Contents:
Phishing is a harmful tactic employed by cyber attackers in order to obtain sensitive information (such as credit card numbers, usernames, and passwords). The attackers pose as reputable in order to trick the victims into putting their faith in them and disclosing their personal information. The information collected via phishing may be utilized for a variety of purposes, including money fraud, identity theft, illegal access to the victim’s accounts or accounts to which they have access, blackmailing the victim, and more.
How Does This New Method Work?
A sophisticated new phishing approach enables adversaries to circumvent multi-factor authentication (MFA) by discreetly requiring victims to log into their accounts directly on attacker-controlled servers via the VNC screen sharing system, according to the researchers.
It is still necessary to get the one-time passcode issued to the victim in order to completely compromise the account, even if threat actors are successful in convincing users to submit their credentials on a phishing site if MFA is in place.
Attackers have upgraded their phishing kits to include tactics such as reverse proxies or other means of collecting MFA codes from unknowing victims in order to obtain access to a target’s MFA-protected accounts.
Companies, on the other hand, are becoming more aware of this technique and have started implementing security measures that prevent logins or cancel accounts when reverse proxies are found.
While doing a penetration test for a client, security researcher mr.d0x tried to launch a phishing assault on the company’s workers in order to get corporate account credentials. He was unsuccessful.
The accounts were all equipped with MFA, therefore mr.d0x used the Evilginx2 attack framework to launch a phishing campaign, which served as a reverse proxy to harvest passwords and MFA codes from the compromised accounts.
When the researcher conducted the test, he discovered that Google blocked logins when it detected reverse proxy or man-in-the-middle (MiTM) attacks.
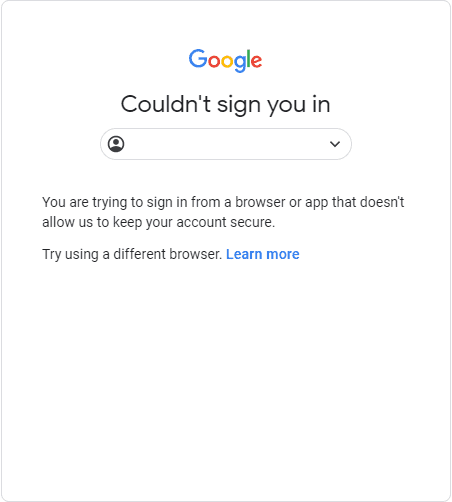
In an interview with BleepingComputer, mr.d0x said that this was a new security feature introduced by Google in 2019 expressly to avoid these sorts of assaults.
VNC is a remote access software program that enables remote users to connect to and control the desktop of a logged-in user from anywhere in the world. Virtual Network Computing (VNC) clients are used by the majority of users to connect to a VNC server and access the remote desktop in a way similar to Windows Remote Desktop.
The researcher’s novel phishing approach comes into play when a tool called noVNC enables users to connect to a VNC server directly from inside a browser by merely clicking a link, which is enabled by the noVNC program.
noVNC is both a VNC client JavaScript library as well as an application built on top of that library. noVNC runs well in any modern browser including mobile browsers (iOS and Android). Essentially, noVNC allows the web browser to act as a VNC client to remotely access a machine.
So how do we use noVNC to steal credentials & bypass 2FA? Setup a server with noVNC, run Firefox (or any other browser) in kiosk mode and head to the website you’d like the user to authenticate to (e.g. accounts.google.com). Send the link to the target user and when the user clicks the URL they’ll be accessing the VNC session without realizing it. And because you’ve already setup Firefox in kiosk mode all the user will see is a web page, as expected.
When a victim clicks on a link, the attacker’s VNC server will display a login screen for the targeted email service, which the victim may enter into as usual. This is because the attacker’s VNC server is set to run a browser in kiosk mode, which runs the browser in full-screen mode.
Since it’s my server I can have many tricks up my sleeve, for example say I have burp suite or any other HTTP proxy attached to this browser and its capturing all the HTTP requests occurring. When the user is done I can check the requests and grab the username and password and session token,” mr.d0x told BleepingComputer in a conversation about the attack.
Another alternative could be I inject JS into the browser before sending the phishing link. When the user begins using the browser it runs my JS.Theres many more options because at the end of the day the user authenticates onto your server.
The best advice for avoiding these sorts of assaults is the same as it has always been: do not click on URLs from unknown senders, look for odd domains in embedded links, and take any email that asks you to enter into your account as a suspect.
Browsers are more powerful than ever and the usage of browsers as clients for remote access provides new ways for attackers to steal credentials, bypass 2FA and more. I strongly believe that what I’ve demonstrated in this article is only a small portion of what this technique can be used for. As usual, feel free to build off this technique or provide comments and feedback on Twitter.
How Can Heimdal Help?
Heimdal Security has developed two email security software aimed against both simple and sophisticated email threats (Heimdal Email Security, which detects and blocks malware, spam emails, malicious URLs, and phishing attacks and Heimdal Email Fraud Prevention, a revolutionary email protection system against employee impersonation, fraud attempts – and BEC, in general.
You may want to consider Heimdal Security’s Heimdal Email Fraud Prevention, the ultimate email protection against financial email fraud, C-level executive impersonation, phishing, insider threat attacks, and complex email malware. How does it work? By using over 125 vectors of analysis and being fully supported by threat intelligence, it detects phraseology changes, performs IBAN/Account number scanning, identifies modified attachments, malicious links, and Man-in-the-Email attacks. Furthermore, it integrates with O365 and any mail filtering solutions and includes live monitoring and alerting 24/7 by our specialists.


 Network Security
Network Security
 Vulnerability Management
Vulnerability Management
 Privileged Access Management
Privileged Access Management
 Endpoint Security
Endpoint Security
 Threat Hunting
Threat Hunting
 Unified Endpoint Management
Unified Endpoint Management
 Email & Collaboration Security
Email & Collaboration Security










