not only to prevent and detect attackers but also to expel them from the system effectively.
What Does an External Penetration Test Entail?
- Open Source Reconnaissance: It uses publicly available resources to try and uncover sensitive information about a company, such as types of technology they use, potential usernames, or other info that can be used later on.
- Full Port Scan: To footprint an organization’s external perimeter, an external penetration test performs a port scan to see which services are available and accepting inbound connections. This can help determine any shortcomings in their password policy and which ports they have open.
- Vulnerability Scan: While some assessments would focus solely on a vulnerability scan, it’s just the beginning of a penetration test. A vulnerability scan will check for easy-to-find issues or weaknesses that can lead to more significant compromises.
- Unauthenticated Web Application Penetration Testing: Although it’s typically only one portion of an external penetration test, unauthenticated web application testing includes everything an attacker would see and do from a black box perspective.
- Manual and Automated Exploit Attempts: This is the most critical part of the assessment: what attackers do when trying to infiltrate your system or application. An external penetration test looks for vulnerabilities that automated scans don’t find, exploits identified vulnerabilities and understands the associated risks.
External Penetration Testing Methodology
So, we’ve already mentioned that penetration testing is a way to see what would happen if someone tried to hack your system. This is sometimes called a “mock drill,” and it provides a third-party perspective on the security of your project.
External penetration testing can be broken down into a 5-step process, which is as follows:
Step 1: Planning and Reconnaissance
The penetration testing process’s first step is defining the scope and target. You also need to choose what type of pen test you’ll be conducting.
The testing process usually starts with understanding the testing assets. A roadmap for the entire process is also defined, including deploying diverse techniques and penetration tools.
Step 2: Scanning and Vulnerability Assessment
The next step is to see what happens to the target system when they interrupt it multiple times. The tester will try to hack the target system using both static and dynamic techniques, as explained below:
- Static assessment
These tools can scan an application’s code in its entirety. They examine the application’s functions and how it functions to find issues.
- Dynamic assessment
It analyzes running codes and provides automated analysis of performance to identify inefficiencies.
Step 3: Exploitation
This is the final stage of a penetration test. In this phase, the tester exploits error-prone systems with various unconventional attacks.
White hat hackers are talented and skilled at hacking into websites to see if they can be breached or hacked. They access your site through web application attacks and try to break in, steal data, or do many other things. By locating vulnerabilities on your site, web testers can assess the potential damage these exploits could cause.
Many different tools are used for software and network testing exploits. Each one is used for specific projects and depending on the needs.
Step 4: Analysis Report
A compilation of all the penetration test findings and results are compiled into a comprehensive report, including:
- Specific vulnerabilities discovered during the testing.
- Sensitive information.
- The time the tester was able to remain undetected in the system.
Step 5: Refactoring and Rescanning
Making the required changes in the code is at the heart of this step. This process involves developers making modifications based on new vulnerabilities detected in a pen test.
Once the code has been refactored, it is then reviewed by the testers to confirm that the tested code is operating as intended.
Key Points to Keep in Mind When Performing an External Penetration Test
When organizing your external penetration test, consider the following:
- Who’s performing the assessment? A qualified penetration tester? Check out our guide on choosing a consultant to find out more about penetration testing certifications and choosing a company.
- How much will it cost? Rates are typically based on a day rate, but your job is scoped based on the days it’ll take for an assessment. Therefore, you should get quotes from different companies to find the best option.
- What is included? There are a few things to look for when reading through proposals and statements of work. First, the potential service provider will typically list what’s in and out of scope.
- What services should you be using? A provider with a good record will include tests for checking your exposed credentials, password spraying and testing any web applications that are publicly accessible.
- Should you include social engineering? Social engineering should be a good value-add, though it is sometimes successful when an attacker has enough determination. On the other hand, it should be optional if your budget is limited.
External Penetration Testing vs. Vulnerability Scanning
If you know what vulnerability scanning is, you’ll find that an external pen test shares some similarities.
But let’s see what’s the difference between the two.
External penetration testing is an in-depth security assessment but only begins with a full external vulnerability scan. After that, the pen tester will investigate all of the output manually to remove false positives and run exploits to verify the extent/impact of any vulnerabilities found. They’ll also chain together multiple weaknesses to produce more impactful exploits.
On the other hand, vulnerability scanners may report that a service has a critical weakness, but a pen test would try to exploit the flaw and gain control over the system. If successful, the pen tester would use their access to go even further and compromise other strategies and services.
To summarize, vulnerability scanning is similar to problem detection. It’s an automated technique for detecting possible vulnerable bugs in the system, while penetration testing not only detects but also exploits those vulnerabilities using external pen testing tools. This evaluation determines the extent of the security issues caused by them.
What Are the Three Penetration Testing Methodologies?
There are three penetration test techniques, and they all accomplish the same goal.
- Black-box testing
A black-box penetration test identifies computer security flaws that can be exploited outside the network. The tester must also make use of dynamic analysis techniques to do this.
On the downside, if testers can’t breach the security perimeter, internal vulnerabilities could go unfixed.
- White-box testing
White box, or open box testing, is the opposite of black box testing. Pen testers can examine every aspect of a system’s internal workings and intended behavior to find bugs that have gone unnoticed. They can also use a static analysis tool that searches for problems in the code from the computer’s memory.
- Grey-box testing
Grey-box testing chooses to provide some user information, like a middle ground between the black and white boxes. As a result, they share less detailed knowledge than a white-box tester but offer more than the black-box alternative.
Wrapping Up
An external network pen test can be hugely beneficial when assessing your current cybersecurity defenses. To simulate a malicious attack approach, the team would take on the role of an outside hacker and try to figure out what you’re missing.
The takeaway? They find gaps in your current security so that you then know where to plug them.
If you liked this article, follow us on LinkedIn, Twitter, Facebook, Youtube, and Instagram for more cybersecurity news and topics.


 Network Security
Network Security
 Vulnerability Management
Vulnerability Management
 Privileged Access Management
Privileged Access Management
 Endpoint Security
Endpoint Security
 Threat Hunting
Threat Hunting
 Unified Endpoint Management
Unified Endpoint Management
 Email & Collaboration Security
Email & Collaboration Security










