Contents:
In a previously-published material, Heimdal® has analyzed the emergent Dark Power malware – a ransomware strain written in the NIM programming and capable leveraging advanced encryption techniques such as CTR for a better stranglehold on the victim’s device and, implicitly, the hosted data. Open-source threat intelligence feeds shed very little insight on the preferred vector of infiltration (i.e., functional assumption is based on the fact that, statistically speaking, most ransomware is transmitted via email) and vulnerability discovery & abuse (i.e., insufficient data on brutalized coding vulnerabilities). Heimdal®’s research in vulnerability D&A associated with the Dark Power strain has revealed that the ransomware abuses kernel-related APIs at IPC level, thus managing to move faster across the cyber-kill chain. In this article, we will take a closer look at the vulnerabilities and map out connections to know CVEs.
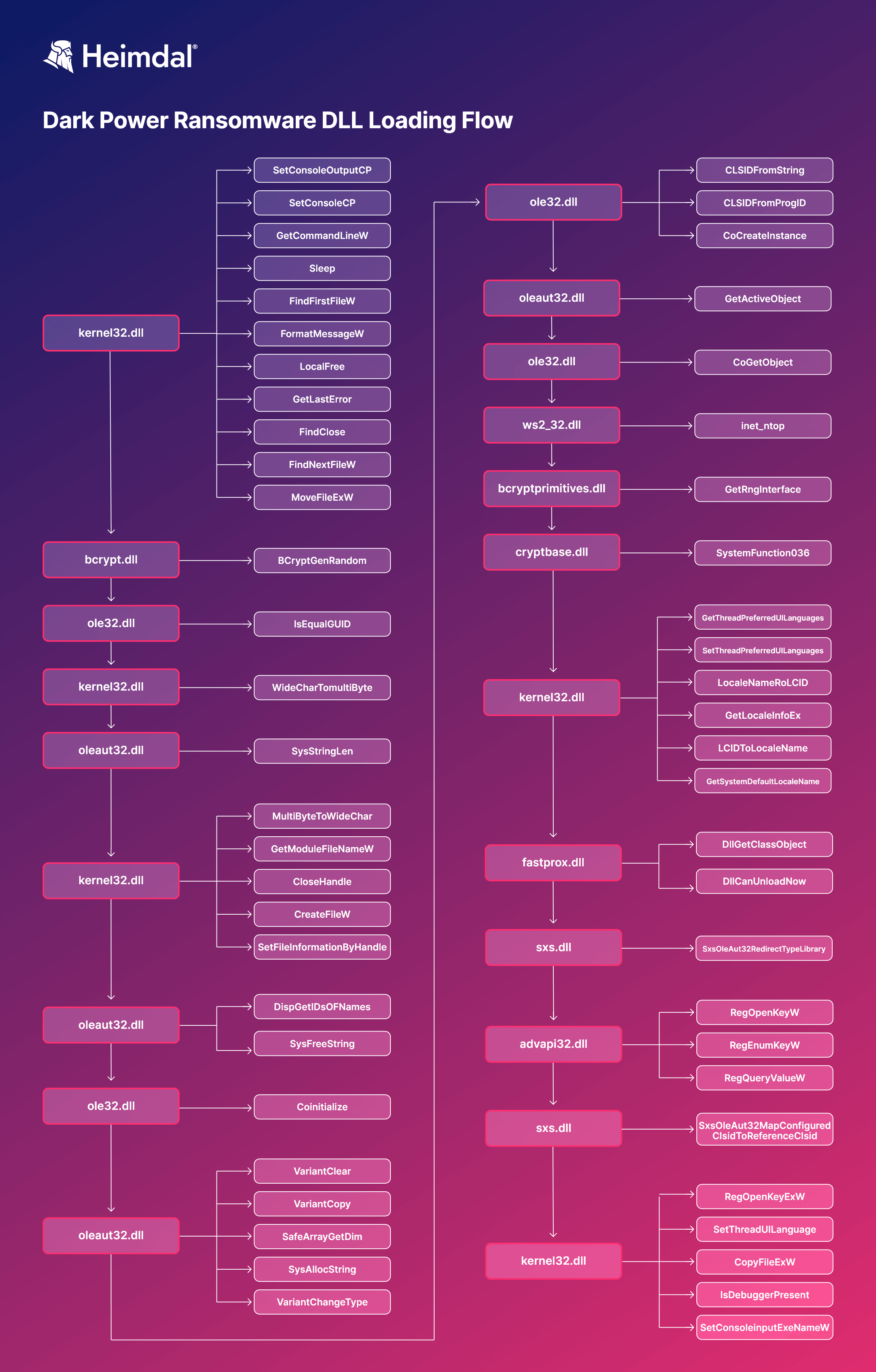
Drill-down APIs workflow resolved by the Dark Power ransomware
Our investigation begins with a CapeSandbox resolved APIs dump. To summarize, the Dark Power ransomware interacts with the following DLLs; commands have also been included for each step.
kernel32.dll
Description: a 32-bit dynamic link library (DLL) found in the Microsoft Windows OS kernel. Its purpose is to handles memory management, input/output (i.e., I/O) operations, and interrupts. Upon successful boot, kernel32.dll is loaded into a protected memory space so other applications cannot interfere with it. When it occurs, it will return the “invalid page fault” error.
Association to documented CVEs and/or similar malware family
- CVE-2007-4528 – The FFI extension found in PHP 5.0.5 does not permit safe_mode restriction. This threat-actors to execute arbitrary code by loading an arbitrary Dynamic-Link Library and calling a function, such as kernel32.dll or the WinExec function.
- CVE-2007-5145 – “Multiple buffer overflows in system DLL files in Microsoft Windows XP, as used by Microsoft Windows Explorer (explorer.exe) 6.00.2900.2180, Notepad++, unspecified Adobe Macromedia applications, and other programs, allow user-assisted remote attackers to cause a denial of service (application crash) via long strings in the author, title, subject, and comment fields of a file, possibly involving improper handling of extended file attributes by the:
- NtQueryInformationFile,
- NtQueryDirectoryFile,
- NtSetInformationFile,
- FileAllInformation,
- FileNameInformation, and other FILE_INFORMATION_CLASS functions in ntdll.dll
- GetFileAttributesExW
- GetFileAttributesW functions in kernel32.dll.”
CVE description courtesy of NIST
- CVE-2007-1347 – A bug in Windows Explorer (i.e., versions Windows 2000 SP4 FR and XP SP2 FR), allows remote threat actors to trigger a denial of service via a crafted Office file.
- TR-23 – NetWiredRC Malware. A feature-rich RAT (i.e., Remote Access Tool) with the following import table: kernel32.dll, user32.dll, gdi32.dll, advapi.dll, shell32.dll, comctl32.dll, shlwapi.dll, ole32.dll, oleaut32.dll, and version32.dll. Observed Command & Control traffic associated to TR-23 employed AES-256-OFB proprietary protocol for malicious actions on object.
bcrypt.dll
Description: also known as the Windows Cryptographic Primitives Library, this DLL provides cryptographic functions (i.e., deriving hashes or encrypting/decrypting information).
Association to documented CVEs and similar malware family
- CVE-2023-28260 – .NET DLL Hijacking Remote Code Execution Vulnerability
- CVE-2022-32223 – the Node.js is vulnerable to DLL hijacking if certain conditions are met (i.e., victim’s machine .This vulnerability can be exploited if the victim has the following dependencies deployed on Microsoft Windows-running machine: OpenSSL 8220 and openssl.cnf”. The mechanism is as follows: if the conditions are met, the node executable will search for the providers.dll located in the active user directory. Consequently, `the node executable will attempt to search for the same DLL via Windows’ DLL Search Order. Hijacking is possible if the threat actor plants a malicious providers.dll.
- CVE-2021-38571 – affects Foxit Reader and PhantomPDF before 10.1.4 making them vulnerable to DLL hijacking.
- CVE-2023-29187 – A Windows user with basic user authorization can exploit a DLL hijacking attack in SapSetup (i.e., Software Installation Program) – version 9.0, resulting in a privilege escalation running code as administrator of the very same Windows PC. A successful attack depends on various preconditions beyond the attacker’s control.
- Nokoyawa ransomware.
- Karma ransomware.
ole32.dll
Description: provides the Component Object Model, as well as Object Linking and Embedding.
Association to documented CVEs and similar malware family
- MS05-012: Remote Code Execution via bugs in COM and OLE.
- MS05-051: Vulnerabilities in MSDTC and COM+ Could Allow Remote Code Execution (902400)
- LockBit ransomware.
- Emotet.
oleaut32.dll
Description: a shared OS file and loaded by multiple applications for setup purposes.
Association to documented CVEs and similar malware family
- Vulnerability Note VU#158647 – Microsoft Windows Object Linking and Embedding (OLE) OleAut32 library SafeArrayRedim function vulnerable to remote code execution via Internet Explorer
- CVE-2022-34101 – A vulnerability was discovered in the Crestron AirMedia Windows Application, version 4.3.1.39, in which a user can place a malicious DLL in a certain path to execute code and preform a privilege escalation attack.
ws2_32.dll
Description: the DLL’s main purpose is to loads the service provider’s API DLL into the system by leveraging the operating system’s dynamic library loading mechanisms. Initialization is done by calling the WSPStartup function.
Association to documented CVEs and similar malware family
- WannaCry.
- BlackByte ransomware.
- LockBit Green ransomware.
- Ranzy Locker ransomware.
- Conti ransomware.
bcryptprimitives.dll
Description: Microsoft DLL containing routines for implementing cryptographic primitives and fundamental building-block algorithms.
Association to documented CVEs and similar malware family
fastprox.dll
Description: a DLL used by the WMI Custom Marshaller.
Association to documented CVEs and similar malware family
sxs.dll
Description: is a vital OS that handles the logging process the manifest files, with a role in binding and the activation process(s) associated with each manifest.
Association to documented CVEs and similar malware family
- CVE-2016-4349 – Untrusted search path vulnerability in Cisco WebEx Productivity Tools 2.40.5001.10012 allows local users to gain privileges via a Trojan horse cryptsp.dll, dwmapi.dll, msimg32.dll, ntmarta.dll, propsys.dll, riched20.dll, rpcrtremote.dll, secur32.dll, sxs.dll, or uxtheme.dll file in the current working directory, aka Bug ID CSCuy56140.
advapi32.dll
Description: short for Advanced API Services Library, advapapi32 is a Microsoft-specific utility that used for API support and employed in various operations such as registry, security calls, and advanced features.
Association to documented CVEs and similar malware family
- CVE-2017-11742 – The writeRandomBytes_RtlGenRandom function in xmlparse.c in libexpat in Expat 2.2.1 and 2.2.2 on Windows allows local users to gain privileges via a Trojan horse ADVAPI32.DLL in the current working directory because of an untrusted search path, aka DLL hijacking.z
- CaddyWiper – a destructive data wiper that has been deployed in attacks against organizations in Ukraine.
- Cuba ransomware.
- Backdoor: W32/TDSS.
- Nefilim ransomware.
- AtomSilo ransomware.
This is an ongoing Heimdal® investigation. We will update the document with additional information as soon as they become available.
Conclusion & Countermeasures
In dealing with the novel Dark Power ransomware, Heimdal® has the following recommendations.
- Access Governance to limit access to sensitive network-shared resources. Ransomware also encrypts data that’s shared over the network. Deploying an IAM will severely decrease the chances of over-the-network encryption and lateral movement.
- Cloud backups. Dark Power ransomware removes backups and shadow copies stored on the machine. Regularly backing up to your cloud provider and having a disaster recovery plan in place makes it easier to retrieve your data in case of ransomware encryption.
- Cybersecurity education. We strongly believe that (continuous) cybersecurity education is the right way to prevent such occurrences.
- Malicious encryption protection. While education, AG, and cloud backups are vital in preventing ransomware attacks, more direct, boots-on-the-ground solutions should be considered. Heimdal®’s Ransomware Encryption Protection safeguards against malicious encryption attempts by interrupting the kill-chain at IPC level.










 Network Security
Network Security
 Vulnerability Management
Vulnerability Management
 Privileged Access Management
Privileged Access Management  Endpoint Security
Endpoint Security
 Threat Hunting
Threat Hunting
 Unified Endpoint Management
Unified Endpoint Management
 Email & Collaboration Security
Email & Collaboration Security