Contents:
The Donut extortion group has been confirmed by cybersecurity experts to deploy ransomware in double-extortion attacks on organizations. Since August of this year, the extortion group has been linked with attacks on multiple companies such as DESFA, Sheppard Robson, and construction company Sando.
Based on various evidence, it is believed that behind the Donut Leaks there is an affiliate for numerous operations, trying to monetize the data in their own operation. Such suspicions aroused after the data for Sando and DESFA was also posted to the sites of other operations, with Sando being claimed by Hive ransomware, and DESFA by Ragnar Locker.
The Donut Operation: What Is It?
BleepingComputer found a sample of an encryptor for the Donut operation, finding out that the threat group is using its own custom ransomware for double-extortion attacks.
Although the ransomware is still being examined, when it is run, it will look for files with particular extensions to encrypt. Files and folders with the following strings will not be encrypted by the ransomware:
- Edge
- ntldr
- Opera
- bak
- Chrome
- DAT
- ini
- AllUsers
- Chromium
- bootmgr
- Windows
- db
- ini
- dat
- ini
- efi
- inf
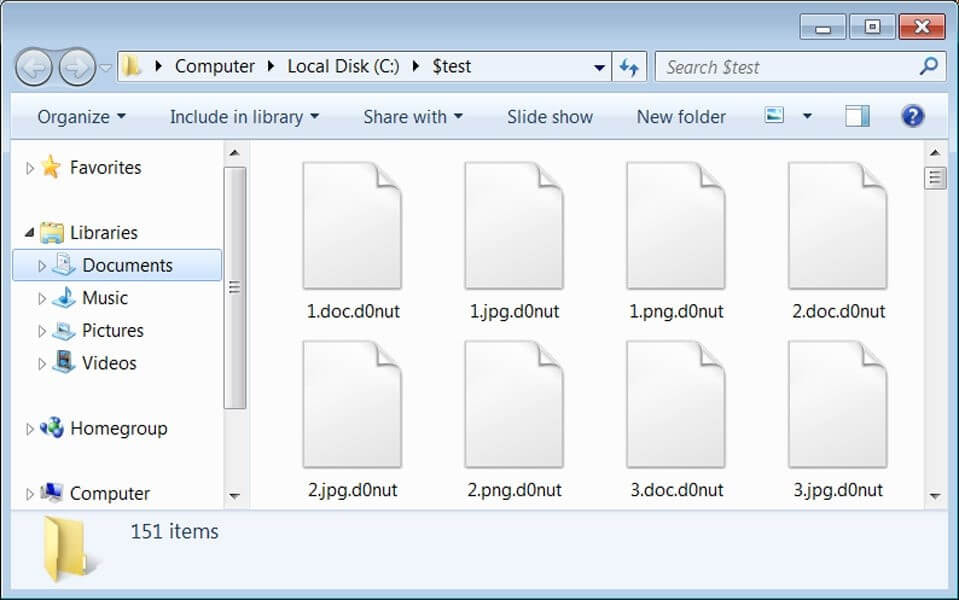
Example of Files Encrypted by the Donut Ransomware (Source)
The ransom notes deployed by the malware are heavily obfuscated to avoid detection, with all strings encoded and the JavaScript decoding the note in the browser. There are other ways to get in touch with the threat actors listed in these ransom notes, including TOX and a Tor negotiation site.
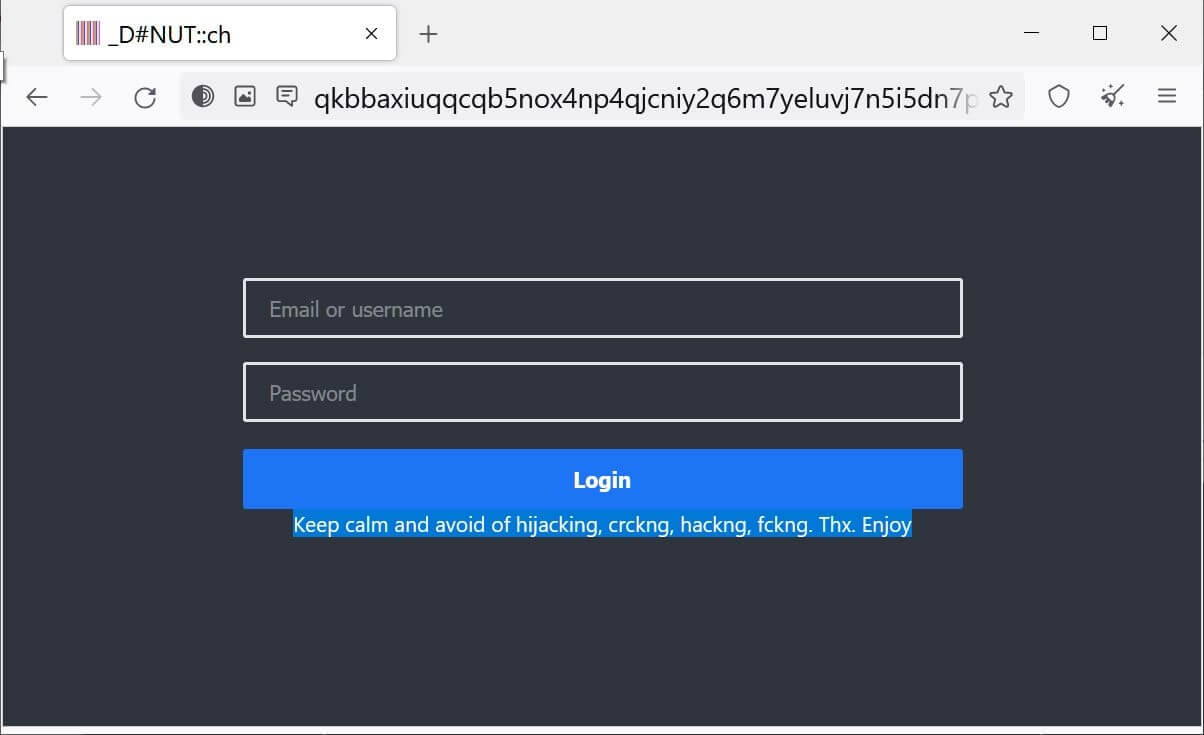
Donut Ransomware Negotiation Site (Source)
The ransomware operation also includes a “builder” on their data leak site, which is currently broken as it uses HTTPS URLs. The builder consists of a bash script to create a Windows and Linux Electron app with a Tor client bundled to access their leak sites.
This extortion group is one to watch out for, not only for its capabilities but also for its ability to market itself.
If you liked this article, follow us on LinkedIn, Twitter, Facebook, Youtube, and Instagram for more cybersecurity news and topics.


 Network Security
Network Security
 Vulnerability Management
Vulnerability Management
 Privileged Access Management
Privileged Access Management
 Endpoint Security
Endpoint Security
 Threat Hunting
Threat Hunting
 Unified Endpoint Management
Unified Endpoint Management
 Email & Collaboration Security
Email & Collaboration Security










