Did you know, the average employee today uses 2.5 devices to carry out their work?
Across businesses, this can add up to hundreds or even thousands of bits of kit. One 2021 study in the UK found two-thirds of large businesses (250+ employees) have more than 1,000 devices on their networks, while medium-sized companies (50-249 employers) have 185, on average.
All these devices can help boost productivity. But they also expose you to new kinds of risk.
And that’s where Endpoint Detection & Response (EDR) comes in.
EDR is a type of cybersecurity solution that monitors all the endpoints (i.e., laptops, desktops, smartphones, tablets etc.) on your network.
Let’s learn more about this approach, as well as the top 8 EDR benefits.
Endpoint Detection & Response In a Nutshell
EDR is a kind of cybersecurity solution that monitors activity on all the endpoints (devices) on a company’s network.
It tracks various kinds of activity on endpoints, including user behavior, system logs, network traffic and more, and analyzes endpoint data.
If it detects anything suspicious on a device, the EDR system will alert IT teams.
It might also automatically isolate the device on the enterprise network if a threat is detected.
That can help stop breaches from spreading.
An endpoint solution can track activity on endpoints in different ways, but they typically install a lightweight agent on each device.
This will silently track activity in the background, then send information to a centralized dashboard used by your security team.
While EDR isn’t new (the term was coined in 2013), it has become more common in the era of remote work. As more employees use more devices to do their work away from the office, traditional firewalls and antivirus are less capable of keeping organizations safe. EDR can be part of the solution.
Strengthen your cybersecurity with EDR
Detect and respond to threats effectively with Heimdal's EDR.
To learn more about what EDR is, read our comprehensive guide.
Related: EDR vs XDR – a comparison
8 EDR Benefits

- Steven Legg, CEO of US Cybersecurity Consultancy Antigen
1. EDR Enables Modern Working Styles
As mentioned above, the modern workplace is characterized by the usage of multiple connected devices.
What is more, people now connect to company networks remotely when working from home or while traveling.
Traditional cybersecurity methods are simply not suited to this reality.
Firewalls and antivirus conceptualize work as something that happens at a place (i.e. the office). Yet, as we now all know, work can be done anywhere that employees have an internet connection.
Using EDR recognizes this reality. It allows people to work remotely in a secure way, by scanning their devices for potential threats – even when they’re outside of the network. It also means people are less likely to use shadow IT or unsecured personal devices to do work on.
2. Helps You Detect Breaches Faster
Using an EDR solution can help companies detect cybersecurity attacks faster. In a 2020 survey, 14% of companies with an EDR said they detected a security breach almost instantly, compared to 9% who didn’t use them.
Similarly, 14% of companies with an EDR detected breaches “within a few hours”, compared to 10% without an EDR.
The survey also found that companies without an EDR system were more likely to take weeks or months to detect breaches compared to those that had one installed.
Reduces IT Friction

- Michael Warrer, Group CIO at NRGi
Defense in Depth
Using EDR technology can save significant amounts of time and friction for both IT workers and end users. Using EDR means people can work anywhere without having to get their devices inspected by IT or have additional software installed.
That means they can just do their work without extra effort or waiting for approvals.
There is no single cybersecurity technology that can protect organizations against all kinds of threats.
However, using EDR gives you greater depth, with another layer of security covering all the endpoints on your network.
No one can claim EDR is completely impregnable – no security technology can be.
But having an additional layer makes it more likely you will ‘catch’ malicious actors that do get inside your systems.
Security evolution: Why more companies are adopting cybersecurity platforms
5. Increases Visibility for IT Teams

- Nabil Nistar, Head of Product Marketing at Heimdal
EDR helps security professionals monitor their environments in a far more comprehensive way than ever before. Without EDR, security breaches on a device can go weeks or months without being detected. It’s often only when an employee notices their device is “playing up” that they notify IT about the problem – and at this stage the breach may have spread.
Using EDR gives you far more visibility into your entire network. From a central dashboard, you receive alerts about suspicious activity and can proactively respond to them.
6. Compliance and Audit Trails
Most organizations today are required to follow minimum security standards.
They must be able to show they have made appropriate efforts to protect data. And Endpoint Detection & Response can help here.
It provides an entirely auditable log of all activity on your network, and proves you have taken adequate precautions to protect sensitive information.
7. Investigate Breaches More Effectively
An EDR solution also helps cybersecurity professionals investigate breaches more effectively.
The lightweight agents installed on all endpoints keep a constant log of activity on the device. This can help identify exactly when and how a breach happened – so you can learn more about what might have caused it.
8. Respond to Threats Automatically
Breaches can happen any time of day – including at night or on weekends when your security teams may be unable to respond.
Some Endpoint Detection & Response solutions can automatically respond to threats, isolating infected devices from the network or encrypting data stored on them. This can help prevent the spread of attacks.
EDR Challenges And Limitations
Although there are many EDR benefits, it’s also important to be aware of its limitations. These include:
Cannot catch everything
No cybersecurity solution can claim to prevent all types of cyber threats. EDR should be viewed as a layer of your wider security posture.
Alert fatigue
Depending on how you set up your EDR, the issue of ‘alert fatigue’ may arise. If security staff get dozens of possible alerts about cyber threats and data breaches each day – which turn out to be false positives or unimportant – they may start to ignore potential breaches.
Only covers endpoints
Naturally enough, EDR only monitors endpoints on your network. For some organizations that’s enough.
But as companies connect ever more cloud apps, IoT sensors and other kinds of technology, the attack surface starts to expand. To address this, some organizations now adopt Extended Detection & Response (XDR), which monitors a wider range of data in more places.
Protect Your Business With Heimdal® XDR
There are so many benefits to an EDR solution – from protecting your data, to achieving compliance, responding to cyber threats, through to enabling modern working practices.
But not all EDR tools are the same. They track data in different ways, and use varying levels of sophistication and machine learning to analyze threats and respond to them.
Heimdal® XDR is the widest cybersecurity platform on the market and it offers advanced threat hunting, unparalleled prevention, efficient remediation, and more.
We have developed a holistic approach to EDR which gives you enormous power – but with a lightweight solution that doesn’t slow endpoints down.
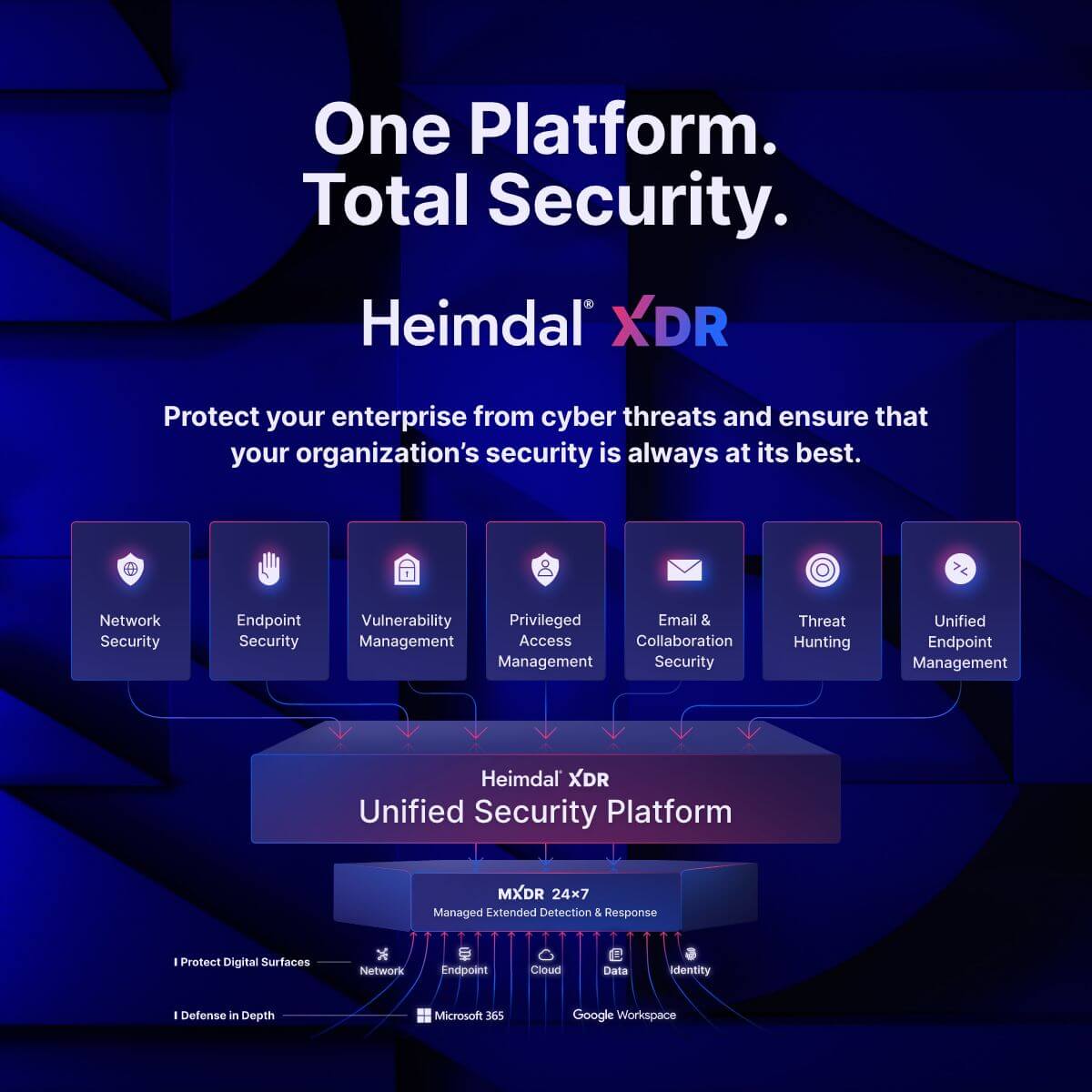
We’re confident Heimdal XDR® is the most comprehensive cybersecurity platform on the market. Here’s why:
- All major cybersecurity solutions in one place;
- AI and ML threat intelligence;
- Instant, unified intelligence;
- Automated threat response and task management;
- APIs to most third-party point solution vendors;
- World-class, 24/7, global support;
- Continually evolving.
Learn more about our EDR solution and take your cybersecurity posture to the next level with Heimdal®!










 Network Security
Network Security
 Vulnerability Management
Vulnerability Management
 Privileged Access Management
Privileged Access Management  Endpoint Security
Endpoint Security
 Threat Hunting
Threat Hunting
 Unified Endpoint Management
Unified Endpoint Management
 Email & Collaboration Security
Email & Collaboration Security








