Contents:
Cybersecurity researchers have issued a warning about SysJoker, a brand-new multiplatform malware that targets Windows, Mac, and Linux. According to them, the backdoor is able to remain undetected on all three operating systems.
The new backdoor was initially discovered in December 2021 by experts at security software company Intezer during an active attack on a Linux-based web server of a leading educational institution.
The researchers believe that the SysJoker attack began during the second half of 2021, based on command and control (C2) domain registration and the samples discovered in VirusTotal.
More on SysJoker Malware
The newly discovered backdoor is written in C++ programming language, and while each version is customized for the targeted operating system, they all go unnoticed on VirusTotal, an online malware scanning tool that uses 57 different antivirus detection engines.
SysJoker Backdoor M.O.
As explained by BleepingComputer, the Windows version, unlike the Mac and Linux samples, includes a first-stage dropper. The dropper is a DLL that uses PowerShell commands to download the SysJoker ZIP from a GitHub repository, unzip it on “C:ProgramDataRecoverySystem,” and run the payload.
As per the report, when the backdoor is executed, it sleeps for 90 to 120 seconds. Then it will start creating the C:ProgramDataSystemData directory and copy itself there, posing as igfxCUIService.exe (Intel Graphics Common User Interface Service).
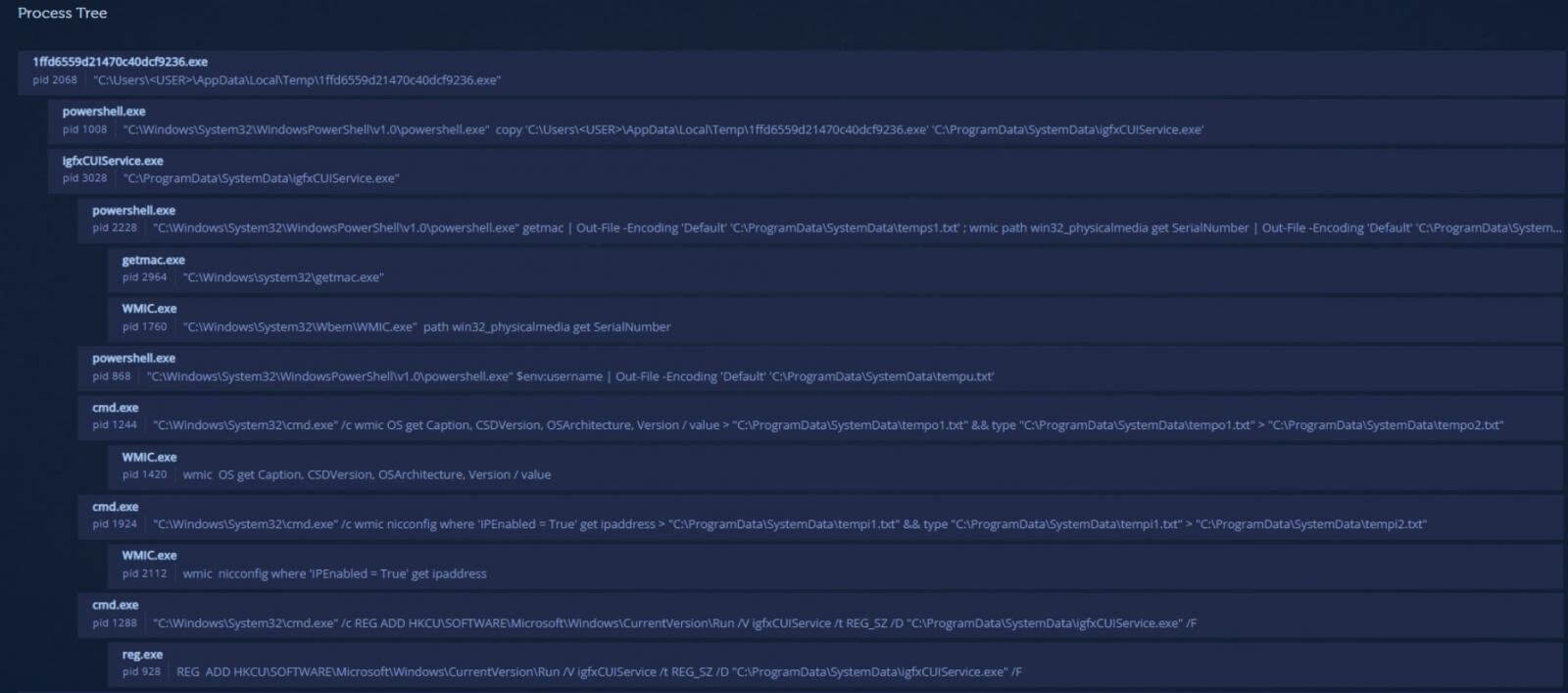
Next, SysJoker will gather information about the machine using Living off the Land (LOtL) commands. SysJoker uses different temporary text files to log the results of the commands.
These text files are deleted immediately, stored in a JSON object and then encoded and written to a file named “microsoft_Windows.dll”.
After the collection of system and network data, the virus will establish persistence by creating a new registry key (HKEY CURRENT USERSoftwareMicrosoftWindowsCurrentVersionRun). Random sleep periods are interlaced between all functions leading up to this point.
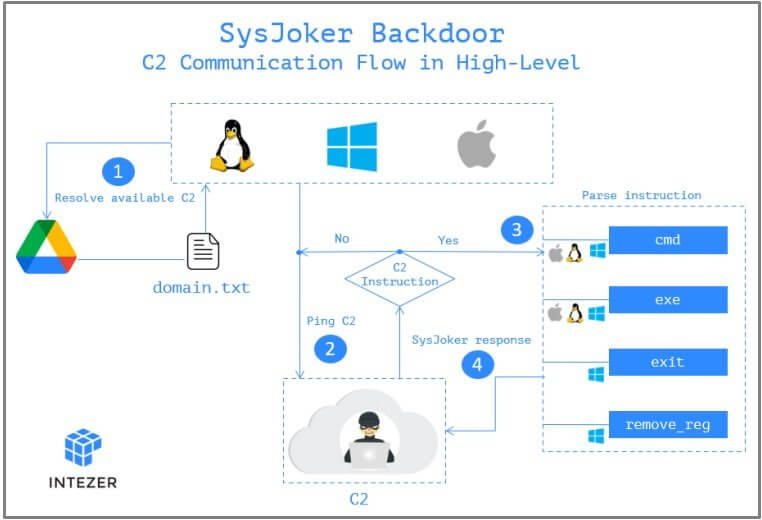
Following this, the backdoor reaches out to the C2 server controlled by the attacker via a hardcoded Google Drive link.
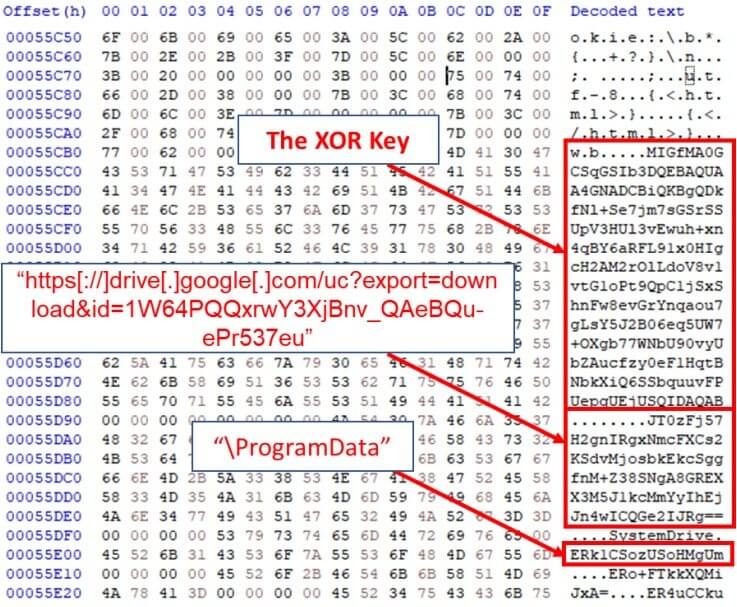
The link hosts a “domain.txt” file, which the hackers keep up to date in order to provide available servers to live beacons. This list is regularly updated to bypass detection and blocking.
The data gathered during the initial stages of the infection is sent to the C2 as the first handshake. The C2 responds with a unique token that serves as the compromised endpoint’s identifier.
The C2 may then instruct the malware to deliver more malware, execute commands on the affected machine, or delete the backdoor from the device. Those last two commands, however, have yet to be applied.
How to Stay Safe?
Intezer’s report includes detailed indicators of compromise (IOCs) that administrators can use to determine whether a device is infected with SysJoker.
If you have been compromised, take the following steps:
- Kill the processes related to SysJoker, delete the relevant persistence mechanism, and all the files;
- Ensure that the compromised device is clean by running a memory scanner;
- Investigate the initial entry point of the backdoor. If a server was infected with SysJoker, check:
- Configuration status and password complexity for publicly facing services
- Used software versions and possible known exploits
If you liked this article, follow us on LinkedIn, Twitter, Facebook, Youtube, and Instagram for more cybersecurity news and topics.


 Network Security
Network Security
 Vulnerability Management
Vulnerability Management
 Privileged Access Management
Privileged Access Management
 Endpoint Security
Endpoint Security
 Threat Hunting
Threat Hunting
 Unified Endpoint Management
Unified Endpoint Management
 Email & Collaboration Security
Email & Collaboration Security










