Contents:
South Korean researchers presented a new covert channel attack named CASPER. It uses internal speakers to leak data from air-gapped PCs to nearby smartphones at a rate of 20 bits per second.
Until now, similar attacks used external speakers. But network-isolated systems, commonly used in highly secretive organizations, do not usually have external speakers. The new method uses internal speakers since those are commonly present in any environment.
How Does the Attack Work?
To breach an air-gapped system, hackers need physical access to the target, first of all. In order to carry on the attack, they must first infect it with malware. They either need a rogue employee or an intruder. The possibility that this happens is not that far-fetched.
Did this kind of attack happen before? The answer is yes, and not just once.
- Iran’s uranium enrichment facility at Natanz was infected with the Stuxnet worm.
- the Agent.BTZ malware infected a U.S. military base.
- the Remsec modular backdoor succeeded to gather information from air-gapped government networks. It was reported as active for more than 5 years.
Once the threat actor successfully installs the malware, it can list the filesystem of the target, find files or file types that match a hardcoded list and make an exfiltration attempt. Also, it can perform keylogging, a more effective method in this case, where the data transmission rate is slow.
The malware will encode the data to be exfiltrated from the target in binary or Morse code and transmit it through the internal speaker using frequency modulation, achieving an imperceptible ultrasound in a range between 17 kHz and 20 kHz.
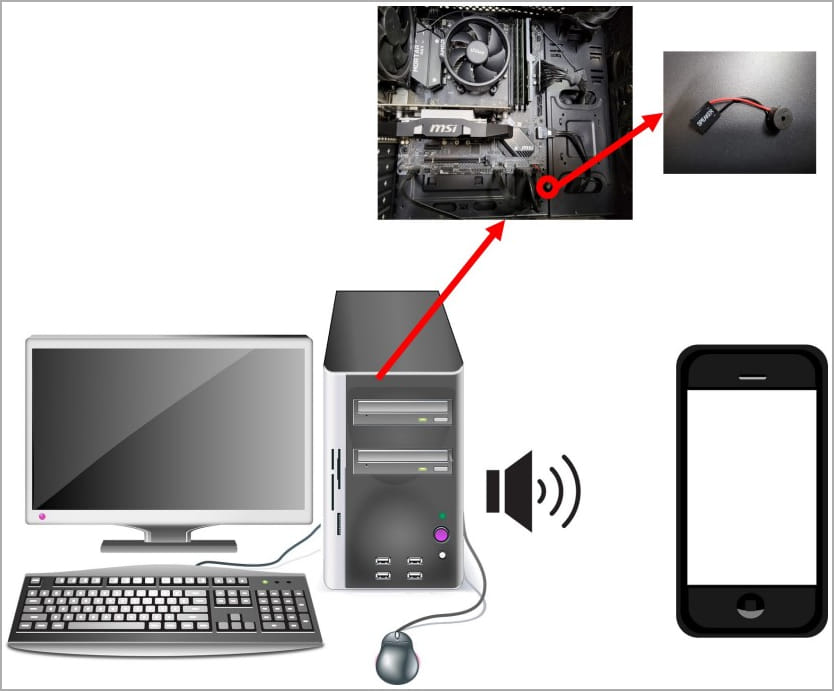
What Can This Method Do?
In their cyberespionage activities, hackers need to exfiltrate data from air-gapped systems.
If they would use the Casper method, the malware could transmit an 8-characters long password in roughly 3 seconds. While a 2048-bit RSA key could be transmitted in 100 seconds.
In order to exfiltrate larger packets, for example, a 10 KB file, hackers would need at least one hour. So, as the Korean researchers stated themselves, the lack of speed is the downside of this method:
Our method is slower in transferring data compared to other covert channel technologies using optical methods or electromagnetic methods because the speed of data transfer by sound is limited. Therefore, it is possible to think of a method of transmitting data simultaneously by varying the frequency band for a fast bit rate. However, this method is impossible. The method using an internal speaker is impossible to produce sound in one frequency band while making sound in another frequency band.
How to Defend Against a Casper Attack
Researchers also offered some ways to prevent a Casper attack. Here are their recommendations:
- Remove the internal speaker from mission-critical devices.
- Use a high-pass filter to retain all emitted frequencies that are within the range of audible sound. Just block ultrasound transmissions.
And if you liked this article, follow us on LinkedIn, Twitter, Facebook, and YouTube for more cybersecurity news and topics.










 Network Security
Network Security
 Vulnerability Management
Vulnerability Management
 Privileged Access Management
Privileged Access Management  Endpoint Security
Endpoint Security
 Threat Hunting
Threat Hunting
 Unified Endpoint Management
Unified Endpoint Management
 Email & Collaboration Security
Email & Collaboration Security







