Contents:
Please note that the term “Zerobot” in this article refers to a specific malware variant, not to zerobot.ai, an organization which offers a verbal chatbot service.
Recently, a Go-based botnet, Zerobot, was seen spreading in the wild. It took advantage of nearly two dozen different security vulnerabilities found in IoT devices and other software. The malware infects devices with a DDoS botnet, which launches powerful attacks against specified targets.
The campaign allegedly began after November 18, and primarily singles out Windows and Linux operating systems to gain control of vulnerable machines.
In their advisory, the researchers claim the botnet:
…contains several modules, including self-replication, attacks for different protocols, and self-propagation. It also communicates with its command-and-control server using the WebSocket protocol.
What Is Zerobot?
Zerobot is a propagation script that’s used to retrieve the malicious payload once it has access to a computer. It knows what kind of microarchitecture (i.e., “zero.arm64”) the host has and then uses that information to extract the payload. The malware targets a wide range of CPU architectures, including i386, amd64, arm, arm64, mips, mips64, mips64le, mipsle, ppc64, ppc64le, riscv64 and s390x.
Two distinct versions of Zerobot have been observed to date:
- One used before November 24, which includes basic functions,
- The updated version with a self-propagating module that can breach other endpoints by making use of 21 exploits.
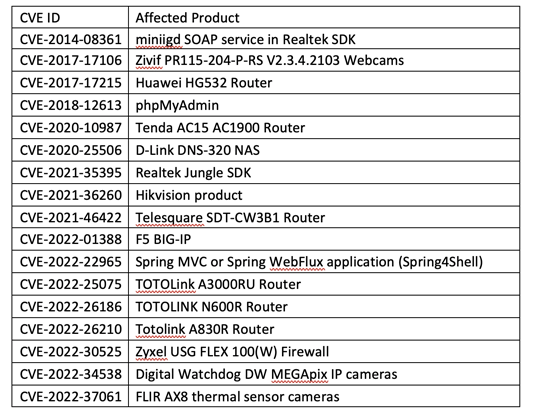
Some common vulnerabilities that are included in the update include TOTOLINK routers, Zyxel firewalls, F5 BIG-IP, Hikvision cameras, FLIR AX8 thermal imaging cameras, D-Link DNS-320 NAS, and Spring Framework.
The advisory lists the exploited flaws as follows:
Furthermore, Zerobot will establish contact with a remote C2 server and await instructions that allow it to launch DDoS attacks for different network protocols like TCP, UDP, TLS, HTTP, and ICMP.
The C2 may follow-up with one of these commands:
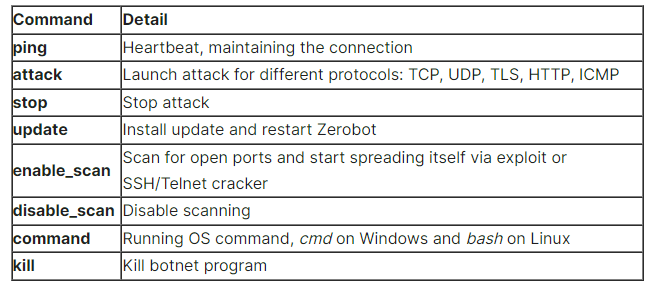
Additionally, the malware also uses an anti-kill module designed to protect it from being turned off or unable to load.
Zerobot first appeared mid-November and since then, its developer has improved it with a string obfuscation module, a copy file module, a self-propagation module, and several new exploits.
Despite its current focus being the launch of DDoS, Zerobot could be eventually used as both an initial access and launch point for future cyberattacks.
If you liked this article, follow us on LinkedIn, Twitter, Facebook, Youtube, and Instagram for more cybersecurity news and topics.










 Network Security
Network Security
 Vulnerability Management
Vulnerability Management
 Privileged Access Management
Privileged Access Management  Endpoint Security
Endpoint Security
 Threat Hunting
Threat Hunting
 Unified Endpoint Management
Unified Endpoint Management
 Email & Collaboration Security
Email & Collaboration Security







