Contents:
Zyxel released updates to fix a critical vulnerability that impacts 28 access points (AP) and security router version.
The Zyxel vulnerability is tracked as CVE-2024-7261 and has a 9.8 CVSS score, which is considered critical. The flaw enables hackers to run arbitrary commands on the target’s operating system remotely.
The improper neutralization of special elements in the parameter “host” in the CGI program of some AP and security router versions could allow an unauthenticated attacker to execute OS commands by sending a crafted cookie to a vulnerable device.
Source – Zyxel Security Advisory
Chengchao Ai from Fuzhou University’s ROIS team discovered and reported the vulnerability to Zyxel.
What products does the Zyxel OS vulnerability impact?
The company published a list of 29 products – 28 APs and a router version – that are vulnerable to CVE-2024-7261. In their security advisory, you can find details about the product type, the model, the version, and the available patch.
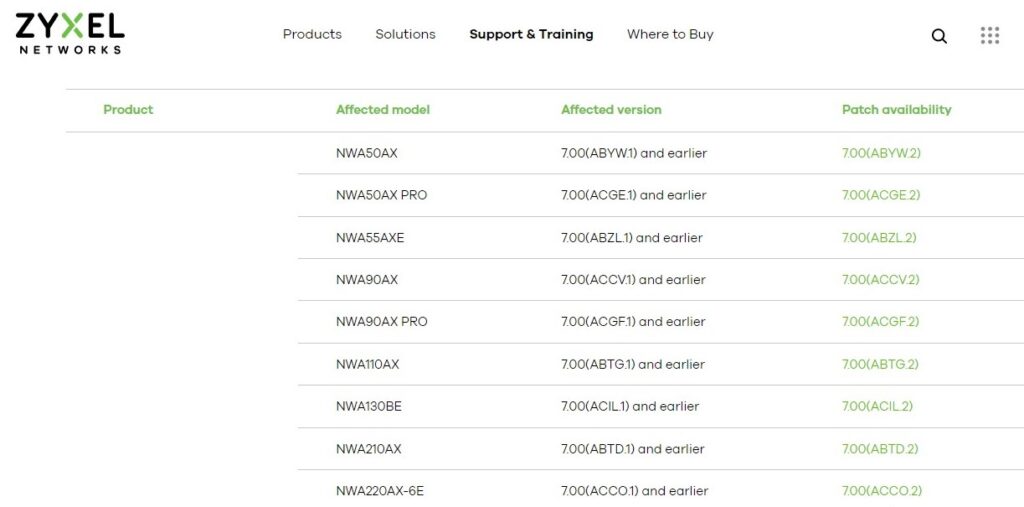
Source – Zyxel Security Advisory
Although vulnerability assessment and patch management can be challenging for some companies, security experts warn users to patch timely. Because of the nature of the affected products, exploiting CVE-2024-7261 could result in spreading the infection at a network level.
For additional information or guidance regarding the patching process, visit the company’s Community page.
8 more Zyxel vulnerabilities revealed the same day
The same day, September 3rd, Zyxel released 2 other advisories regarding 8 more vulnerabilities. Seven of them impact firewall versions:
CVE-2024-6343
buffer overflow vulnerability in the CGI program can enable an authenticated attacker with administrator privileges to cause denial of service (DoS)
CVE-2024-7203
command injection vulnerability that requires authentication. It can lead to execute OS commands by running a crafted CLI command.
CVE-2024-42057
command injection vulnerability in the IPSec VPN feature. It enables unauthenticated attacker to execute certain OS commands only if the device was configured in User-Based-PSK authentication mode and has a valid user with a username exceeding 28 characters.
CVE-2024-42058
null pointer dereference vulnerability that an unauthenticated threat actor can use to cause DoS.
CVE-2024-42059
command injection vulnerability that enables an authenticated attacker with admin rights to execute some OS commands.
CVE-2024-42060
command injection vulnerability allowing authenticated attackers with admin privileges to run OS commands by uploading a crafted internal user agreement file to the vulnerable device.
CVE-2024-42061
reflected cross-site scripting (XSS) vulnerability in the CGI program “dynamic_script.cgi” that enables threat actors to trick a user into visiting a crafted URL with the XSS payload.
You can find a complete description and available patches for all seven here.
The eight vulnerability, CVE-2024-5412, impacts 5G NR CPE, DSL/Ethernet CPE, fiber ONT, WiFi extender, and security router devices. This buffer overflow vulnerability enables an unauthenticated malicious actor to inflict a denial of service (DoS) attack by sending a crafted HTTP request to vulnerable devices.
Patching 9 vulnerabilities for one device can take long, depending on the infrastructure’s size and complexity. Using automated patch management software helps avoid leaving the gate open long enough for hackers to exploit the flaws. Here’s why you should prioritize closing vulnerabilities:
If you liked this article, follow us on LinkedIn, Twitter, Facebook, and Youtube, for more cybersecurity news and topics.










 Network Security
Network Security
 Vulnerability Management
Vulnerability Management
 Privileged Access Management
Privileged Access Management  Endpoint Security
Endpoint Security
 Threat Hunting
Threat Hunting
 Unified Endpoint Management
Unified Endpoint Management
 Email & Collaboration Security
Email & Collaboration Security








