Contents:
Endpoint protection software works like a security system for a digital hotel.
They equip each ‘room’ – in our case work device – with a lock, alarms, video surveillance, etc. This way they make sure each visitor or hotel employee uses the private or common spaces safely and legit.
Endpoint protection tools act like digital shields that keep out cyber threats such as malware, ransomware, and unauthorized access.
AI and automation made cyberattacks more complex and frequent. So, using a reliable endpoint protection solution has shifted from nice-to-have to absolute necessity. Successful cyberattacks don’t just compromise data. They disrupt operations, damage reputation, and erode customer trust.
This article analyzes the 8 best endpoint protection software that can safeguard your devices and keep your business secure. Let’s dive in!
Key takeaways:
- you need more than a traditional antivirus for effective endpoint protection
- AI-powered behavior analysis is mandatory for catching advanced, unknown threats in time
- go for a cross-platform solution if your company runs more than one operating system
- best endpoint protection solutions come with a unified dashboard that makes maintenance and security processes easier to manage
Endpoint protection software types
There are various types of endpoint protection software. Knowing what’s on the table and comparing features and capabilities will help you make an educated choice when deciding what endpoint protection solution to buy for your company. For example, antiviruses are a traditional type of endpoint protection software. While they still have a place in the defense strategy, due to the increasing complexity of threats, they are no longer enough to keep a device safe. Modern solutions, like Endpoint Detection and Response platforms, go beyond recognizing and blocking already known malware. Read further to see how they do that.
Antiviruses
Antivirus software is one of the oldest tools for protecting devices. It scans computers and other gadgets to find and remove harmful programs like viruses, worms, or malware. However, traditional antiviruses are not as strong as they used to be. Their weak point is that they can only recognize malware that has already been reported by someone else. They can’t spot a new threat.
That’s why a Next-Generation Antivirus (NGAV) is a better choice. NGAVs use artificial intelligence and behavioral analysis to detect new and unknown threats. Unlike traditional antivirus tools, it doesn’t just rely on a database of known viruses. Instead, it watches for suspicious actions and stops threats before they can harm your system.
Endpoint Detection and Response (EDR)
EDR is like having a guardian on duty 24/7. This software doesn’t just block threats—it watches everything happening on your devices to find unusual behavior.
If something suspicious happens, EDR steps in to investigate and fix the problem. It keeps records of what happened, so you can track an attack’s origin and learn from past incidents to improve your defenses. EDR is especially helpful for businesses because it can monitor and provide quick incident response for thousands of devices at once.
Data Loss Prevention (DLP) Software
DLP software protects your most valuable information, like customer data, passwords, or financial records. It makes sure sensitive data doesn’t leave your company accidentally or gets stolen.
For example, DLP can block someone who tries to send private files through email or copy them to a USB drive. This is crucial for businesses that need to follow strict rules about data privacy. With DLP, you can prevent leaks and keep your data safe from both accidental mistakes and malicious insiders.
Mobile Device Management (MDM)
With so many people working on the go, mobile devices like phones and tablets need full-time protection. MDM ensures these devices are secure and follow your company’s rules.
This software allows you to control what apps can be used, lock devices remotely if they are lost, and make sure sensitive data is protected even if employees are working from home or on the road. MDM helps businesses stay safe while still being flexible.
Application Whitelisting Software
This type of software allows only approved programs to run on your devices. It creates a “safe list” of apps, blocking any software that isn’t on the list.
Application whitelisting stops harmful or unknown programs from sneaking into your system by doing this. It’s like having a security guard who checks IDs at the door, making sure only trusted applications can enter. This tool is great for reducing risks from accidental downloads or malicious files. It also prevents the shadow IT phenomenon.
Firewall and Intrusion Prevention Systems (IPS)
A firewall acts as a protective wall between your network and the outside internet. It filters and blocks unwanted traffic, like clicks on a malicious IP in a phishing email.
Intrusion Prevention Systems (IPS) take security a step further. They don’t just block threats—they actively monitor traffic to spot and stop attacks in real time. Together, firewalls and IPS create a strong barrier, keeping your systems safe from both small threats and large-scale attacks.
Best 8 Endpoint Protection Software
Finding the right tools to protect your devices and data can be tricky. To help you out, here’s a list of some of the best endpoint protection solutions. Each one has its strengths and features, so you can pick what fits your needs best.
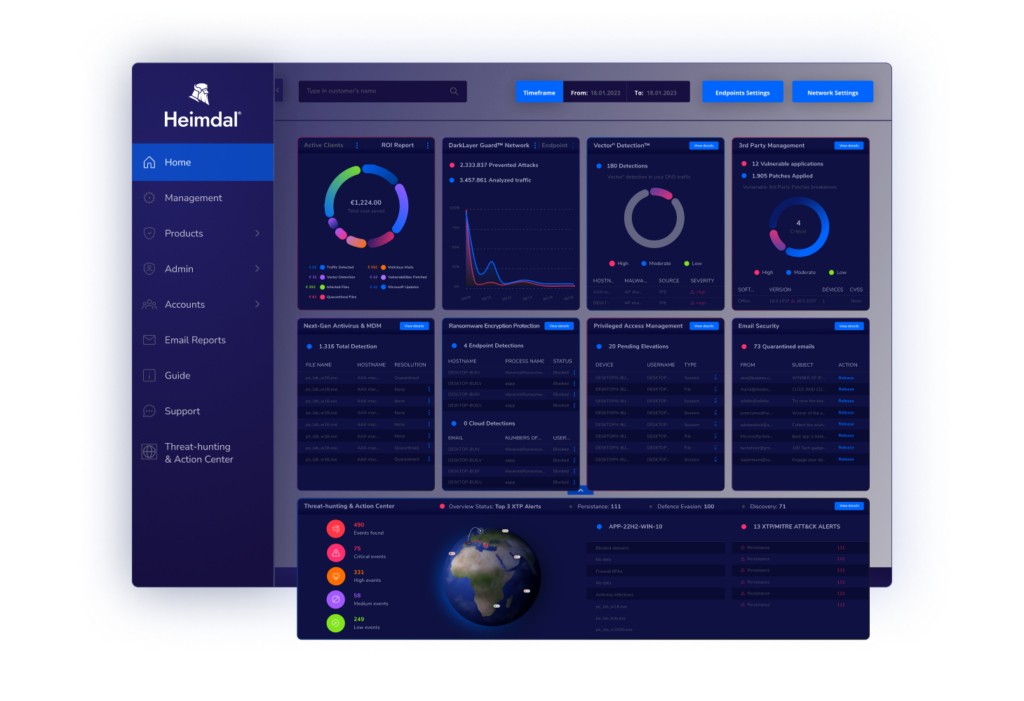
Heimdal XDR
Heimdal’s XDR platform gives you complete and affordable protection for your devices. It’s easy to use and helps IT teams manage security better with a unified, automated system. Heimdal offers multiple layers of security:
- DNS Security: Stops the infection outside your system.
- Next-Generation Antivirus: Protects against unknown advanced viruses and malware.
- Privileged Access Management: Ensures only authorized people can access sensitive data.
- Ransomware Encryption Protection: Detects and blocks suspicious encryption processes before a ransomware attack locks your files.
- Patch and Asset Management: Keeps your software up to date to fix security holes. Heimdal’s patch management tool helps check and deploy patches anytime, anywhere, in less than 4 hours.
Features
- Modular design for customizable protection
- AI-powered threat detection that helps stop attacks in real time
- Unified dashboard that shows all protection in one place, making it easy to manage
User reviews
I’ve gradually been moving all of my endpoints over to Heimdal. Mainly just using the NGAV, Ransomware Encryption Protection, Patch Management and MXDR. I’ve had a very positive experience of both the software and the company. Heimdal are very responsive to suggestions and there’s lots planned in the roadmap. I had a major concern with an endpoint and Andrei from Heimdal reached out on a Saturday evening at 7pm GMT (or 9pm in Romania, where he is based) to help me out. I buy via Brigantia in the UK and they have been very helpful with explaining how to set up the portal and I had a free session with Clelia from Heimdal to further harden my settings. If you find the portal confusing, there’s lots of support available to help.
Pricing
Heimdal offers customized Pricing that fits various business requirements and usage patterns. To see Heimdal in action before making any commitments, book a demo.
Cisco Secure Endpoint
 Cisco Secure Endpoint automatically detects and stops attacks in real-time. The system works by learning how different types of threats behave and using that knowledge to stop them before they can do any harm. Cisco also makes it easy to understand what happened during a security issue with detailed reports. This tool helps keep devices safe without requiring constant attention from IT teams.
Cisco Secure Endpoint automatically detects and stops attacks in real-time. The system works by learning how different types of threats behave and using that knowledge to stop them before they can do any harm. Cisco also makes it easy to understand what happened during a security issue with detailed reports. This tool helps keep devices safe without requiring constant attention from IT teams.
Features
- Uses machine learning to automatically detect threats.
- Provides detailed reports so you can understand attacks better
- Offers real-time protection, ensuring your devices are safe as you use them
Pricing
Its pricing starts at USD 93.60.
ThreatDown
ThreatDown watches your system in real-time and stops harmful processes before they can cause damage. If it detects a threat on your device, ThreatDown instantly blocks it. It’s easy to set up and works well with other security tools you might already have.
Features
- Real-time monitoring that detects and stops threats instantly
- Easy integration with other tools makes it simple to add into your existing security setup
- Automatic updates that keep your system protected against new threats
Pricing
Its pricing starts at USD 69 per endpoint per month.
Harmony Endpoint
Harmony Endpoint from Checkpoint offers advanced EPP, EDR and XDR capabilities. The solution ensures that your employees can access important company information securely, even if they are working from home or other locations. Harmony Endpoint gives detailed reports on any security issues, so you can learn from past attacks and prevent future problems.
Features
- Easy to deploy for On-Prem, Cloud, or MSSP Management
- Secure remote access for workers
- Detailed incident reports that show exactly what happened if an attack occurs
Pricing
You need to request a quote as per your requirements.
Vipre EDR
Vipre EDR monitors devices and uses advanced technology to detect suspicious activities. When a threat is found, Vipre immediately blocks it and alerts you, so you can take action. It also provides real-time updates, so you never miss any new vulnerabilities or dangers.
Features
- Uses artificial intelligence to detect unusual behavior on your devices
- Provides real-time alerts when something suspicious is found
- Detailed reports that show where the incident originated and how to stop it
Pricing
Pricing depends on the company’s requirements. Get in touch with the vendor for a customized offer.
Threatlocker
Threatlocker’s endpoint protection platform (EPP) uses a list of approved software and blocks anything that isn’t on the list. It might sound like any other application whitelisting tool, but it goes beyond that. Threatlocker also controls the way those apps interact with each other and what resources they get to access.
Threatlocker is easy to set up and you can customize it to fit your company’s needs.
Features
- Unified approach
- Automatic updates to make sure your protection is always up to date
- Controls over storage, so only authorized users can access important files
Pricing
You need to request a quote as per your requirements.
Trend Vision One
Trend Vision One uses machine learning to predict and stop future threats based on patterns and behaviors. Their endpoint protection solution shines at offering real-time protection and quick responses to security issues. Trend Vision One also provides helpful reports and alerts that let you know exactly what’s happening on your devices.
Features
- Unified platform that combines antivirus, endpoint detection and response (EDR), and automated threat detection
- Detailed insights into security incidents help you understand what happened
- Fast response to stop threats before they spread
Pricing
It lets you use the platform for free for 30 days. After that, you can contact its sales team to get a final quote as per your requirements.
VMware Carbon Black Cloud

VMware Carbon Black monitors your devices for suspicious activities and uses advanced tools to block dangerous programs. It also works by detecting attacks before they happen by spotting patterns and Indicators of Compromise (IoCs), giving businesses extra time to respond. It makes security easy for businesses by providing a single platform to manage all devices and data in one place.
Features
- Advanced endpoint protection that stops even the most sophisticated threats
- Real-time monitoring to detect and block attacks as they happen
- Detailed analytics to help IT teams understand and respond to threats
Pricing
Its pricing starts at USD 36 per endpoint per year when committing to Cloud Endpoint Standard for 36 months, to USD 90 per endpoint per year with a 12 month subscription to Cloud Endpoint Enterprise.
Why use advanced endpoint protection software?
Using advanced endpoint protection solutions comes with a series of benefits. Here are some of the most important.
Prevent sophisticated threats
Advanced endpoint protection software is designed to stop complex attacks that traditional security tools might miss.
Phishing would not happen – or has a very small chance of happening – if you have a very capable email security tool. Advanced software can spot hidden threats like phishing emails before they cause harm, adding an extra layer of security.
Andrei Hinodache, Cybersecurity Architect and Technical Product Marketing Manager @Heimdal – Source
Imagine you receive an email that looks like it’s from a trusted company, but it contains a hidden virus. If you click on it, your computer could be infected. Advanced protection can spot the virus and block it before you even click, keeping your computer safe.
It’s like having an expert guard who knows all the tricks criminals use and stops them in their tracks.
Reduce the attack surface
Your computer or phone has certain entry points, or “doors,” that hackers can use to break in. If these doors are left open or unguarded, it’s easier for the bad guys to get in. Advanced software closes unnecessary doors and secures the ones you necessarily need to keep open.
Under mitigation of entry points, we have secured internet traffic, patching, admin rights management, zero trust methodology, software control, and so on. These strategies collectively shrink the attack surface and reduce the chances of an attacker getting through.
Andrei Hinodache, Cybersecurity Architect and Technical Product Marketing Manager @Heimdal – Source
For example, if you use a public Wi-Fi network, hackers might try to attack through that network. Advanced protection will help secure your connection and stop attackers from using it to get into your system.
Enhanced Data Security
As an organization, most of the data you collect is precious: employees’ IDs, payrolls, customers’ financial data, etc. Advanced endpoint protection solutions restrict access to this data so only you or the people you trust can see, change, or download it.
The human factor is the most interesting because it’s an ongoing process. Make sure you have strong password policies, intelligent multi-factor authentication, and apply the principle of least privilege.” These measures ensure your data remains protected, even in high-risk scenarios.
Andrei Hinodache, Cybersecurity Architect and Technical Product Marketing Manager @Heimdal – Source
For instance, if your phone gets stolen, endpoint protection software can remotely lock it or, if necessary, wipe all the information on it. This way you’ll be sure no one can view any private data you might have stored or used on the device.
Think of it like a safe where only you have the key. Even if someone finds it and tries to break in, they won’t be able to open it.
Support meeting compliance goals
Businesses, especially in fields like healthcare and finance, need to follow strict rules about protecting data.
Cybersecurity has three pillars: people, processes, and technology. Don’t forget the first two—they are very important.” Advanced endpoint protection ensures organizations adhere to regulatory standards while safeguarding their systems.
Andrei Hinodache, Cybersecurity Architect and Technical Product Marketing Manager @Heimdal – Source
For example, hospitals rely on advanced endpoint protection software to secure patient records and ensure they meet HIPAA privacy standards. If hackers were to access patient data, the hospital could face severe consequences, including NIS2 fines, legal actions, and damage to their reputation. With this software, threats are detected and blocked before they can cause harm, keeping the organization both safe and legally compliant.
Real-time threat detection
Due to advanced endpoint protection software, your devices are continuously monitored for threats. It’s like having a security guard who never sleeps and always keeps an eye out for trouble.
You should have one place where you see everything, including forensic telemetry, lateral movement sensors, and credential harvesting detection, to react fast. This enables real-time threat detection and immediate response.
Andrei Hinodache, Cybersecurity Architect and Technical Product Marketing Manager @Heimdal – Source
If a hacker tries to break into your system, the software will detect the threat in real-time and stop it immediately. This prevents serious damage from happening.
For example, if hackers successfully download malware on your computer, an endpoint protection software like Heimdal’s XDR will detect and remove it in real-time. There will be no further damage, since the attackers will not have enough time to access and exfiltrate your data.
Secure remote work environments
Remote work has become the norm, but it also introduces new risks to company devices. Employees working outside the office often share more information online, whether through unsecured networks in places like coffee shops or on personal devices that lack enterprise-level protection.
Without advanced endpoint management solutions, IT teams face challenges in addressing vulnerabilities or ensuring devices are properly maintained remotely. This lack of oversight makes it easier for hackers to exploit security gaps, compromising sensitive company data. Advanced endpoint management tools solve this by monitoring devices, applying patches, and securing data no matter where employees work.
Admin rights management and zero trust methodology are key to defending against ransomware. Nothing that is not needed or approved should run in your environment. This ensures that remote environments are as secure as traditional office setups.
Andrei Hinodache, Cybersecurity Architect and Technical Product Marketing Manager @Heimdal – Source
Take action to protect your endpoints today
Endpoint security has evolved way over traditional antiviruses and firewalls. This evolution is directly connected to hackers creating more complex kinds of threats. So, you also need to level-up your endpoint protection strategy by implementing the right tools and policies.
When choosing the best endpoint protection solution for your organization, look for one that offers unification, automation, and a modular approach. This way you can integrate exactly the tools you need under the same umbrella.
Among the many options available, Heimdal’s XDR platform is one of the best choices. It combines various security tools into a simple-to-use, automated system. With Heimdal, you can manage updates, prevent threats, and control all devices from one easy-to-use dashboard.
If you’re looking for a smart, simple, and powerful solution, Heimdal is the way to go. It integrates seamlessly with your existing tools, strengthens security, and makes your IT team’s work more efficient.
FAQs
1. How can I tell if my computer needs endpoint protection?
If your device is connected to the internet and/or you exchange data in any way with other devices then yes, you should use an endpoint protection solution.
Check for signs of a potential infection, like the device running slow, freezing, or showing weird pop-ups.
2. What should I look for when choosing endpoint protection?
Look for software that:
- Uses automation to solve redundant tasks and processes
- It’s easy for you to install and use
- Works on various operating systems
- Uses machine learning and behavior analysis to detect unknown threats
3. Is endpoint protection the same as antivirus?
Traditional antiviruses only detect and block threats they find on a list with reported threats. They are useless against unreported malware. On the other hand, endpoint protection can include behavior analysis that can spot unknown threats, patch management, ransomware encryption protection and more.
If you liked this article, follow us on LinkedIn, Twitter, Facebook, and Youtube, for more cybersecurity news and topics.










 Network Security
Network Security
 Vulnerability Management
Vulnerability Management
 Privileged Access Management
Privileged Access Management  Endpoint Security
Endpoint Security
 Threat Hunting
Threat Hunting
 Unified Endpoint Management
Unified Endpoint Management
 Email & Collaboration Security
Email & Collaboration Security