Contents:
Following attacks on users of Android and iOS in the US, Taiwan, South Korea, Germany, Japan, and the UK, the Roaming Mantis campaign turned its attention to French users, possibly impacting tens of thousands of devices.
Security experts think that Roaming Mantis is a financially-motivated Chinese cybercrime group that began attacking individuals living in Europe this year in February.
The Lures and the XLoader
In a cyberattack that has been recently discovered, the malicious campaign uses SMS communication to trick victims into downloading malware on their Android devices. If the target is using iOS, they will be redirected to a phishing website requesting Apple login information.
A report by researchers at European cybersecurity SAAS company SEKOIA published yesterday showed that the Roaming Mantis threat actor is now dropping the XLoader (MoqHao) payload on Android devices.
According to the report, MoqHao (also known as Wroba, XLoader for Android) is a powerful Android Remote Access Trojan (RAT) with information-stealing and backdoor functionalities that most likely spreads through SMS spamming.
The ongoing Roaming Mantis operation focuses on French mobile users and begins with an SMS that asks potential victims to follow a URL.
The text message notifies the victims of the arrival of a package, which they must check and receive. You can see the original message in French below:
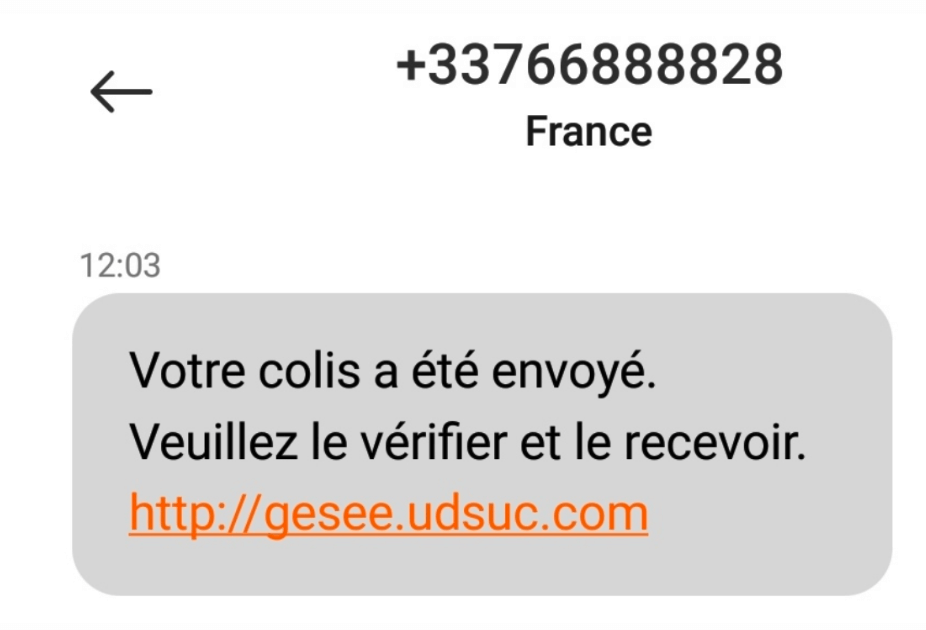
If the target lives in France and is using an iOS device, they will be instructed to visit a phishing page that collects Apple credentials. If the victim’s mobile phone is running the Android operating system, they will be directed to a website that contains the installation file for a mobile app (an Android Package Kit – APK).
The Roaming Mantis servers display a 404 error for users whose devices are not in France, and the attack ends.
Below is an overview of the infection chain based on the victim’s location and operating system.
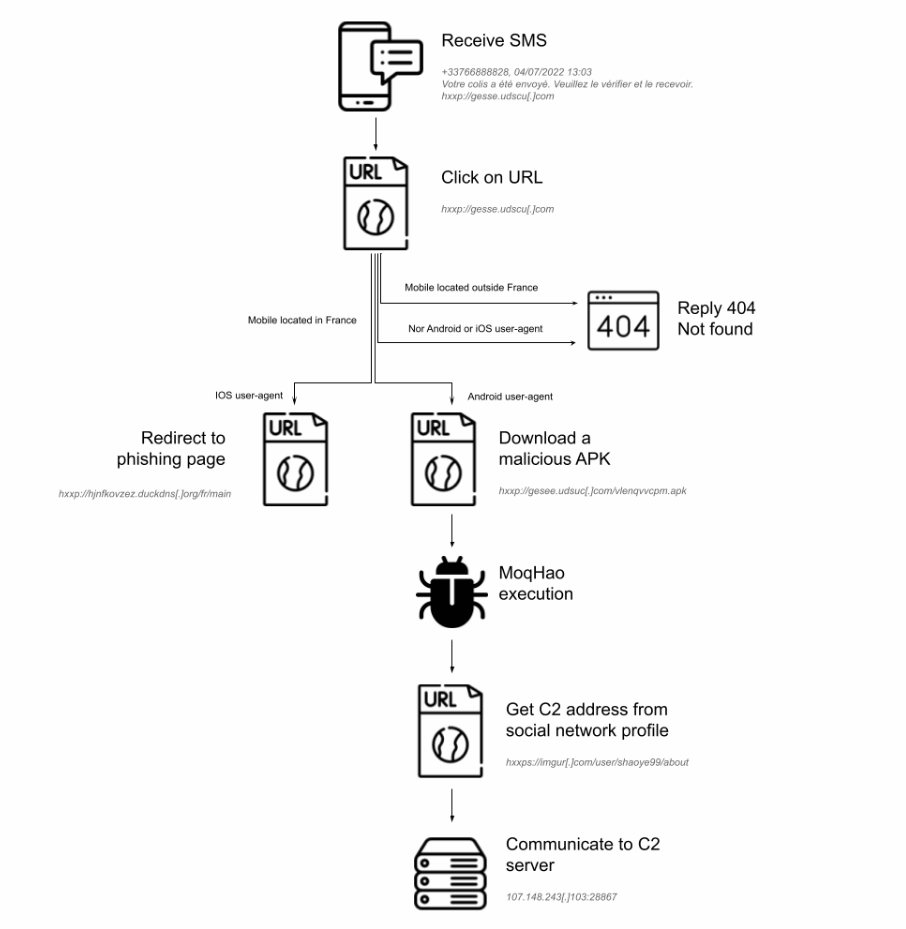
The APK runs and imitates a Chrome setup while soliciting risky authorizations, including:
- SMS interception,
- phone call making,
- reading and writing storage,
- processing system alerts,
- obtaining accounts lists.
As explained by BleepingComputer, the command and control (C2) configuration is recovered from hardcoded Imgur profile locations which are encoded in base64 to avoid being detected.
The victim’s number might be substantial, as SEKOIA reported that more than 90.000 unique IP addresses requested the C2 server distributing MoqHao up to this point.
It’s unknown how many iOS users have provided their Apple iCloud login information on the Roaming Mantis phishing page, but it may be the same number or even higher.
Roaming Mantis Infrastructure
Security researchers at SEKOIA claim that the infrastructure of Roaming Mantis hasn’t changed much since team Cymru’s last analysis in April.
The open ports on the servers are still the same: TCP/443, TCP/5985, TCP/10081, and TCP/47001, while the same certificates discovered in April are still in use.
Domains used inside SMS messages are either registered with Godaddy or use dynamic DNS services such as duckdns.org. The intrusion set uses more than hundreds subdomains. Indeed each IP address is resolved by dozens of FQDN.
IoCs are available on the SEKOIA.IO Community Github.
If you liked this article, follow us on LinkedIn, Twitter, Facebook, Youtube, and Instagram for more cybersecurity news and topics.


 Network Security
Network Security
 Vulnerability Management
Vulnerability Management
 Privileged Access Management
Privileged Access Management
 Endpoint Security
Endpoint Security
 Threat Hunting
Threat Hunting
 Unified Endpoint Management
Unified Endpoint Management
 Email & Collaboration Security
Email & Collaboration Security










