Contents:
A previously undocumented Chinese-speaking threat group has been responsible for targeting telecommunications and IT service providers in the Middle East and Asia.
The threat cluster now identified as WIP19, which stands for work-in-progress, is being tracked in relation to espionage-related attacks aimed at key infrastructure organizations.
Based on their investigations, the cybersecurity company SentinelOne claims these attacks are characterized by the use of a stolen digital certificate issued by DEEPSoft, a Korean company that specializes in messaging solutions, to sign malicious artifacts deployed during the infection chain. In addition, almost all operations performed by the threat actors appear to have been completed in a “hands-on keyboard” fashion, meaning the attacker cares for a stealthy approach.
The cybersecurity firm also noted that some portions of the malicious components employed by WIP19 were authored by a Chinese-speaking malware author known as WinEggDrop, that has been active since 2014. Further, WIP19 is said to have some overlap with another group codenamed Operation Shadow Force but utilizes new malware and techniques.
As the toolset itself appears to be shared among several actors, it is unclear whether this is a new iteration of operation “Shadow Force” or simply a different actor utilizing similar TTPs.
It Starts with Valid Digital Certificates
The cybersecurity company discovered that WIP19 has been using a valid digital certificate which was most likely stolen, given that it has been used to sign legitimate software used by the Korean company DEEPSoft Co., Ltd. The threat actor used the certificate to sign several malware components, some of which were tailor-made for specific targets.
Furthermore, SQLMaggie was also linked to this activity. According to The Hacker News, SQLMaggie was also the subject of an in-depth analysis aimed at calling out its ability to break into Microsoft SQL servers and leverage the access to run arbitrary commands via SQL queries.
Following a scanning process of 600,000 servers worldwide, it was revealed that 285 servers had been infected with Maggie’s backdoor user, spread over 42 countries, predominantly South Korea, India, Vietnam, China, Taiwan, Russia, Thailand, Germany, Iran, and the U.S.
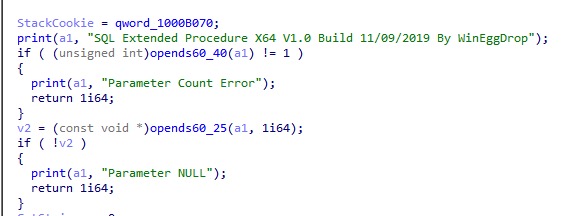
The author’s purported signature in SQLMaggie – Source
Other Components
WIP19`s toolset also includes a combination of a credential dumper, network scanner, browser stealer, keystroke logger and screen recorder. The password dumper consists of two components, one used as a loader, and the other as a dumper.
The analysis also specifies that WIP19 has been observed utilizing a less common DLL search order hijacking of explorer.exe to load a keylogging and screen recording component internally named ScreenCapDll_x64. The ScreenCap malware performs checks involving the victim’s machine name, indicating it is specially crafted for each deployment.
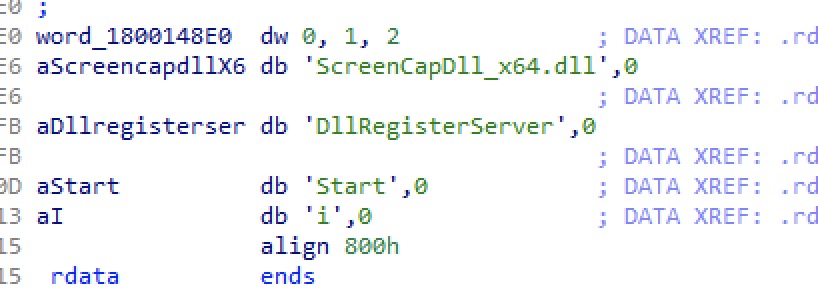
The keylogging and screen recording components – Source
The fact that the attacks have precise targets, the telecom sector being singled out, and are low in volume suggests the primary motive behind the campaign may be to gather intelligence, due to the amount of sensitive data these companies hold.
If you liked this article, follow us on LinkedIn, Twitter, Facebook, Youtube, and Instagram for more cybersecurity news and topics.


 Network Security
Network Security
 Vulnerability Management
Vulnerability Management
 Privileged Access Management
Privileged Access Management
 Endpoint Security
Endpoint Security
 Threat Hunting
Threat Hunting
 Unified Endpoint Management
Unified Endpoint Management
 Email & Collaboration Security
Email & Collaboration Security









