Contents:
An advisory recently published by multiple US federal agencies shows that Chinese state-backed cybercriminals have attacked and impacted important telecommunications organizations and network service providers in order to snatch credentials and collect sensitive data.
This joint cybersecurity advisory was coauthored by the National Security Agency (NSA), the Cybersecurity and Infrastructure Security Agency (CISA), and the Federal Bureau of Investigation (FBI). According to it, Chinese cybercrime organizations have continued to abuse publicly known flaws to compromise anything from unsecured small office/home office (SOHO) routers to medium and even big enterprise networks.
Once the devices were compromised, the attackers used them as command-and-control servers and proxy systems to break into other networks as part of their own attack infrastructure.
Upon gaining an initial foothold into a telecommunications organization or network service provider, PRC state-sponsored cyber actors have identified critical users and infrastructure including systems critical to maintaining the security of authentication, authorization, and accounting.
Following the discovery of a critical Remote Authentication Dial-In User Service (RADIUS) server, malicious actors obtained access to the underlying SQL database and used SQL commands to dump the credentials, which included both cleartext and hashed passwords for user and administrative accounts.
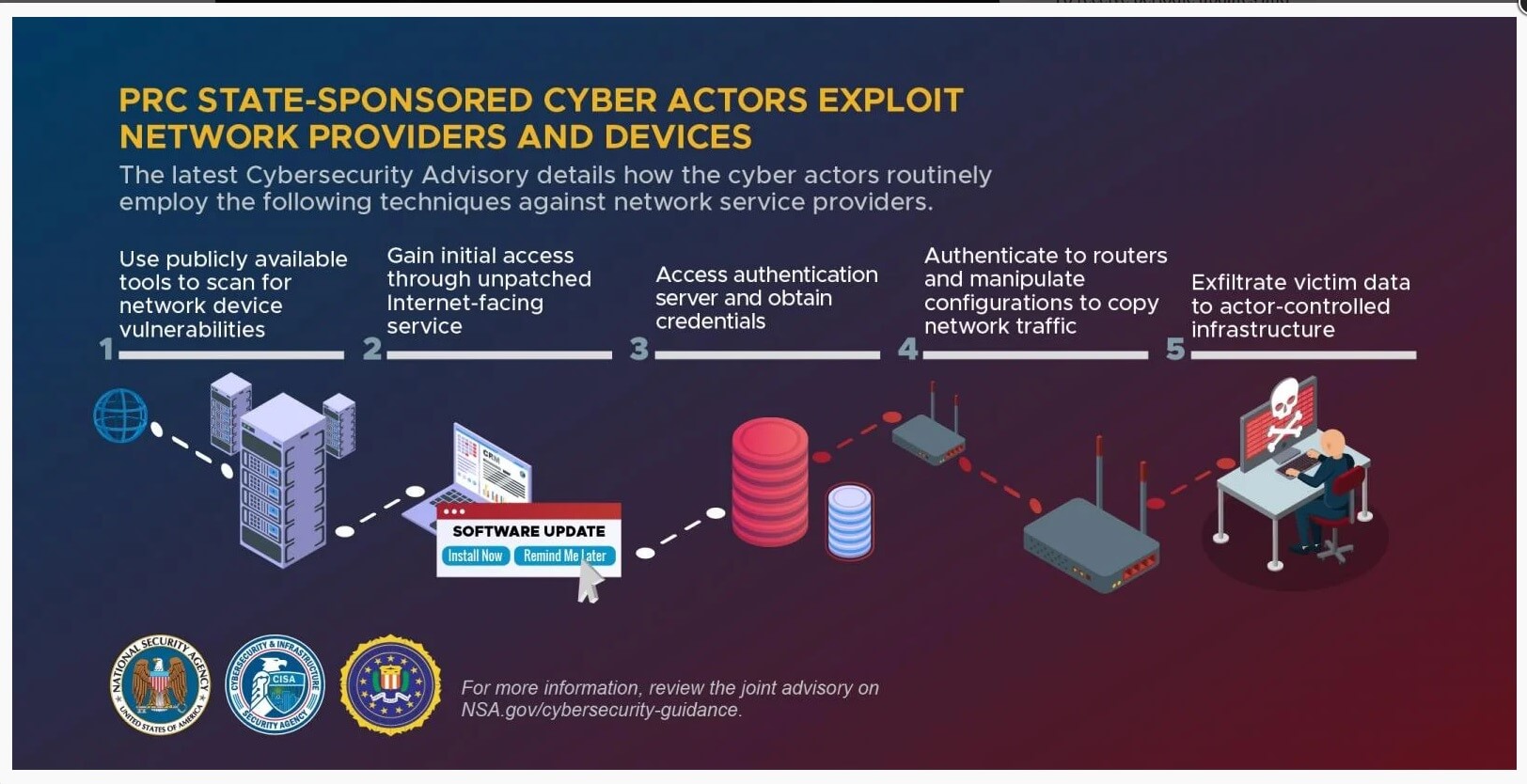
Armed with valid accounts and credentials from the compromised RADIUS server and the router configurations, the cyber actors returned to the network and used their access and knowledge to successfully authenticate and execute router commands to surreptitiously route, capture, and exfiltrate traffic out of the network to actor-controlled infrastructure.
NSA, CISA, and the FBI consider the common vulnerabilities and exposures (CVEs) listed below to be the network device CVEs most frequently abused by People’s Republic of China (PRC) state-sponsored cybercriminals since 2020.
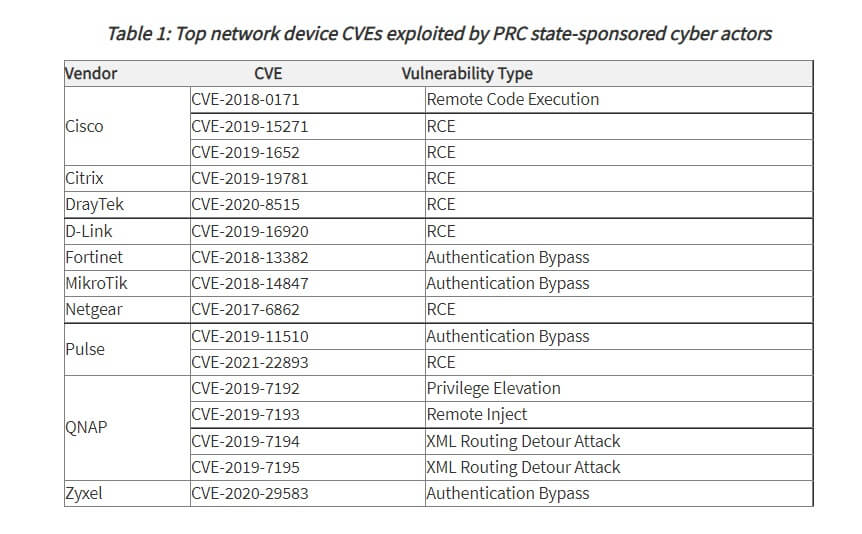
China-backed hackers have established broad infrastructure networks as a result of using these vulnerabilities, allowing them to compromise an even broader range of public and private sector organizations.
The three federal agencies encourage companies to establish a set of mitigation strategies in order to reduce the likelihood of cyberattacks compromising their networks. Some of them are:
- Update and patch systems and products as quickly as possible after fixes are published. To optimize and speed up the process, consider using a unified patch management solution.
- Remove or separate any suspected compromised devices from the network right away.
- Apply strict password policy, enforce password complexity, change passwords on a regular basis, and conduct frequent account reviews to ensure compliance.
- Separate networks to restrict or prevent lateral movement.
- Implement multifactor authentication (MFA) for all users, without exception.
Check out all the recommendations here.
If you liked this article, follow us on LinkedIn, Twitter, Facebook, Youtube, and Instagram for more cybersecurity news and topics.


 Network Security
Network Security
 Vulnerability Management
Vulnerability Management
 Privileged Access Management
Privileged Access Management
 Endpoint Security
Endpoint Security
 Threat Hunting
Threat Hunting
 Unified Endpoint Management
Unified Endpoint Management
 Email & Collaboration Security
Email & Collaboration Security










