Contents:
BYOD (Bring Your Own Device), also known as BYOT (Bring Your Own Technology) refers to a security policy of allowing employees to bring personally own devices such as laptops, tablets, and smartphones in the workplace, and to use them to access confidential information and applications belonging to an organization.
The term “Bring Your Own Device” (BYOD) became popular in 2009, thanks to the US technology firm Intel, which identified an increasing trend among its employees to bring their own devices to work and connect them to the corporate network.
BYOD Advantages and Disadvantages
Due to the fact that almost every human being is currently owning and using devices such as smartphones, tablets, and computers in their daily lives, more and more organizations have started to allow employees to bring their own devices to work.
Even if studies had shown that productivity increases and costs are diminished, the idea of BYOD is still rejected by some companies due to security concerns.
As with any new technology or trend, there are advantages and disadvantages. If you’re considering implementing a BYOD policy, it might be a good idea to weigh the pros and cons before making a decision:
BYOD Advantages
- You are saving money. With a BYOD policy, companies can save money as they are not responsible for providing the employee with phones or laptops. It doesn’t entirely cut down costs as they still have to invest in mobile device management (MDM) software to protect corporate data from several risks and threats.
- Increased productivity. Employees are more comfortable with their personal devices than with organizations’ outdated devices that are prone to malfunctions and require a longer start-up time. Employees who are familiar with their devices tend to access them more quickly and efficiently, allowing them to accomplish more tasks in less time. Furthermore, employees take better care of their personal devices and keep them up to date.
- Flexibility and independence. An employee can use the devices they seem suitable for work purposes without having to follow up with the organization’s IT department for the newest device. They also have the freedom to work after office hours, while traveling, or remotely.
- Increased employee satisfaction and job satisfaction. The employee can use the device they have chosen as their own instead of one the company selected. It also allows them to carry one device rather than one for work and one for personal purposes.
- Potential future employees will find it appealing. BYOD can be used to attract new employees. According to a survey, more than 44% of job seekers view an organization more positively if it supports their device.
- Better employer-remote employee relationships. By facilitating BYOD, an employer will be able to reach all of their employees, no matter where they are, on a device that’s probably already in their pocket or hand.
- Less Training. Employees are more familiar with their devices’ OS and functions as they also spend time using them outside working hours. Therefore, they will not need training on how to use a smartphone or a laptop.
BYOD Disadvantages
- Devices used by employees are vulnerable to theft, loss, or damage. When employees bring their own devices to work, any access to the corporate network can be dangerous, whether the employee performs simple tasks such as logging into a work email account or more sensitive activities like accessing banking or HR documentation.
Once an attacker gains access to a stolen or lost gadget they can steal data stored locally on the device, utilize stored credentials to access corporate networks, or delete data.
- Device infection. Smartphones are frequently infected with malware that can spread to other devices connected to the company network, and in most cases, users are not even aware of the infection. This type of infection can lead to data loss and downtime.
According to experts, on desktops or laptops, operating system vulnerabilities pose the highest risk as most users forget to update with the latest security patches.
- Improper antivirus software, firewalls, or other specialized security software. Some employee equipment may not be protected at all, while others may be protected by ineffective free-of-charge or dubious antivirus programs.
- Devices used for both personal and professional purposes. A company has no control over the websites its employees visit, some of which may be malicious or compromised, or the applications they install. Furthermore, smartphones can be used by other family members who may connect to unsecured wi-fi or accidentally share confidential company information.
- Device incompatibility problems. Employees use a variety of devices that run on various platforms. Thus, issues such as version discrepancy, competing platforms, wrong setups, mismatched hardware, unsupported applications or protocols are common and can substantially stymie the process of effectively implementing BYOD.
- Employee Privacy. In order to make BYOD work, the IT team of a company may have to get control over its employees’ devices to install, supervise or configure an MDM (Mobile Device Management) system to protect the confidentiality of corporate data. It may be difficult because employees can feel monitored and believe that their sensitive information is exposed.
- Jailbroken devices. Jailbreak is the process of removing the limits set by a device manufacturer, typically to enable unauthorized third-party software to be installed. This raises the possibility of an employee unintentionally installing malicious software on their own device.
In order to mitigate these risks, an employer must come up with a BYOD security policy that works for the needs of both organization and employees.
Best Practices When Implementing a BYOD Security Policy
Educate Your Employees about Security
Most of the time, the BYOD-related security risks involve human error. It is important to define a BYOD security policy but it’s essential and mandatory to take the time to educate your work staff about it. Your employees should understand what they can and cannot do on their personal devices, why the security measures matter, and what happens if they break the policy.
Your employees must understand that by implementing a BYOD policy, the entire organization will be protected from data breaches and other cybersecurity threats.
Determine Which Devices Are Acceptable and Proper Use
Make it clear for your employees which devices are adequate, including operating systems (Android OS or Apple iOS) and device types. This way, your IT team won’t have to deal with compatibility problems with multiple types of devices.
Also, determine the occasions of acceptable use of personal devices at the office. Employees can and will definitely try to use personal features of their smartphones or computers while at work. To address this issue, you could consider employing a company app that requires users to log in before they can access corporate data.
Set Up Security Requirements
Organizations should encourage their employees to get used to following security best practices by making necessary security measures mandatory.
A good BYOD policy should require employees to keep their personal devices password-protected non-stop (and also use multi-factor authentication), consider using a Virtual Private Network (VPN) and antivirus solutions in order to reduce the chances of exposing corporate data.
Ask for Registration with the IT Department
The visibility of the devices connected to the network is improved when they are registered with the IT department. This can easily be included in the onboarding process for new employees and devices.
This way, a sysadmin can quickly compare the list of registered devices to the list of connected devices to detect unauthorized connections.
Determine Who Owns What Data
On devices that are under a BYOD policy, we can find a combination of personal information and corporate data including contacts, files, calendars, and work emails. Employees must be informed that their private data will continue to be exclusively under their control. In addition, indicate what data is owned by your organization.
Implement Mobile Device Management (MDM) Software Application
Mobile Device Management (MDM) software allows IT to automate any device that is directly connected to an organization’s network, such as laptops, printers, smartphones, tablets, and further control and secure their administrative policies.
When a device is stolen, lost, or compromised, MDM software provides an infallible procedure to remove confidential data from the phone remotely.
Even if storing confidential data such as corporate financial information on a BYOD is not recommended, such devices may come into contact with sensitive data.
Consider an Employee Exit Policy
It is important to know that corporate data must be removed from a device belonging to an employee who decided to leave an organization. One approach would be to create a set of exit protocols for securely removing company data while maintaining the integrity of the employee’s personal information.
Before the removal of corporate data from your employee’s device don’t forget to back up their data and content.
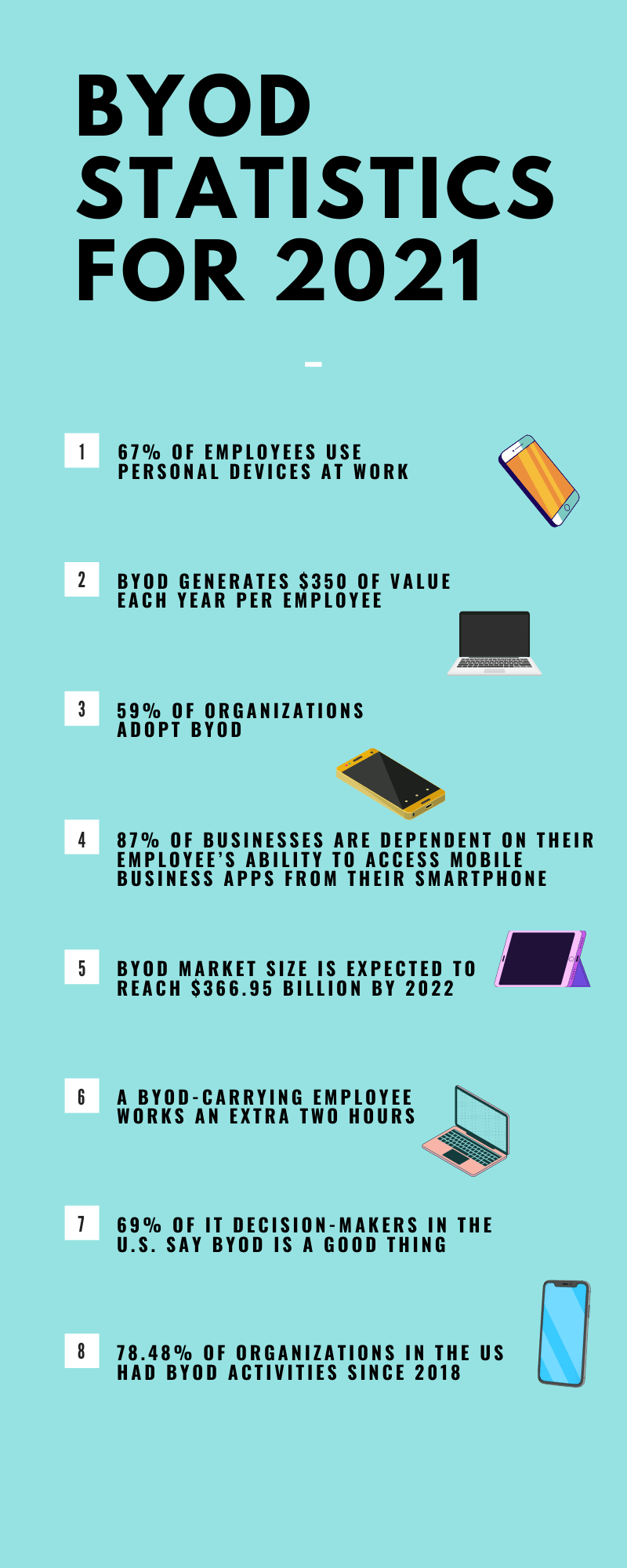
Wrapping Up…
A Bring-Your-Own-Device (BYOD) policy boosts productivity and lowers expenses, but cybersecurity is more complicated than ever as security experts confront with a new and dynamic landscape that appears to have no limitations. More and more organizations started to admit the importance and value of employee devices at the workplaces, but also the necessity of strong BYOD security policies to keep businesses safe and secure.
Heimdal Security aims to make the internet a safer place for all organizations, and for individuals as well, and to offer the latest in cybersecurity protection against advanced cyberattacks. Our security solutions are designed to work with your company’s needs and budget.











 Network Security
Network Security
 Vulnerability Management
Vulnerability Management
 Privileged Access Management
Privileged Access Management  Endpoint Security
Endpoint Security
 Threat Hunting
Threat Hunting
 Unified Endpoint Management
Unified Endpoint Management
 Email & Collaboration Security
Email & Collaboration Security








