Contents:
On early Monday, numerous Danish smartphone users reported suspicious SMS-type content originating from a questionable source, allegedly related to Danske Spil. In all instances, a single message would be sent, informing the user of his enrollment in a monthly pay-to-win plan, rescindable via the web. The investigation revealed that the URL enclosed in the SMS points to a game cracks repository that is very popular among fans of pirated content and malware creators.
The Facts in the Case of the Danish SMS Smishing Wave
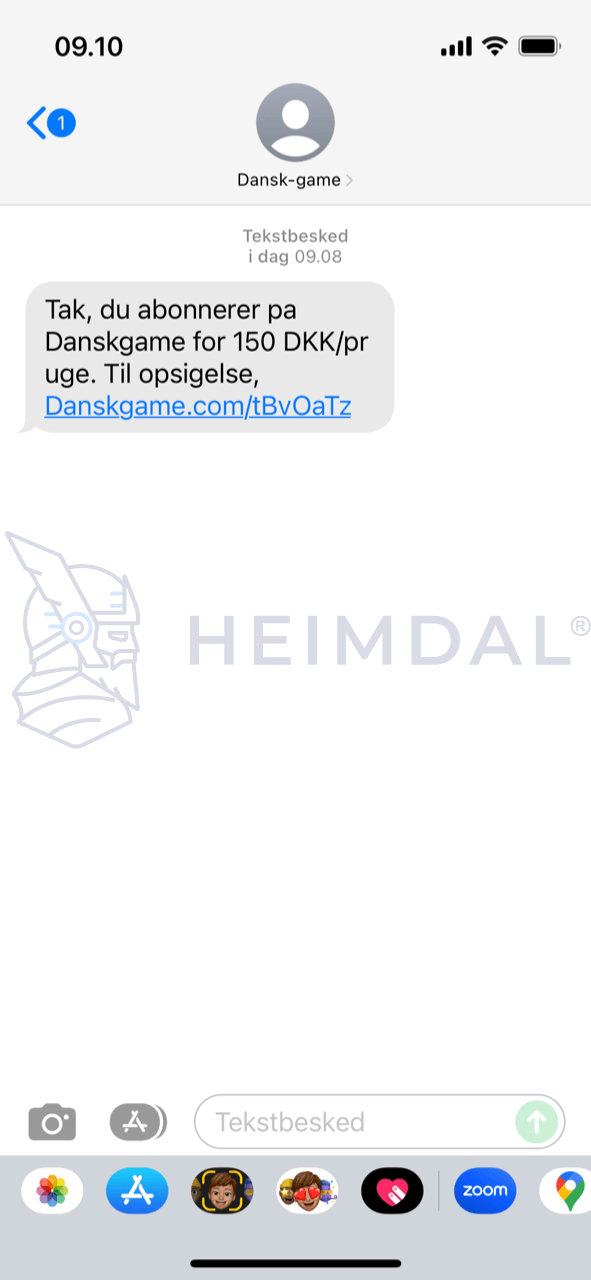
Contacted by an anonymous reader, Heimdal® was made aware that numerous Danish smartphone owners have been flooded by cryptic messages from a user that goes by the moniker of “Dansk-game”. Invariably, the smartphone owners would have received the following SMS:
Translated from Danish to English, the SMS reads:
Thanks for subscribing to the Danskgame (sic!) for DKK 150/month. For termination (sic!), Danskgame.com/tBcOaTz
Heimdal®’s investigation has revealed that none of the users who reported receiving the message have ever participated in such activities or signed digital forms that made them recipients of newsletters, promotions, or other forms of communications from this particular user. At the time of the investigation, the website under scrutiny returned a Code 503 error (i.e. Service Unavailable).
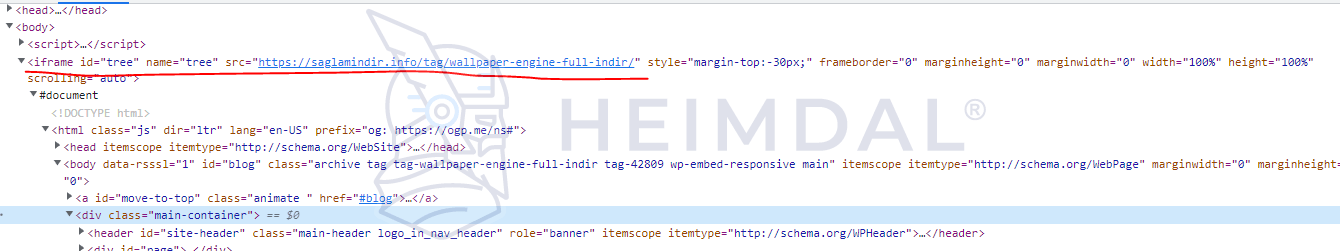
Digital forensics has revealed that the perpetrator has chosen this course of action to reduce their digital footprint. However, a closer examination of the attack URL has unearthed a significant detail – the domain’s HTML code contains a scripted iframe that redirects the user to a secondary domain (i.e., https://saglamindir.info/tag/wallpaper-engine-full-indir/).
The domain in question is quite popular among gamers, being considered a regular treasure trove of DRM busters (i.e., software used to bypass anti-piracy safeguards). Since the website hosts illicit content, it’s only natural for it to double up as a dropping location for (overtly) malicious content. The ramifications of these smishing actions remain largely unknown; with the iframe in place, the threat actor can easily control the user’s end-to-end journey.
For instance, the user can be redirected to a web-hosted resource that can drop spyware on his device. The same mechanism can be leveraged for multiple payloads, including ransomware assemblers, rootkits, trojans, keyloggers, etc. Our investigation has concluded the that smishing campaign targeting Danish users is a zero-day operation, the extent of which is largely unknown at this point in time.
The campaign, although not a novelty, may yet see some traction as it’s capitalizing on a userbase that bands together people from all over Europe (i.e., EUROJACKPOT, one’s of Danish National Lottery’s games extends to nearly 18 countries). However clever the design, it has one major pitfall – the game engagement fee. No lottery program will automatically enroll and charge the user. We advise users to keep this detail in mind the next time they receive a similar text message.
Heimdal® will continue to monitor this event (and related occurrences) and will provide regular updates.
Anti-phishing Cybersecurity Tips
Below, you will find a short, but comprehensive list of tips on how to guard yourself against phishing and smishing attempts.
Avoid opening suspicious-looking ads
Bear in mind that some Google ads you may come across are not malicious. However, this doesn’t mean that you should open everyone, just because the item looks interesting or was on your Wishlist (those can be tracked across apps and platforms). If you do open a link via SMS, make sure it has the HTTPS certificate – check for the padlock icon next to the link.
Deploy and employ next-gen anti-phishing protection
Some phishing attempts, such as the one we’ve discussed, employ a sophisticated anti-detection mechanism, allowing them to get past your antivirus. To counter these threats, you use an anti-malware solution that looks beyond the ‘file’ and ‘code’ level.
Heimdal® Threat Prevention – Endpoint, Heimdal®’s award-winning DNS-filtering solution, can prevent threats from reaching your machine by blocking traffic to and from any malicious C&C server.
Too good to be true!
It’s the golden rule of the Internet: if something looks too good to be true, then it’s, most likely a scam. So, if some website requests very personal info to take possession of some fabulous prize, then it’s a scam. Also, keep in mind that anniversary sweepstakes, such as the one mentioned in the fake ad, are usually announced on the company’s website.
If you liked this article, follow us on LinkedIn, Twitter, Facebook, YouTube, and Instagram for more cybersecurity news and topics.










 Network Security
Network Security
 Vulnerability Management
Vulnerability Management
 Privileged Access Management
Privileged Access Management  Endpoint Security
Endpoint Security
 Threat Hunting
Threat Hunting
 Unified Endpoint Management
Unified Endpoint Management
 Email & Collaboration Security
Email & Collaboration Security