Contents:
Marked by significant geopolitical shifts and unrest, 2022 has galvanized the cybersecurity landscape as well; war-profiteering fueled by endless media disputes has allowed the threat actors not only to operate unhindered but also to find safe harbor with states that choose to turn blind eye to cyber-criminal activity.
2023 will most likely be just as challenging as the previous few years, but I’m confident that the cybersecurity market has the right tools to deal with the constantly shifting cybercrime landscape and new/consolidated threats, whether we’re talking about supply chain attacks, ransomware, deepfakes or cyber espionage.
Glancing back at 2022’s Cyber Threats
The “new normal” foisted upon organizations as they accommodate a remote workforce has left them vulnerable to new attack vectors and facing huge alterations in the threat landscape, according to our annual Threat Report.
Worms, Trojans, and infected JS malware were the ones our SOC Team encountered most often. Although these varieties of malware often appear legitimate, they are actually designed to destroy, disrupt, or steal data, and they can quickly seize control of a device.
Looking more closely at how the cybersecurity landscape altered in 2022, we couldn’t help but notice that our clients have successfully been safeguarded from major cyber events thanks to our unified corporate security suite.
Without further ado, here’s a sneak peek of what Heimdal®’s 2023 Cyber-Security & Threat Intelligence Report brings to the table. We tackled the main areas of last year’s cybersecurity interests by putting together a list of:
- Most Important Cyberattacks.
- The Most Powerful Statistics of 2022.
- Threatscape Predictions for 2023.
You can download the Heimdal® CyberSecurity & Threat Intelligence Report 2023 here.
Cyber Threat Report 2023 Key Takeaways
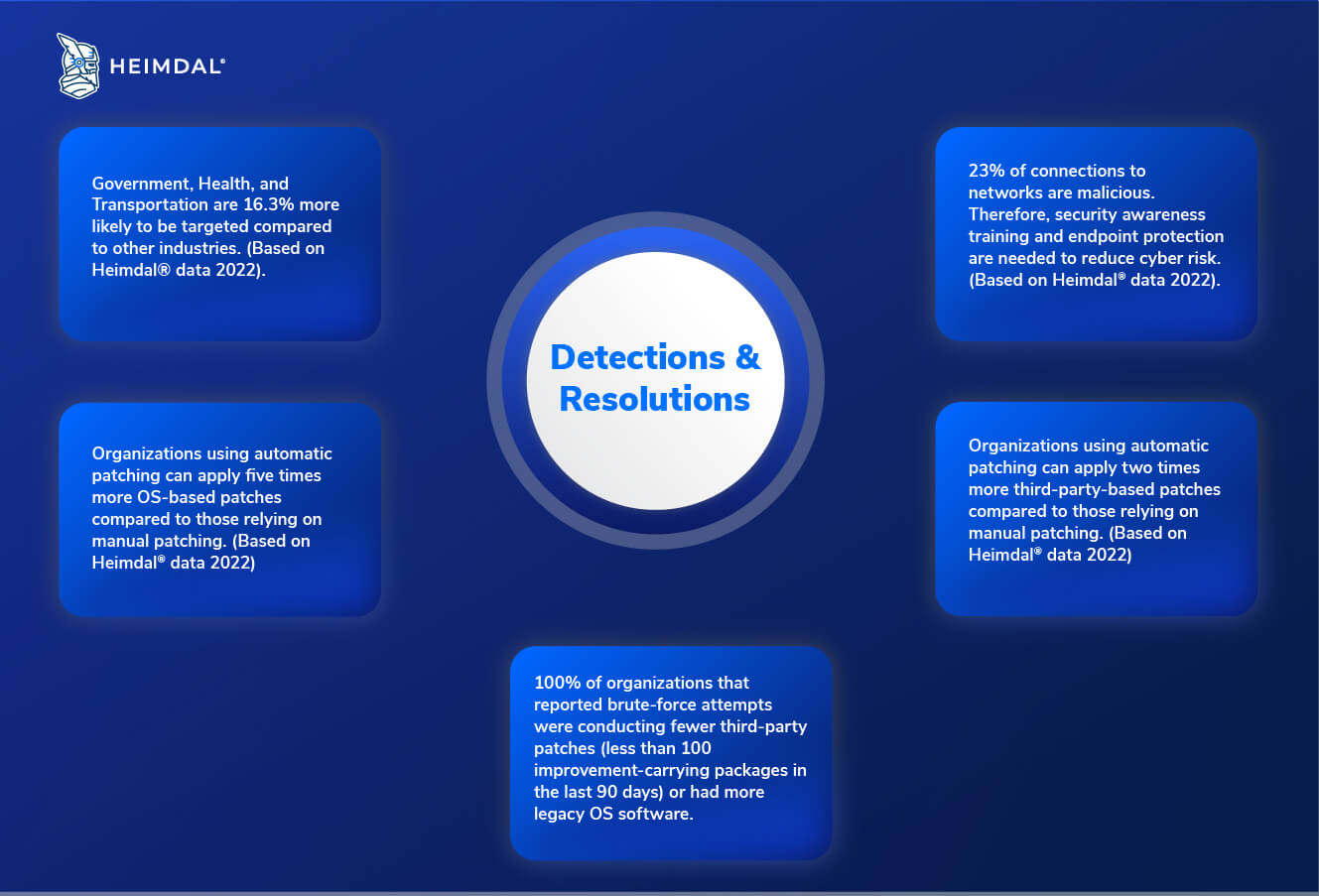
- 100% of organizations that reported brute-force attempts were conducting fewer third-party patches (less than 100 improvement-carrying packages in the last 90 days) or had more legacy OS software.
- Government, Health, and Transportation are 16.3% more likely to be targeted compared to other industries. (Based on Heimdal® data 2022).
- 23% of connections to networks are malicious. Therefore, security awareness training and endpoint protection are needed to reduce cyber risk. (Based on Heimdal® data 2022).
- Organizations using automatic patching can apply five times more OS-based patches compared to those relying on manual patching. (Based on Heimdal® data 2022)
- Organizations using automatic patching can apply two times more third-party-based patches compared to those relying on manual patching. (Based on Heimdal® data 2022).
Detections & resolutions
- 170,000,000 million DNS, HTTP, and HTTPS attacks were blocked by Heimdal® in 2022.
- 50% of network-based attacks originated from .co Top-Level Domains.
- 167% YoY (i.e., 2021 – 2022) increase Russia-based cyberattacks.
- 10% of all emails hide malicious content.
- 23.8% of all emails scanned by Heimdal® had a Critical severity score.
- 6.35 network-based attacks per day were carried out between January 2021 and October 2022.
- HTML endpoint-based malware and infected JavaScript were the most frequently detected attacks.
- Custom attack ‘stationary’. Threat actors such as Cobalt Therapin, employed victim-tailored spear-phishing forms to increase the odds of success.
Key Predictions of Cyber Threats and Trends for 2023
- Centralized cybersecurity architectures will replace point-based solutions.
- Overemphasis on tool automation and asset visibility.
- SOAR and SIEM hybridization to replace conventional threat-hunting tools and approaches.
- HVTs, MSPs in particular, will face additional challenges in protecting against multi-surface attacks.
- ‘Web of Ransomware’ will make it difficult for authorities to track down cyber-criminals.
- Time vs. effect. Attackers will spend more time staging attacks in order to increase likelihood of success.
- Russia – Ukraine conflict to become a breeding ground for cyber-criminals.
- A rise in state-sponsored cyberespionage.
- Deepfakes to play a key role in social engineering.
In 2022 we witnessed not only a rise in cyber-threats all across the grid, but also increased friction when it comes to embracing non-traditional malware detection & mitigation tools. Despite the industry’s having a clear-cut trajectory, automatizations, be them all-inclusive or partial, carry inherent challenges and limitations (e.g., SIEM solutions are prone to alert fatigue, while SOAR-type responses are confined to low- and medium-level security incidents).
Other factors that encumber the adoption and implementation processes are licensing, medium- to long-term costs (i.e., setup, configuration, upscaling, and maintenance), and workforce, the latter being considered a deal-breaker for organizations seeking to embrace SIEM, SOAR, or hybrid approaches.
Such challenges highlight the importance of enhancing cyber resilience across society; nevertheless, cybersecurity requires more than just precautions; it is also critical to educate employees and the broader public about cyber protection and how to stay safe from such threats.

If you want to know more about what 2023 might bring in terms of cybersecurity you should read Morten’s article on the top trends we’ll see in cybersecurity.
Interested in learning more about the Heimdal® way? Join us at UK CyberWeek Conference & Expo (April 4-5th). We’ll be waiting for you at stand #A6 at the Business Design Centre, in London. Don’t miss the chance to see our award-winning products in action, or just meet the team. We will also be giving away a luxury, super-car driving experience to one lucky delegate! Could that be you?


 Network Security
Network Security
 Vulnerability Management
Vulnerability Management
 Privileged Access Management
Privileged Access Management
 Endpoint Security
Endpoint Security
 Threat Hunting
Threat Hunting
 Unified Endpoint Management
Unified Endpoint Management
 Email & Collaboration Security
Email & Collaboration Security