Contents:
American video game publishing house 2K Games confirms that they have been the victims of a cyberattack. The hackers targeted 2K’s help desk platform and used it to reach customers with fake support tickets, pushing malware through embedded links. 2K’s support account took to Twitter to address the ongoing situation after BleepingComputer broke the story on the security breach.
Earlier today, we became aware that an unauthorized third party illegally accessed the credentials of one of our vendors to the help desk platform that 2K uses to provide support to our customers.
“Please do not open any emails or click any links”
2K advised its customers to not interact with emails received from the 2K Games support account. Per BleepingComputer, 2K customers started receiving emails earlier today saying they opened support tickets on the publisher’s online support ticketing system.
The unauthorized party sent a communication to certain players containing a malicious link. Please do not open any emails or click on any links that you receive from the 2K Games support account.
For those users who have interacted with the email, the company advised them to take the following steps to mitigate the potential impact of the malware immediately:
- Reset any user account passwords stored in your web browser (e.g., Chrome AutoFill)
- Enable multi-factor authentication (MFA) whenever available, especially on personal email, banking, and phone or Internet provider accounts. If possible, avoid using MFA that relies on text message verification – using an authenticator app would be the most secure method
- Install and run a reputable anti-virus program
- Check your account settings to see if any forwarding rules have been added or changed on your personal email accounts
The company will issue an official notice when it is safe for the players to interact with the support staff’s emails again.
RedLine Info-Stealer Was Used by the Attackers
Users confirmed that the tickets were accessible via 2K’s help desk portal, however, numerous recipients stated that they were not the ones who opened the support tickets. After the tickets were opened, they would receive another email in reply from a supposed 2K official, named “Prince K”. The email included links to a downloadable file named “2K Launcher.zip” from 2ksupport.zendesk.com.
The archive contained an executable file which was in fact the RedLine information-stealing malware, as BleepingComputer found out. After infecting the system, the malware threats to steal a wide range of data such as web browser history, cookies, saved passwords, messages, but also stored financial information such as credit card data, or cryptocurrency wallets.
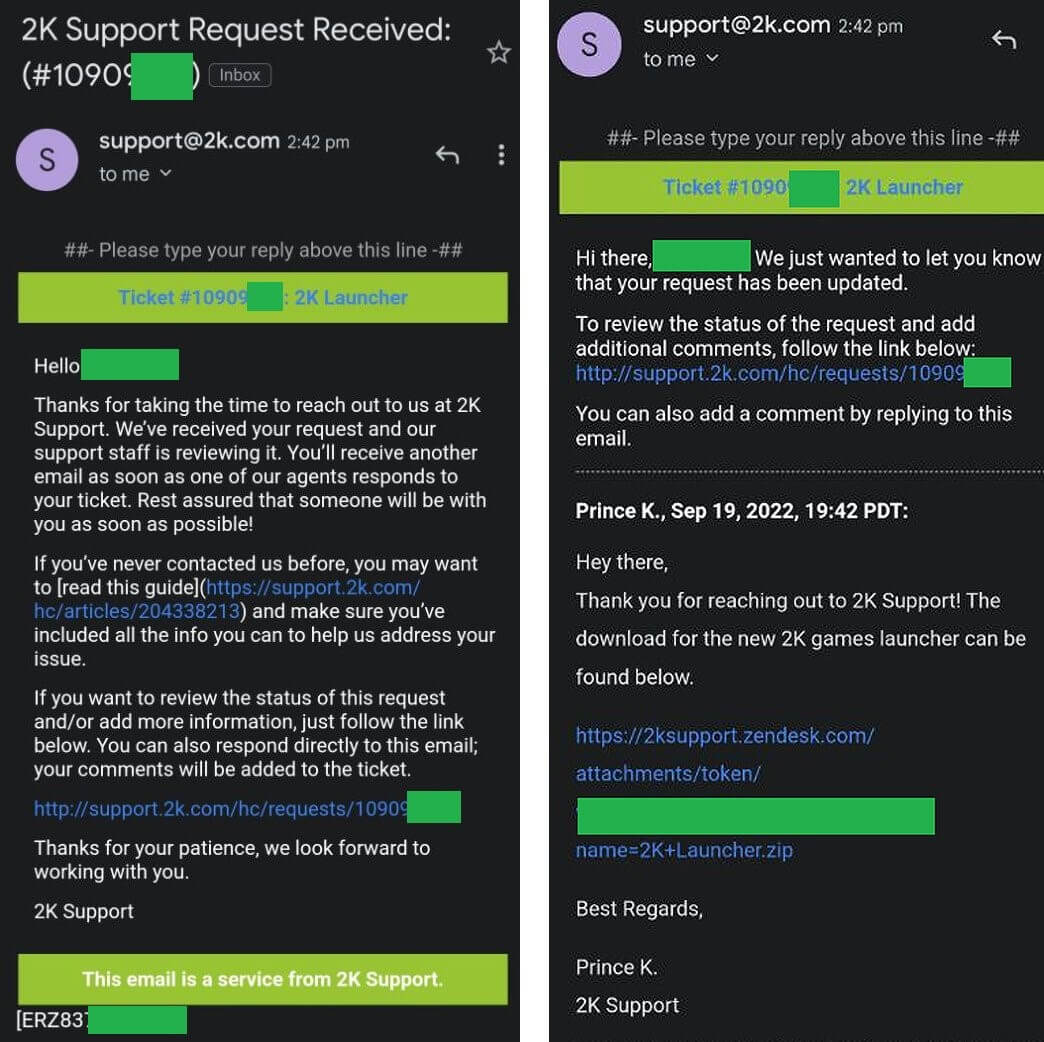
2K support tickets received by the victims (Source)
Although it is too early to draw suspicions, as the company is yet to provide any information regarding the claims, users are linking the attack with the Rockstar Game breach that leaked footage of their upcoming game, GTA VI. What drew users to this conclusion is the fact that both 2K and Rockstar Games are subsidiaries of Take-Two Interactive. It is believed that the Rockstar Games attack was conducted by a hacker affiliated with the South American hacking group Lapsus$.
If you liked this article, follow us on LinkedIn, Twitter, Facebook, Youtube, and Instagram for more cybersecurity news and topics.


 Network Security
Network Security
 Vulnerability Management
Vulnerability Management
 Privileged Access Management
Privileged Access Management
 Endpoint Security
Endpoint Security
 Threat Hunting
Threat Hunting
 Unified Endpoint Management
Unified Endpoint Management
 Email & Collaboration Security
Email & Collaboration Security










