Contents:
Fakecalls, an Android banking malware, has a powerful feature that allows it to hijack calls to a bank’s customer service number and connect the target directly with the malware’s operators.
More on Fakecalls
According to cybersecurity experts at Kaspersky, the Fakecalls malware first appeared last year and has been observed attacking users in South Korea, specifically clients of widely known banks such as KakaoBank and Kookmin Bank (KB).
Despite the fact that it has been operative for some time, the banking trojan has received little attention, most likely due to its limited target geography, notwithstanding its fake call function, which represents a new step in the evolution of mobile banking threats.
Fakecalls M.O.
Fakecalls poses as a well-known financial institution’s mobile app and shows all the trademarks of the entity it impersonates, including the official logo and the customer support phone number. When the victim attempts to contact the bank, the trojan interrupts the connection and displays its own call screen, which is nearly identical to the authentic one.
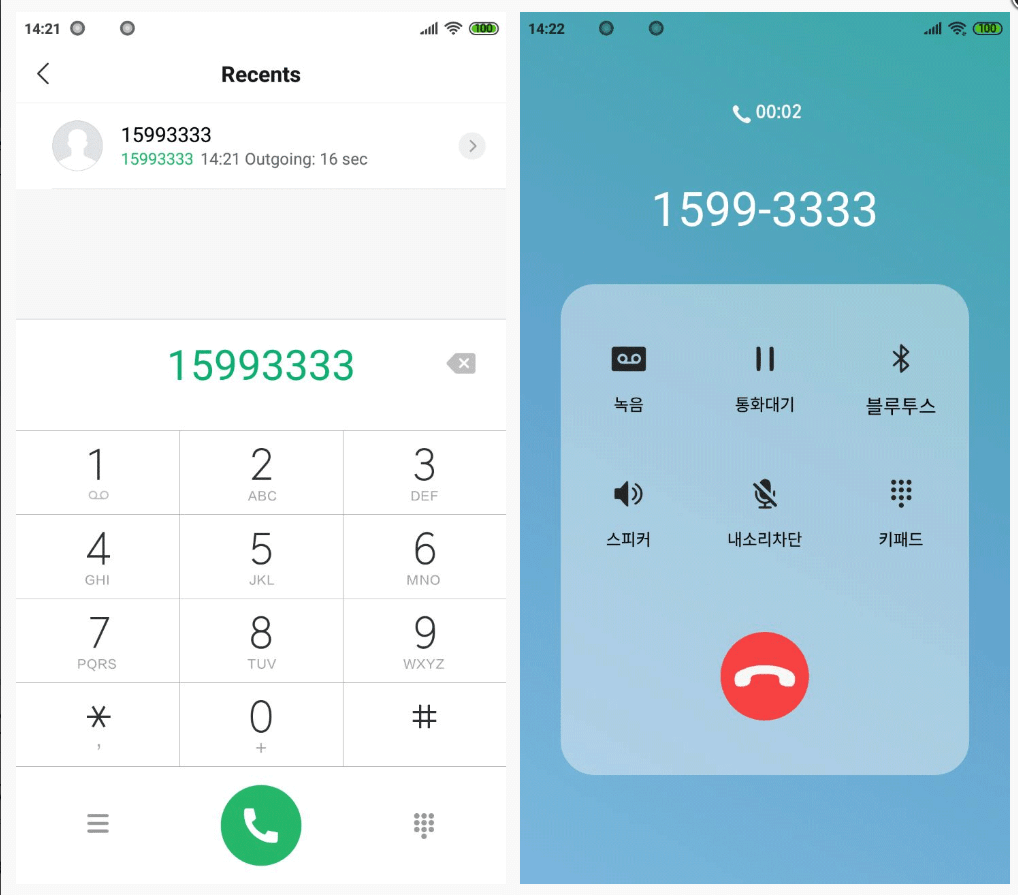
While the target sees the bank’s actual phone number on the screen, the call is, in fact, with the threat actors who can impersonate the bank’s customer service agents and collect data that will allow them to get access to the victim’s money.
This is possible because Fakecalls asks for several authorizations during installation, including access to the contact list, microphone, camera, location data, and call handling.
Kaspersky researchers examined the malware and discovered that is also able to play a pre-recorded message similar to those used by banks to welcome people seeking assistance:
The creators of the Fakecalls malware recorded a few sentences that banks frequently use to inform their clients that an operator will pick up their call as soon as one becomes available.
Hello. Thank you for calling KakaoBank. Our call center is currently receiving an unusually large volume of calls. A consultant will speak to you as soon as possible. <…> To improve the quality of the service, your conversation will be recorded.
Welcome to Kookmin Bank. Your conversation will be recorded. We will now connect you with an operator.
Spyware Toolkit
The malware’s permissions enable malicious actors to:
- keep an eye on the victim by broadcasting real-time audio and video from the device,
- visualize its location,
- copy contacts, pictures, and videos,
- read text message history.
These permissions allow the malware not only to spy on the user but to control their device to a certain extent, giving the Trojan the ability to drop incoming calls and delete them from the history. This allows the scammers, among other things, to block and hide real calls from banks.
While the threat actor behind Fakecalls has been noticed to support only the Korean language, which makes it easy to identify if the compromised device functions with a different system language, its developers could add more to expand to other areas.
How to Stay Protected
- Download applications only from official stores and do not authorize installations from questionable sources.
- Pay attention to the permissions that apps request and whether they are truly necessary. Reject the permissions that could be dangerous, such as access to calls, SMS, and accessibility.
- Don’t provide sensitive information over the phone. Legitimate financial institutions will never request your online banking login information, PIN, card security code, or confirmation codes via text message. If you suspect that something might be wrong, visit the bank’s official website to find out what questions employees are or aren’t allowed to ask.
If you liked this article, follow us on LinkedIn, Twitter, Facebook, Youtube, and Instagram for more cybersecurity news and topics.










 Network Security
Network Security
 Vulnerability Management
Vulnerability Management
 Privileged Access Management
Privileged Access Management  Endpoint Security
Endpoint Security
 Threat Hunting
Threat Hunting
 Unified Endpoint Management
Unified Endpoint Management
 Email & Collaboration Security
Email & Collaboration Security








