Contents:
In a recent investigation, security researchers have discovered 75 applications on Google Play and other ten on Apple’s App Store that are engaged in ad fraud. The apps would do more than flood the users with advertisements, they also generated revenue through impersonating other legitimate apps. It is reported that collectively, these apps were downloaded by 13 million users.
According to BleepingComputer, these apps are part of a new ad fraud campaign called “Scylla”. Analysts believe that Scylla is the third wave of an operation launched by the same threat actor, after 2019’s “Poseidon” and 2020’s “Charybdis”.
How Scylla Works?
To make it appear to the advertisers as if the ad impressions are coming from a profitable software category, Scylla apps were found to use a bundle ID that didn’t match the name of their publication. Researchers discovered that 29 Scylla apps imitated up to 6.000 CTV-based apps and cycled regularly through the IDs to evade fraud detection.
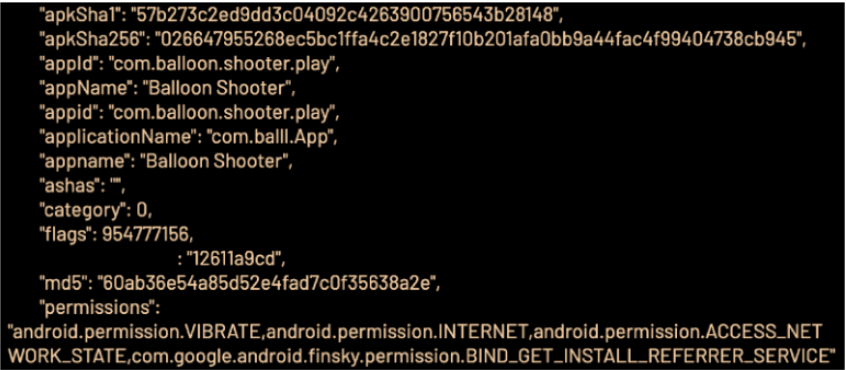
C2 responding to the ID spoofing instructions (Source)
To fool the victim into thinking that nothing suspicious is happening, the Google Play apps were loaded in hidden WebView windows, with the entirety of the process happening in the background. More than that, the apps would trigger ad impression events even when the victims were not using their devices, through a “JobScheduler” system. Scylla apps were using the Allatori Java obfuscator, so they were harder to identify and reverse engineer than their predecessor “Poseidon”.
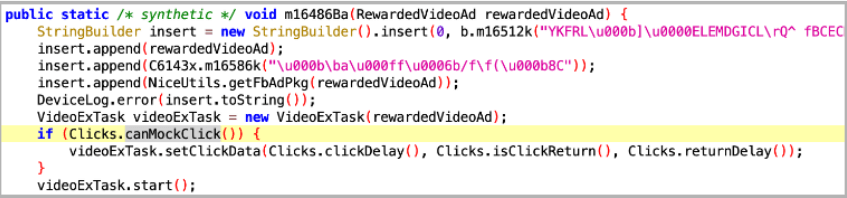
JobScheduler Code (Source)
Response to the Malware
The researchers informed Google and Apple about the malware and since then the apps have been removed from both Store platforms. The apps should be detected automatically on Android devices unless the Play Protect security option is disabled. For iOS, it is not clear how to remove adware apps already installed on the device. Some of the apps engaged in the Scylla ad fraud are:
On iOS:
- Loot the Castle – com.loot.rcastle.fight.battle (id1602634568)
- Run Bridge – com.run.bridge.race (id1584737005)
- Shinning Gun – com.shinning.gun.ios (id1588037078)
- Racing Legend 3D – com.racing.legend.like (id1589579456)
- Rope Runner – com.rope.runner.family (id1614987707)
- Wood Sculptor – com.wood.sculptor.cutter (id1603211466)
- Fire-Wall – com.fire.wall.poptit (id1540542924)
- Ninja Critical Hit – wger.ninjacriticalhit.ios (id1514055403)
- Tony Runs – com.TonyRuns.game
On Android:
- Super Hero-Save the world! – com.asuper.man.playmilk
- Spot 10 Differences – com.different.ten.spotgames
- Find 5 Differences – com.find.five.subtle.differences.spot.new
- Dinosaur Legend – com.huluwagames.dinosaur.legend.play
- One Line Drawing – com.one.line.drawing.stroke.yuxi
- Shoot Master – com.shooter.master.bullet.puzzle.huahong
- Talent Trap – NEW – com.talent.trap.stop.all
Users could keep an eye out for suspicious or unwanted programs by keeping an eye out for symptoms like quick battery depletion, high internet data usage, or apps they don’t recall installing. Researchers also recommend to the check the list of installed apps and removing any apps they do not remember installing or that are coming from an unfamiliar vendor.
If you liked this article, follow us on LinkedIn, Twitter, Facebook, Youtube, and Instagram for more cybersecurity news and topics.










 Network Security
Network Security
 Vulnerability Management
Vulnerability Management
 Privileged Access Management
Privileged Access Management  Endpoint Security
Endpoint Security
 Threat Hunting
Threat Hunting
 Unified Endpoint Management
Unified Endpoint Management
 Email & Collaboration Security
Email & Collaboration Security








