Contents:
Alexander Graham Bell’s invention of the telephone back in 1876 marked one of the most important cultural revolutions of mankind – its invention and everything that followed afterwards (the invention of the first dial phone, the apparition of the first mobile/cellular phone, the apparition of the 2nd, 3rd, 4th and 5th generation technologies) allowed us to communicate faster and have almost everything we need to know or acquire at the touch of our fingertips. At a certain point in mobile phones’ evolution, the Android operating system appeared – with an intuitive interface and various connectivity options, it is used on 74.43% of devices worldwide. Despite Android’s popularity, Android permissions – the principle on which it operates, put users’ mobile security at certain risks. Let’s find out more.
Android Permissions List
Like I’ve already mentioned, Android operates on the principle of permissions, in order to protect your data from exploitation. This means that applications can access hardware and data only if and when they are given permission. The system maintains a list of permissions for each application installed on the device. Moreover, “the system resets the permissions of unused apps that target Android 11 or higher, and apps might need to update the permissions that they declare if they use the system alert window or read information related to phone numbers.”
Developers.Android.com mentions that there are various types of permissions:
a. One-time permissions
The dialogue box for this kind of permissions contains the option called Only this time. If this option is selected, the app that requests a location, microphone or camera-related permission is “granted a temporary one-time permission”.
b. Unused apps auto-reset permissions
If an application hasn’t been used for months, user data are protected by the system, which automatically resets the runtime initial permissions. When it comes to permission dialogue visibility, Developers.Android.com explains: “Starting in Android 11, if the user taps Deny for a specific permission more than once during your app’s lifetime of installation on a device, the user doesn’t see the system permissions dialog if your app requests that permission again. The user’s action implies “don’t ask again.” On previous versions, users would see the system permissions dialogue each time your app requested a permission, unless the user had previously selected a “don’t ask again” checkbox or option. This behaviour change in Android 11 discourages repeated requests for permissions that users have chosen to deny.”
Permissions can also be classified according to how dangerous they are from a cybersecurity point of view:
a. Normal permissions
Normal permissions include: ACCESS_NOTIFICATION_POLICY, ACCESS_WIFI_STATE, BLUETOOTH, BLUETOOTH_ADMIN, INTERNET, KILL_BACKGROUND_PROCESSES, MANAGE_OWN_CALLS, MODIFY_AUDIO_SETTINGS, SET_ALARM, SET_WALLPAPER, VIBRATE etc.
b. Signature permissions
Signature permissions involve: BIND_AUTOFILL_SERVICE, BIND_INPUT_METHOD, BIND_VPN_SERVICE, CLEAR_APP_CACHE, MANAGE_DOCUMENT, READ_VOICEMAIL, REQUEST_INSTALL_PACKAGES etc.
c. Dangerous permissions
Dangerous permissions refer to: READ_CALENDAR, WRITE_CALENDAR, CAMERA, READ_CONTACTS, WRITE_CONTACTS, RECORD_AUDIO, READ_PHONE_NUMBERS, CALL_PHONE, ANSWER_PHONE_CALLS, SEND_SMS, RECEIVE_SMS, READ_SMS and so on. You can find out more details about certain Android permissions at TechK47.com. If you want to know how to access app permissions on Android or how to change app permissions, you should simply check the App permissions Settings section on your mobile phone or tablet. You should bear in mind, though, that turning off permissions may cause apps on your device to stop functioning.
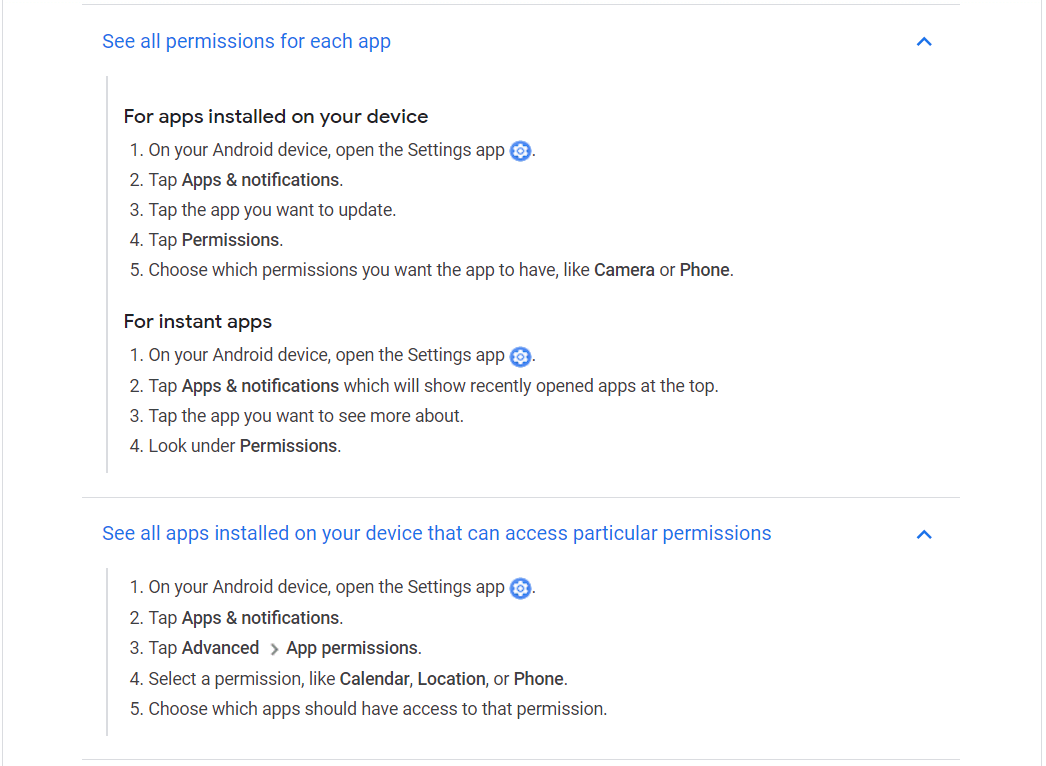
Source: Google Play Help
Android Permissions Threats
As one can expect, Android permissions are dangerous because, even though their purpose was to protect users, they can compromise the device, its resources and the data stored on it if they are granted to a malicious application.
Here are a few examples of how the most frequently requested Android permissions can be abused:
1. SYSTEM_ALERT_WINDOW
When granted, this permission allows an app to display a window over any other app, with no notification for the user. SearchSecurity explains: “this functionality can be abused to display fraudulent ads and overlay windows — a common technique used by banking Trojans that create windows identical to a banking app’s login page, as well as ransomware that places a persistent on-top screen. “
2. ACCESS_NETWORK_STATE
This Android permission allows apps to check for cellular network connections (including Wi-Fi), to download updates or connect to a server or website. It is usually required by location, check-in and social media apps. By spotting available network connections, malicious apps can download malware or send text messages. Malicious connections can drain your battery and add to data charges.
3. ACCESS_WIFI_STATE
This permission gives apps access to Wi-Fi network information, including the list of configured networks and the currently active network. This Android permission is required by browser and communication apps. It can easily be abused if cybercriminals use device bugs to steal Wi-Fi passwords and hack into the networks you usually access.
4. Full INTERNET access
This permission allows applications to connect to the Internet – it is required by browser, communication, productivity and gaming apps and can be abused if malicious apps use it to download malware or communicate with their command centres.
5. Modify / Delete SD cards
When granted this permission, apps can write on external storage, including SD cards. Most often, this Android permission is required by camera, document and audio and video apps. Hackers can abuse this permission by storing copies of stolen information or saving files before sending them to the command centre. It’s not uncommon for malicious apps to even delete photos or other files on the SD card.
6. SEND_SMS
This permission is required by communication and social media apps, to whom it allows to send text messages. Cybercriminals might use it to communicate with command centres or to send messages to premium numbers, which will leave you with unexpected charges. Trond Boksasp and Eivind Utnes from the Norwegian University of Science and Technology also point out that there is a danger in the combination of permissions: “While two permissions can be harmless when granted separately, the privacy and security risk can increase drastically if they are granted together. As an example, take the INTERNET and READ SMS permissions; separately they are harmless, but combined with each other you get an application that can read your text messages and send the contents to a third party. There are many permission combinations that carry severe risks but are not presented as such to the user.”
The Privacy Issue with Android Permissions
Apart from the possible cybersecurity and financial consequences an Android permissions abuse may have, there is always the issue of privacy. Privacy is your right to be left alone and it should be protected. It is more than…moodiness – data privacy has actually “been recognized by governments worldwide and resulted in numerous data protection laws. GDPR represents the most groundbreaking and wholesome data protection regulation and imposes huge fines in order to protect the privacy of an individual.”
Prevention Advice for Your Devices
Android is the most common OS for mobile devices, so you can be sure that at some point, in some way or another, cybercriminals will try to take advantage of this. Although Android permissions can be risky, you can always prevent troubles by paying attention to certain aspects:
1. Use apps with caution. Applications are the easiest way into your device for malware. If you need to download an application, make sure you use only Google Play for this because they scan all the available applications. Third-party applications may be tempting, but you never know if you’ll open a Pandora’s box by installing them or not.
2. Check app permissions on Google Play before downloading and installing anything. Always check the application description and the Permission details section to see what the app will require. These descriptions don’t usually tell why a permission is needed, but they will help you know what to expect.
3. Send an email to the developer. If you need more details about an app’s permissions, feel free to contact the developer. If the reply isn’t satisfying or if you don’t get any at all, you should most probably avoid their application.
4. Capitalize on the huge Android community. Play Store reviews, check-forums and Android news sites can help you find out more about the security of the applications you need. This will probably take a little time, but it’s always better to be safe than sorry.
Prevention Advice for Work Devices
It should come as no surprise that the security of your mobile device might influence the security of the company’s network in which you integrate your device. This is especially true if you use your Android devices extensively for work purposes, as it happens in the case of BYOD (Bring Your Own Device) Policy.
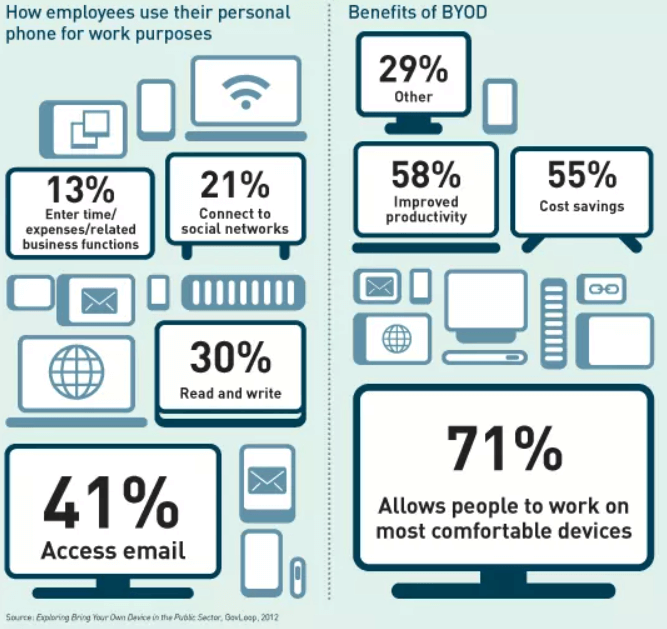
Source: Networking Space
As Lotus Lee and Jeremiah Still note in their paper Re-designing Permission Requirements to Encourage BYOD Policy Adherence, “access to proprietary company data and information from an employee’s smartphone raises serious privacy and security concerns. Companies are vulnerable to data breaches if employees are unable to discern which applications are safe to install.” Here’s what an employer can do to stay safe:
Encrypt data at rest and in transit
Encryption should protect the contents of sensitive files even if a device is stolen or the traffic gets intercepted over an unsecured network. As the InfoSec Institute notes, “to prevent unauthorized access and maintain the encryption in case of a security breach, the IT department of the concerned organization should take control of encryption keys.”
Application installation control
Companies can use Android Enterprise and its managed Google Play Portal, which offers a containerized environment that helps to separate work and personal applications and data. This allows companies to have better control over devices used for work purposes and their Android permissions without confining an employee’s personal use of their device.
Containerization
Similar to how the Google Play Portal functions, containerization allows a part of the device (including applications and their permissions) to be separated into its own bubble, password-protected and regulated by a different set of policies from the device’s other applications and content. This allows employees to enjoy uninhibited use of their devices in their free time without posing any security risks to the company’s network.
How can Heimdal™ Security help?
In the context of BYOD and Android permissions, Heimdal™ Security can help you protect your company’s network perimeter by using machine learning-driven intelligence that can spot hidden threats that firewalls are unable to detect. Our IPS (Intrusion Prevention System) solution, Heimdal™ Threat Prevention Network, works at the DNS layer to prevent advanced and yet unknown threats which might be trying to infiltrate your organization. With Heimdal™ Threat Prevention Network, you can detect advanced malware in your network, block malicious web content, and prevent data leakage. Heimdal® Network DNS Security
Wrapping Up
In the hastiness of our modern world, we know that you might not have paid considerable attention to the Android permissions required at the installation of the apps on your devices. You may not have even thought of them as threats. Unfortunately, the truth is they can cause you and the company you work for many issues, so it’s best to download, install and use applications thoughtfully.
Whatever prevention method you choose, please remember that Heimdal™ Security always has your back and that our team is here to help you protect your home and your company and to create a cybersecurity culture to the benefit of anyone who wants to learn more about it.
Drop a line below if you have any comments, questions or suggestions – we are all ears and can’t wait to hear your opinion!










 Network Security
Network Security
 Vulnerability Management
Vulnerability Management
 Privileged Access Management
Privileged Access Management  Endpoint Security
Endpoint Security
 Threat Hunting
Threat Hunting
 Unified Endpoint Management
Unified Endpoint Management
 Email & Collaboration Security
Email & Collaboration Security









