Contents:
In an effort to trick targets into handing over large sums of money, a Business Email Compromise (BEC) campaign uses an email thread that claims to have been forwarded by the manager.
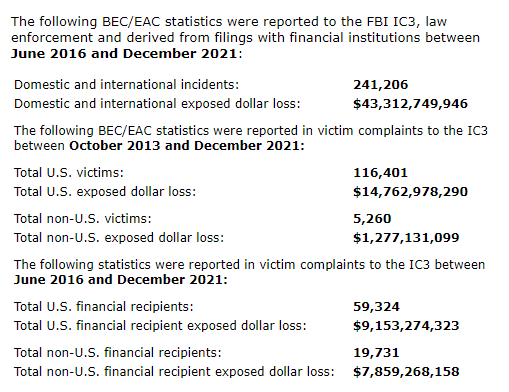
According to the FBI, BEC attacks are among the most profitable types of cybercrime, costing victims a combined total of over $43 billion in recent years. They’re also among the easiest to execute because all an attacker needs is an internet connection, an email account, and possibly some background research on their targets.
BEC emails frequently appear to be from a coworker or manager and demand that a wire transfer is made right away and discretely. Scammers hope that creating a sense of urgency will be sufficient to deceive the unfortunate target into submitting a false payment.
Fraud Disguised as Forwarded Email
One of these more sophisticated BEC campaigns is made to deceive victims into thinking their boss has forwarded an ongoing thread asking them to deal with an invoice and make a payment – which is sent to the scammer’s account.

Cybersecurity researchers from Abnormal Security refer to it as “a sophisticated new business email compromise attack” that combines executive and vendor impersonation. Attacks are even designed to appear like they are coming from a specific executive of the company the target victim works for using email spoofing.
The “boss” asks the victim to set up a financial transaction related to a business payment that is mentioned in the forwarded email in order to make the attack appear more convincingly like it is a part of an ongoing thread.
To make the attack appear more credible, it is deliberately designed to be part of an ongoing thread, with the “boss” asking the victim to set up a financial transaction related to a business payment referenced in the forwarded email. However, just like the message from the “boss,” the forwarded request for an invoice is a hoax orchestrated by scammers as part of the bait.
How Do BEC Attacks Operate?
The attackers use an invoice request that appears to be paid to a legitimate company and hopes the target organization might have a genuine business relationship with the victim will follow the instructions and make the transfer without querying or informing anyone else.
Furthermore, BEC attacks frequently resist email security measures because no malware or malicious code is used in them. Clever, right?
Like all BEC attacks, the reason traditional email defenses have a difficult time detecting them is because they don’t contain any of the static indicators most defenses look out for, like malicious links or attachments. Most BEC attacks are nothing more than pure, text-based social engineering that traditional email defenses are not well-equipped to detect.
The campaign, which has been going on since July 2022, is thought to be the work of a group known as Cobalt Terrapin, which seems to operate out of Turkey, according to analysis of the attacks.
Prevention is Key
As ZDNet explained, since BEC campaigns rely on social engineering rather than malware or other malicious activity that can be identified by anti-virus software, it can be challenging to protect against them. This is why prevention is key in identifying BEC email threats:
- Start with training employees to spot scam emails. By verifying the accuracy of the email, for instance, or by checking to see if an unexpected message with a strangely urgent matter has been sent.
- Additionally, staff should be instructed to use a different form of communication, such as phone or instant messaging, to confirm any suspicious requests.
- Always double-check. In a hectic work environment, taking the time to double-check a request may seem counterintuitive, but it could prevent you from risking the loss of hundreds of thousands of dollars to a BEC attack.
If you liked this article, follow us on LinkedIn, Twitter, Facebook, Youtube, and Instagram for more cybersecurity news and topics.


 Network Security
Network Security
 Vulnerability Management
Vulnerability Management
 Privileged Access Management
Privileged Access Management
 Endpoint Security
Endpoint Security
 Threat Hunting
Threat Hunting
 Unified Endpoint Management
Unified Endpoint Management
 Email & Collaboration Security
Email & Collaboration Security










