Contents:
How many tabs do you have open in your browser right now?
Go ahead and count. We have time.
You might be wondering what the purpose of this seemingly useless exercise is, so I’ll get right to it. While looking to enhance your productivity or just for some fun, you will most likely overlook a key issue: your online safety.
Cyber security is usually the thing you never think about, unless your computer becomes infected. And it’s not just you, of course. Most Internet users share the same indifference towards information security, in spite of it being on the news weekly, if not daily.
Don’t you think it’s strange that we take so many precautions to keep our home and physical belongings safe, but invest so little resources into securing our digital lives, even though they have a huge impact on our revenue, reputation and relationships?
The fact of the matter is that we, as Internet users, are simply not doing enough to keep safe online. And there’s no scarcity when it comes to cyber threats and cyber attacks that come in all shapes, sizes and outcomes.
Just as the software you use is making your computer vulnerable to cyber attacks, so are your online habits. Let me line up just a few examples.
Do you have any of these compromising online habits?

1. Adopting a new app without checking its safety features
How many times have you downloaded an app without even thinking twice about how secure it is or how it handles all the data you put in it?
Maybe you read about it somewhere, maybe it’s a cool new startup that everyone’s talking about or maybe you were looking for an app that can help you organize your task list better. Irrespective of your purpose or intent, we’ve all done this.
The problem with this habit it that it’s not as insignificant as you may think it is. A good app is not only supposed to be easy to use, but it should also protect your information and your privacy. But the trust is that very few actually do, no matter if the companies are big or small (and don’t even get us started on the matter of privacy).
Friendly tip: Before installing an app on your phone or your laptop and giving it rights to access your private information, at least go to the software maker’s website and check the details. See if they seem legitimate, if they offer enough information and if their website at least uses https (a protocol that encrypts communication to keep it safe from prying cyber criminals’ eyes). Don’t just blindly let it into your digital life. It could be rogue, for all you know, or it could become a huge security risk if attackers would compromise it.

2. Lacking the cyber security knowledge and skills to know what to look for
Should you have the very honest intention of following up on the advice above, you may be confronted with a key issue: not knowing what to look for in terms of cyber security.
While it’s true that most aspects related to information security require technical knowledge, it’s also true that understanding the basics is something that everyone can do. Taking a Cyber Security for Beginners course can be a first step, but also reading a few articles on the subject can help.
You don’t need to become an expert to keep your computer and data safe. You just need to pay more attention and listen to the specialists’ advice. It’s often as simple as using strong passwords, the right security products and keeping a generally cautious attitude.
3. Never locking your computer while stepping away from it
You probably hate remembering passwords as much as the next person (and me as well), but they’re necessary. So I hope you’ll incorporate this healthy habit into your routine: set a password for your PC account (ideally a guest account, not the administrator account) and close the lid or put in on stand-by every time you walk away from your computer.
I know you’ve hear this about a million times, but cyber security advice only sounds redundant because too few people actually apply it.
Doing this small thing can keep you safe from malicious attackers who may even have a friendly face, such as a colleague’s. Don’t rule out any possibility. Keeping safe online requires a certain dose of (healthy) paranoia.
4. Systematically ignoring updates
How many times have you rolled your eyes when being prompted to update your Adobe Flash Player, Java or any other application you have installed?
Mhm. But here’s a not-so-fun fact: 8 applications are responsible for making 99% of Windows-running PCs vulnerable to cyber attacks. And you are currently using at least 3 of them.
Keeping your software up to date can protect you from 65% of cyber attack vectors, closing security holes before cyber criminals can exploit them.
[Tweet “Do you systematically ignore software updates? Here’s why to stop doing it:”]Now, you’re most certainly going to think that you just don’t have time to do that, as there are more important items on your to-do list, but here’s a top tip: there are products that can update your software for you, automatically and silently, without ever interrupting your work or your flow. And that’s all for free!
One more problem solved.

5. Multitasking
Cyber criminals loooove multitaskers!
Why?
It’s rather simple: because they’re in a hurry to get more done and because they don’t pay adequate attention to every detail. Cyber criminals can use very creative ways to infect your system, from rogue websites, to infected banners and public Wi-fi networks set up to collect information about everything you do online while using that network.
If you’re all about getting things done, no matter how, maybe you should reconsider. Being cautious and learning to spot potential threats will become a key skill in the coming years.
Of course, “human detection” is not enough. You still need the right tools to catch threats and filter them out before they reach your system, which is something you can’t do manually, so don’t shy away from trying different security products to see which fit your needs better.
6. Using weak passwords and reusing them
This particular piece of advice should be plastered on every website and application ever!
Every data breach in the past 2 years has revealed, systematically, what weak passwords the compromised users had chosen. Passwords such as “123456” or “password” are at the top of the list every single time. You may have used these passwords yourself or maybe you’re still using them, which I hope you’ll change.
A poor choice of passwords is a big security threat to your data. Cyber criminals have the tool to hack NASA, so how long do you think it would take them to crack your security when your password is “password123”?
[Tweet “Stop reusing passwords! Here’s how to protect your accounts from being hacked:”]But there’s something that makes this situation even more dangerous: reusing passwords. So not only are you setting weak passwords, but you’re using them for multiple accounts as well.
Let’s see how this would play out in a cyber attack scenario:
- The cyber criminal employs an automatic system to detect vulnerabilities in your system
- Once the infection happens, it will try to crack your passwords
- It will probably take less than a few seconds to find out you’re using “12345678” as your passwords
- The attacker will then try to see if you’re using this password for other accounts
- When he finds out you do, all your accounts sharing this weak security measure will be exposed, with the attacker being able to gather all the data you have stored inside in a matter of minutes.
And all this could happen while you’re sipping on your latte.
If you don’t believe your data is valuable enough to make you a target, think again. Cyber criminals have a lot of objectives, from stealing your money to using you to get to your company or someone else. There’s always a way they can rob you, extort you or use your resources to launch additional attacks. You can be the main target or just the means to an end.
Of course, you can do something before that happens: learn to manage your credentials like a PRO. (It’s not even that complicated, really.)

7. Not backing up your data
Should something happen to your laptop, what are you going to do about the data you lost?
It doesn’t even have to be a cyber attack. You could spill water all over it, drop it, forget it or even have it stolen from you.
Do you have a backup of your recent work? Are you sure that backup works?
Backing up your data is one of those things you wish you would’ve done when you had the chance. Ransomware victims can attest to this the most, since their data was encrypted with no chance to get it back. Ever.
So the wise thing to do is use this step by step guide to set up an automatic backup schedule that can help you keep your work and other important information safe. Trust me, you’ll be happy to have done this one day.

8. Choosing to satisfy your curiosity over being cautious
“Curiosity killed the cat,” the famous saying says. If we’d update this to 2015’s cyber security situation it might sound like: “curiosity got the cat’s PC infected with malware (and the consequences are irreversible).”
The web is full of attention-grabbing, clickbait-packed headlines which beg for our clicks. Sometimes, the content is legitimate, safe. But sometimes it can lead you to a malicious destination, such as a phishing website or a malware-infected spam email. And cyber criminals are getting unbelievably good at impersonating legitimate publications or channels.
“Check before you click” is the best policy when it comes to using the web safely. Not falling for scams is another ability that you’ll acquire if you learn a bit about information security and opting to be safe instead of feeding your curiosity is another.
Don’t forget: attackers know how to take advantage of your spontaneous reactions and rely on them to get you to click. Sometimes, they can even infect you without clicking, just by browsing a website, so keep an eye out for trouble.

9. Assuming your antivirus provides 100% protection
We’re sorry to say this, but it’s not the ‘90s anymore. Viruses are no longer your biggest problem, malware is – this exotic terms that cyber security specialists are parading around town.
So, long story short, antivirus isn’t enough. It can’t be enough, since attackers are constantly racing the cyber security industry to find new and sly ways to infect PCs without being detected. The longer they stay inside a system without being noticed by antivirus, the more information they can extract.
[Tweet “Do you still believe antivirus can protect you 100%? Think again:”]With that in mind, please be aware that no security solution can protect you 100%. That’s exactly why the best advice is to use a multi-layered security system that can protect you from various angles. The more layers, the better. But don’t expect antivirus to do the impossible. It’s just not a possibility anymore.
10. Not reading the terms of use
Ah, the inglorious terms of use, the End User License Agreement (EULA) – that massive block of text that no one ever reads. We all skip by it. Always have. We just want to install the app, use the features we need, achieve our goal, but we never consider the consequences.
Would you ever blindly sign a contract in real life?
I bet not.
Then why do we do it online?
One explanation is that we are sometimes under the impression that the things we digitally “sign” online are less important than those we sign in real life or don’t have consequences that reflect into the real world. But the online world and the real world are not separated. They’ve actually never been, but now it’s true more than ever that the consequences of our online actions are reflected into our offline lives. Just look at the Ashley Madison hack for a self-explanatory example.
I’m not saying that you should start reading heaps of EULAs, but at least try browsing through them, especially if it’s an important service, such as your email service of choice or the social network you spend most of your time on.
There’s even an add-on that can make this tedious task easier: Terms of Service; Didn’t Read.
There are too many cases where apps collect much more information that it would be necessary, or even legal. So don’t let that happen to you. Get informed and get protected.

11. Connecting to public Wi-Fi
You’re spending the night out with friends and want to show them a funny video, so you connect to the bar’s Wi-Fi.
You’re travelling and roaming rates are expensive, so you take advantage of the airport’s Wi-Fi to see how to get from the airport to your hotel.
You’re on a train and you want to get some work done before you get to work, so you use the public Wi-Fi hotspot to check your email and send important documents.
These are all situations that happen on a daily basis, which is a real issue, because public Wi-Fi networks are unsafe and ridiculously easy to hack.
By using a fake Wi-Fi hotspot, cyber criminals can see and collect all the information that you’re sending and receiving via that connection, including passwords, everything stored on your phone or essential details about your PC.
Imagine what would happen if you buy something online while using a public Wi-Fi hotspot. All your credit card details will then fall into the attackers’ hands, practically inviting them to take your money.
Using public Wi-Fi is never a good idea, especially if you don’t take adequate precautions (install a VPN, use an antivirus, use anti-malware protection and don’t purchase anything online while using this connection). So it’s probably better to just wait until you can use a secure connection.
But if you really, really need to use public Wi-Fi, here’s how you can keep safe.
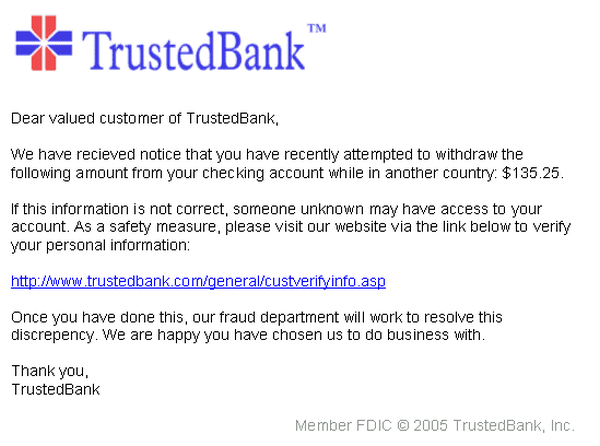
12. Not being able to spot a phishing attack
Phishing attacks are so cleverly created that they could fool even some of the most experienced Internet users. The purpose of these attacks is to get you to divulge confidential information, such as usernames, passwords, and credit card details.
The bait is usually an email or a website designed to masquerade as a trustworthy entity (your bank, a service provider or a public institution), so you will relinquish your most sensitive information without suspecting that there’s a malicious server collecting your data at the other end.
Phishing attacks are becoming increasingly common on social media as well, which is why a cautious attitude is a key asset. Attackers can even do this by phone, so here’s another reason to teach yourself about the most serious cyber threats out there, since they often use psychological manipulation to compromise you.
Spam protection, safe browsing and ensuring that a connection is secure are the key provisions to make in order to protect yourself from phishing attempts. This guide on securing your browsers is the first step, and everything you’ll learn about cyber security is the next one.

13. Sharing every aspect of your private life on social media
Oversharing is not only a big privacy issue, but a cyber security issue as well. All the information you post online can be collected and used against you or to compromise you.
Checking in while at home will reveal your location, sharing baby pictures will divulge information about your family and provide a rich background that cyber criminals can use to then attack you via phishing attempts or using social engineering techniques.
Sharing less is wiser. Sharing as little as possible, even more so.
[Tweet “Here’s how oversharing is decreasing your online safety:”]Of course, for those who need an online personal brand, social media is essential, but you should be aware of the risks and take adequate precautions if you’re going to share all the details of your private life with the world. In the meanwhile, here’s how to keep safe on Facebook, Instagram, LinkedIn and Twitter.

14. Not realizing that everything you put online is, by no means, private
Once you put something online, it’s no longer private. And this doesn’t only include stuff shared on social media. Your emails can become public if a cyber criminal gets a hold of them (and if you’re using weak passwords, it’s only a matter of time until it happens). Your cloud-stored photos could suffer the same fate (which is why multiple backups are recommended).
Your Facebook page, your Twitter account, your Instagram pics – they are all public, no matter if your profile is private. Every piece of content you public on platforms owned by someone other than yourself is no longer yours and you need to realize that.
Fooling yourself into believing that this is not true will only make you more vulnerable to cyber attacks.
And here’s another nugget to remember:
Everything and everyone can be hacked.
So don’t work against yourself and make it even easier for malicious individuals to compromise you.
15. Signing up for a new service/app using your social media accounts
Ah, the social sign in! It was great when it first came up: you could easily sign up for a new product or service with 2 clicks and get on with your business. It was easy and fast – and who doesn’t like easy and fast? But using an account to sign up for another service is not such a good idea.
For example, if your Facebook account should be compromised, every account linked to it will suffer the same fate. Expand that to every social login you’ve ever used and you have a pretty accurate picture of how you’re standing in terms of cyber security, at least from this perspective.
Remember this: everything we do online is linked. Our email addresses, our social media accounts, the tools we use, our apps and other software – everything is bound together by data. Should an attacker find its way into our digital lives, they can easily gain access to all of it.
Unless we do something about it.

16. Forgetting to clean up your online accounts once in a while
If you don’t keep a list of all the accounts you’ve ever created, maybe it’s time to start one now. Keeping track of your accounts on several platforms, apps and other services is a good way to see which accounts you use frequently and which accounts you haven’t logged into for years.
A good idea is to delete the accounts you no longer use. There’s no reason for a company to keep storing your data if you don’t use their service/product anymore. Plus, if you’ve ever reused passwords, this is a good way to make sure that you’re reducing your vulnerabilities.
It’s just like cleaning your closet, but, you know, digitally. You may not see the clutter, but it’s still there and not being able to control it at all will only cause you trouble.
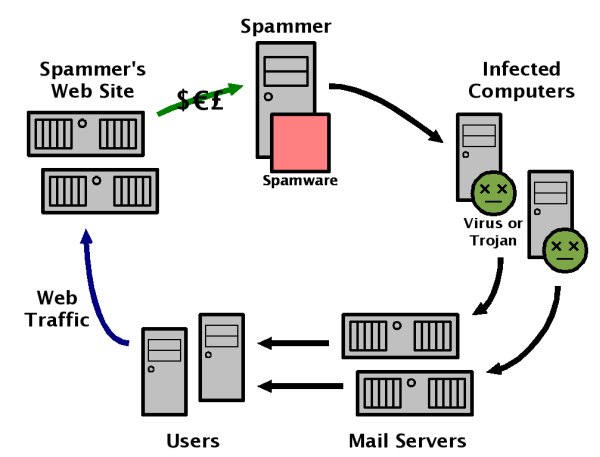
17. Opening emails from strangers
Nowadays, parents should teach their kids two things: never talk to strangers and never open an email from a stranger.
I bet you get a lot of spam emails, we all do. Some may even have catchy subject lines or promise a huge discount on that product you love. But, please, by any means, don’t open them!
Spam emails won’t just clutter your inbox, but they might come loaded with malware, ransomware or other nasty threat. Verify the sender before opening your email and send it directly to spam if an unsolicited email made its way in your inbox.

18. Auto-connecting to Wi-fi and keeping Wi-fi on even while it’s not in use
We all like this idea, right? It makes us a little fuzzy inside. But auto-connecting to Wi-Fi is not ideal for security. Actually, it’s a good idea to turn Wi-Fi off if you’re not using it. While your Wi-Fi is on, cyber criminals could take advantage and launch attacks that antivirus won’t detect and that you certainly won’t be able to spot.
So one more security solution is just a tap away – why not enforce it?
Conclusion
How many of these habits did you admit to?
You don’t have to share the answer or be ashamed of it, you just have to recognize which of your online habits are endangering your data and your digital life and take adequate security measures to prevent potential cyber attacks.
Also, we all know that, as the boundaries between offline and online become blurred, a lot more vulnerabilities will arise. The cyber security industry is already working around the clock to minimize risks and reduce cyber crime, but every user should also take responsibility for his/her own online safety as well.











 Network Security
Network Security
 Vulnerability Management
Vulnerability Management
 Privileged Access Management
Privileged Access Management  Endpoint Security
Endpoint Security
 Threat Hunting
Threat Hunting
 Unified Endpoint Management
Unified Endpoint Management
 Email & Collaboration Security
Email & Collaboration Security








