Contents:
Researchers have discovered a new ransomware strain dubbed Yanluowang ransomware, that is still in the development process. Its targets? Enterprise entities.
Yanluowang Ransomware: the Name Story
The recent strain was discovered by the threat hunter team from Broadcom’s Symantec and, at a first glance, it stands out through its distinct nickname, which is inspired by the name of a Chinese deity: Yanluo Wang. According to Chinese mythology, he was the Death’s God and Diyu’s Fifth Court Ruler (Diyu being depicted as the Chinese hell). The identification of this particular choice of name seems to be related to the extension it uses for file encryption on affected systems.
How Does Yanluowang Ransomware Work?
According to researchers’ report on this topic, the ransomware strain was discovered while an investigation was ongoing for an incident related to some suspicious activity detection in a high-profile company. This dubious activity was linked to the AdFind command line. As a rule, threat actors use AdFind to achieve data access that will later allow them to perform lateral movement onto the network. AdFind stands basically for a free command-line query tool used for the purposes of Active Directory data gathering.
So hackers tried to deploy Yanluowang ransomware payloads on the compromised system of the company under discussion and the process unfolded like this:
Step 1
A malicious tool is launched in an a priori activity before the ransomware is deployed. Therefore, this tool has the role to develop a .txt file containing remote machines’ numbers. This will help in verifying the command line. Then, by making use of WMI (Windows Management Instrumentation) the same tool will manage to get to know which processes run on the remote machines from the before mentioned file. Then all the processes and names of the machines will go under processes.txt.
Step 2
What the ransomware does after the initial phase, once it is deployed, will be to:
- Make hypervisor virtual machines stop;
- The identified processes by that malicious tool will be terminated.
- File encryption;
- the .yanluowang extension is attached (and from here the name of the ransomware).
Step 3
What happens next? The system gets encrypted, so at this point, Yanluowang will drop a ransom note. This comes in the form of a README.txt file. The victims are warned against announcing law enforcement or calling upon ransomware negotiation organizations to help them.
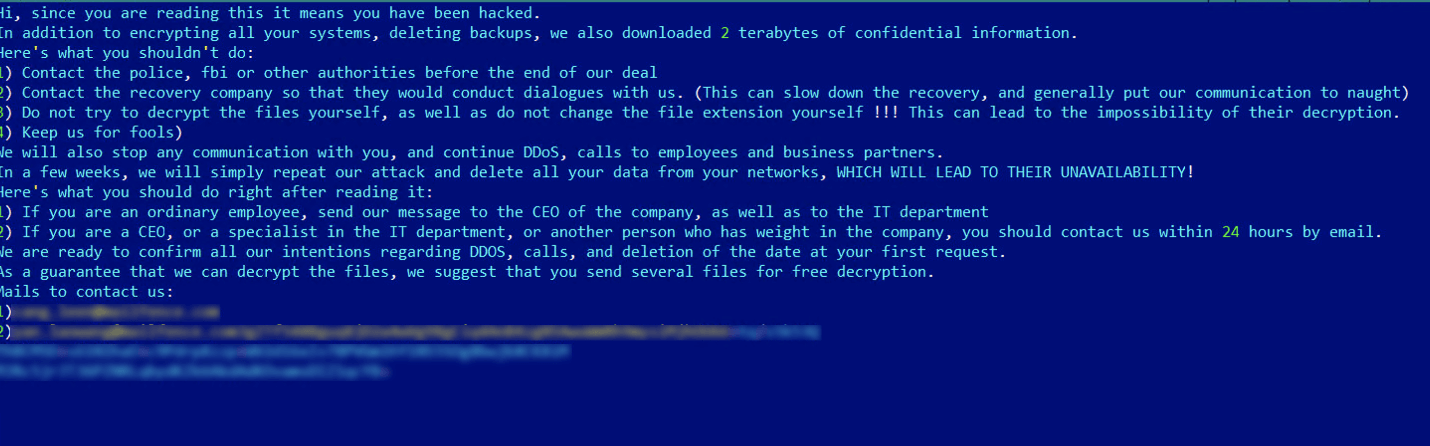
According to the same researchers, threat actors threaten to further engage in DDoS attacks if the rules specified are broken by the victims.
If the attackers’ rules are broken the ransomware operators say they will conduct distributed denial of service (DDoS) attacks against the victim, as well as make ‘calls to employees and business partners. (…) The criminals also threaten to repeat the attack “in a few weeks” and delete the victim’s data”.
How to Stay Safe?
Ransomware is the most popular cyberthreat nowadays and the cybercriminals behind it have been developing for a while advanced techniques to make sure they get their money: for instance, double extortion, where the companies data is stolen before encryption and then the organizations are threatened with data leakage if the ransom is not paid.
We at Heimdal™ are always up to date with the current happenings on the cyberthreat landscape, offering solutions that will enhance your cyber defenses. Benefit from our Ransomware Encryption Protection, a revolutionary product 100% signature-free and say goodbye to exfiltration and data loss.


 Network Security
Network Security
 Vulnerability Management
Vulnerability Management
 Privileged Access Management
Privileged Access Management
 Endpoint Security
Endpoint Security
 Threat Hunting
Threat Hunting
 Unified Endpoint Management
Unified Endpoint Management
 Email & Collaboration Security
Email & Collaboration Security










