Contents:
Businesses are becoming increasingly aware of the cyber-threat represented by bot attacks. In fact, over 70% of organizations in the e-commerce, entertainment, travel, and financial services sectors display a common understanding of the most common types of operations, such as card cracking or credentials stuffing. What is more, 76% of them state that they have been attacked by bots in the past.
However, as little as 1% of companies are aware of the complexity of this issue, which even involves dark marketplaces where stolen credentials can be commercialized for a profit. This is in part because higher-profile attacks have been taking up headlines for quite some time now, which might have business owners thinking that ransomware is the only danger out there.
Nevertheless, that couldn’t be further from the truth. Although not mediatized as often, bot attacks can be equally difficult to mitigate and even more damaging in the long run than a ransomware campaign. For this reason, I will elaborate more on this topic in the following lines.
What are bot attacks? How do they work? Are bot attacks easy to detect? Find out the answer to all of these questions and learn how to protect your website from bot attacks in the sections below.
Bots: The Good, The Bad, and The Ugly
Before I dive into the conversation on botnets, bot attacks, et al., I should first clarify what the term ‘bot’ actually stands for. The cyberworld has many names for them, the most academic of which is Internet robots. However, you might have heard people talking about spiders or crawlers in some contexts. Yep, those are bots too.
Not all bots are born bad. For instance, web crawlers (or spiders) are the good guys who search through sites and gather information from them. Google uses them to map out the page structure of a website. Examples in this category don’t stop here. Are you familiar with those handy instant chat replies that help brands, establishments, or even individual users better manage their online messaging needs? They’re good bots too, and they’re here to benefit us.
However, some bots out there use their powers for evil. Or rather, hackers do it through them. Ill-intended third parties outside your organization can use networks of infected computers known as botnets to gain control of your system. This is a type of self-propagating malware with worm-like capabilities, which brings me to the topic at hand: bot attacks.
What Are Bot Attacks?
When hostile third parties take advantage of a botnet to attack your systems and gain unlawful access to sensitive data, you might have a bot attack on your hands. In the following sections, I will go over the bot attack meaning, the mechanics of the botnet behind it, and some of the most popular types of bot attacks you need to watch out for.
Bot Attack Meaning
Simply put, the term bot attack refers to any instance in which hackers make use of Internet robots to illegitimately enter a network, obtain private data from it, and wreak general havoc within it. As mentioned above, these bad bots are usually part of an interlinked system of compromised machines known as a botnet.
Attackers infiltrate the computers with the help of malware, then use them for malevolent purposes through standard-based communication protocols. These include, but are not limited to, Hypertext Transfer Protocol (HTTP) and Internet Relay Chat (IRC). Besides being manipulated by their creators, botnets are also rented out to other cybercriminals such as ransomware distributors.
Botnet Mechanics
To understand how a bot attack unfolds, it is vital to also be familiar with the mechanics that power them. Thus, next I will present how hackers create and control a botnet.
Any device that can connect to the Internet is a potential target for botnet recruitment, the process of adding devices to the collection of infected machines. Thus, desktop computers and mobile devices are both viable targets.
Other less expected, but equally vulnerable types of devices that can become unwilling participants to a botnet are:
Internet of Things (IoT) devices
- wearable gadgets (smartwatches, fitness trackers)
- smart home devices (speakers, TVs, cameras, thermometers)
- vehicle infotainment systems
Internet infrastructure hardware
- Wi-Fi routers
- network bridges
- web servers
Also known as zombie computers, these malware-ridden devices allow hackers to carry out larger-scale attacks. Their purpose is to mindlessly fulfill commands sent out by the bot herder, which is the leader of the hijacked machines. Attack instructions are then deployed by the bot herder via remote programming through the Command-and-Control (C&C) server.
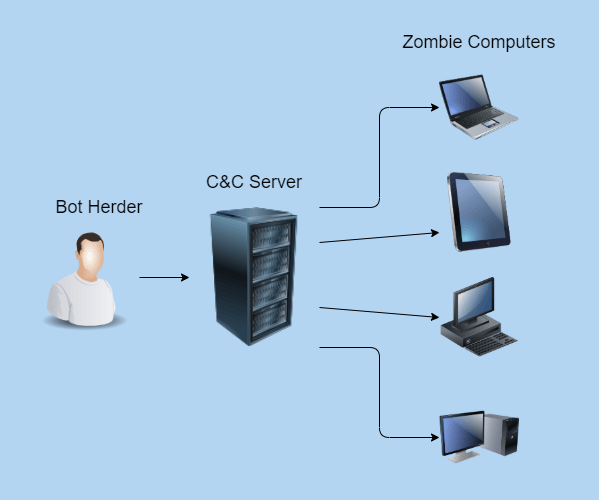
The C&C server is the botnet’s main source of orders, and it can function according to one of two possible models:
- Client-server, a centralized model that sends commands through IRC websites, domains, or networks. It is a dated model that runs with a single bot herder, which leaves the network open to being discovered and is thus undesirable for contemporary attackers.
- Peer-to-peer, a decentralized model that imprints all zombie computers with the instructions and thus hides the bot herder’s identity better. The P2P approach is preferred by hackers nowadays, as it can evade the detection of more modern cybersecurity measures.
Types of Bot Attacks
Bot attacks can come in many shapes and sizes, depending on what the hackers orchestrating them want to achieve. I’ve listed three of the most common types of bot attacks below so that you know what to expect when bad bots target your enterprise.
- Brute force attacks, which consist of running programs that exploit weak user passwords through credential stuffing and dictionary attacks. By trying several thousand password variations at a time, these programs eventually crack accounts that are not properly protected.
- Phishing campaigns, which rely on ill-intentioned social engineering practices that imitate the branding of trusted companies or users within the organizations. The goal of this operation is to persuade users to click on suspicious links or download infected attachments and spread the threat throughout the network, such as it is the case with Emotet malware, for example.
- Distributed denial of service (DDoS), which depends on flooding target web servers with traffic from zombie computers, overloading the system and shutting down processes. Bad bots swarm the victim website and crash it, which results in it and all associated services being taken offline.
Are Bot Attacks Easy to Detect?
According to The Atlantic, bots are responsible for more than half of the total traffic registered on the web. What is more, their online behavior seems to mirror that of human visitors, which makes them increasingly difficult to detect.
The reason for this is the fact that bots have evolved tremendously over the last few years. While first-generation bots performed simple automated tasks and were easily identifiable, their more modern iterations are extremely convincing in cosplaying people online. They can even mimic actions such as non-linear mouse movements.
So how can you tell if you’ve been the victim of a bot attack? Decreased machine performance is the first sign. Of course, it’s normal for our devices to slow down sometimes, especially when we’re multitasking like crazy on them. Nonetheless, this can sometimes be a cause for concern.
When you want to protect your organization against bot attacks, how much lag is too much lag? Here are a few of the most prevalent telltale signs of bot attacks:
- programs behave more sluggish than normal,
- start-up and shut down take longer than before,
- devices crash for no apparent reason,
- your Internet connection slowed down significantly,
- the fan overheats even when the computer is idle,
- settings changed out of the blue and can’t be reversed,
- suspicious messages are being sent from your accounts,
- and the browsers in your network feature unknown components.
How to Prevent Bot Attacks
As it is the case with any other type of cyber-threat, prevention is the best medicine in the case of bot attacks too. In this section, I will go over how to protect your website from bot attacks, as well as have other potential access points covered.
1. Monitor Incoming Traffic and Investigate Its Sources
Getting more traffic on your website might sound like a dream come true for any business owner, but is that really the case? Here are a few unmistakable indications that you are dealing with an onslaught of bad bots:
- high bounce rate
- low conversion rate
- unexplained spikes
If you notice any or all of these happening and cannot trace them back to a reliable source, it’s time to take more palpable measures.
2. Keep an Eye on Every Potential Bad Bot Access Point
The fact that bot attacks favor websites is not a secret, but this doesn’t mean that you should overlook other access points they can find into your enterprise’s network. Exposed APIs and mobile apps are equally vulnerable to intrusions of this kind. Therefore, you should always keep an eye on them as well.
Another critical detail to watch out for are failed login attempts, which you might say are not unheard of in organization networks. However, they do become problematic when there is a rapid growth in their volume. This is why you should always set global threshold alerts for this type of occurrence.
3. Implement a Company-Wide Password Hygiene Policy
Most employees nowadays are aware of the importance of complex passwords that contain both lowercase and uppercase letters, as well as numbers and symbols. Still, having a company-wide password hygiene policy can make all the difference in this modern cybersecurity landscape when it comes to preventing bot attacks and other looming threats.
Train your staff to never use the same password for multiple accounts, both personal and work-related. Another significant aspect of this discussion is regularly changing credentials to ensure they aren’t stolen during breaches. While having a separate password for every single program you use daily might be tricky, this is nothing a good password manager can’t fix.
4. Practice the Principle of Least Privilege Among Employees
While we’re on the topic of credentials, allow me to also stress the importance of practicing the principle of least privilege within your organization. This will limit admin rights in your business network to a few designated individuals, while at the same time giving personnel the necessary level of access to complete their daily tasks. In this way, you can reduce the impact of bot attacks, especially those of brute force and phishing persuasion.
Implementing and actively applying POLP can be a time-consuming affair for your admin, but it doesn’t need to be that way. Our Heimdal™ Privileged Access Management is designed to facilitate this process for the network administrator, as well as immediately de-escalate rights when suspicious activity is detected.
5. Use a Complete Cybersecurity Solution to Cover All Bases
One major takeaway you need to consider when it comes to dealing with bot attacks is that they are versatile. Not only are they adapting to mimic our behavior online to evade being discovered, but they can also infect your enterprise through a variety of gateways.
This is why you will need a complete cybersecurity solution such as EDR Software, our package that covers all bases. It combines the functionalities of Heimdal Next-Gen Antivirus & MDM, a next-generation antivirus, and Heimdal Threat Prevention, a multi-layered threat prevention tool.
Heimdal™ Endpoint Security Software benefits from Heimdal’s proprietary DarkLayer Guard, which will protect your machines against the HTTP exploits that make bot attacks so successful. In addition, its firewall is highly effective in the case of brute force attacks. Finally, Process Behavior-based scanning and VectorN Detection will spot even the best-hidden threats out there, which is good to have around considering how smart and adaptable bots are becoming.
Conclusion
Bot attacks are an often-overlooked threat hiding in the shadowy corners of the cyberworld. But while they might not seem as dangerous as ransomware or Trojans, the damage they can inflict is equally prominent. Therefore, protecting your enterprise against them should be your priority, and Heimdal is here to help. Besides my advice, our security solutions might be just what you need to polish your online shields even more.
Got any comments or questions? As always, feel free to leave your suggestions and inquiries in the comment section below. I look forward to reading them all!










 Network Security
Network Security
 Vulnerability Management
Vulnerability Management
 Privileged Access Management
Privileged Access Management  Endpoint Security
Endpoint Security
 Threat Hunting
Threat Hunting
 Unified Endpoint Management
Unified Endpoint Management
 Email & Collaboration Security
Email & Collaboration Security









