Contents:
FontOnLake is a previously unknown malware family that is targeting any systems running Linux.
The malware has a limited incidence in the wild and has a sophisticated architecture that allows it to remain persistent on an infected machine for long periods of time.
ESET researchers have discovered a previously unknown malware family that utilizes custom and well-designed modules, targeting systems running Linux. Modules used by this malware family, which we dubbed FontOnLake, are constantly under development and provide remote access to the operators, collect credentials, and serve as a proxy server.
In May 2020, the first FontOnLake file was discovered on VirusTotal, and further samples were posted throughout the year. The attackers are targeting Southeast Asia, based on the location of the command-and-control server and the countries from which samples were uploaded to VirusTotal.
We believe that FontOnLake’s operators are particularly cautious since almost all samples seen use unique [C2] servers with varying non-standard ports.
According to BleepingComputer, among the Linux utilities that the threat actor altered to deliver FontOnLake are:
cat – used to print the content of a file
kill – lists all running processes
sftp – secure FTP utility
sshd – the OpenSSH server process
Trojanized programs, backdoors, and rootkits are among the malware’s recognized components, which communicate with one another.
Researchers discovered a number of Trojanized apps, the majority of which was used to load bespoke backdoor or rootkit modules. The three backdoors found are all built-in C++, and they all exfiltrate acquired credentials as well as their bash command history to the C2 server. In each of the three backdoors, researchers discovered two “marginally different” versions of the rootkit, which were employed one at a time.
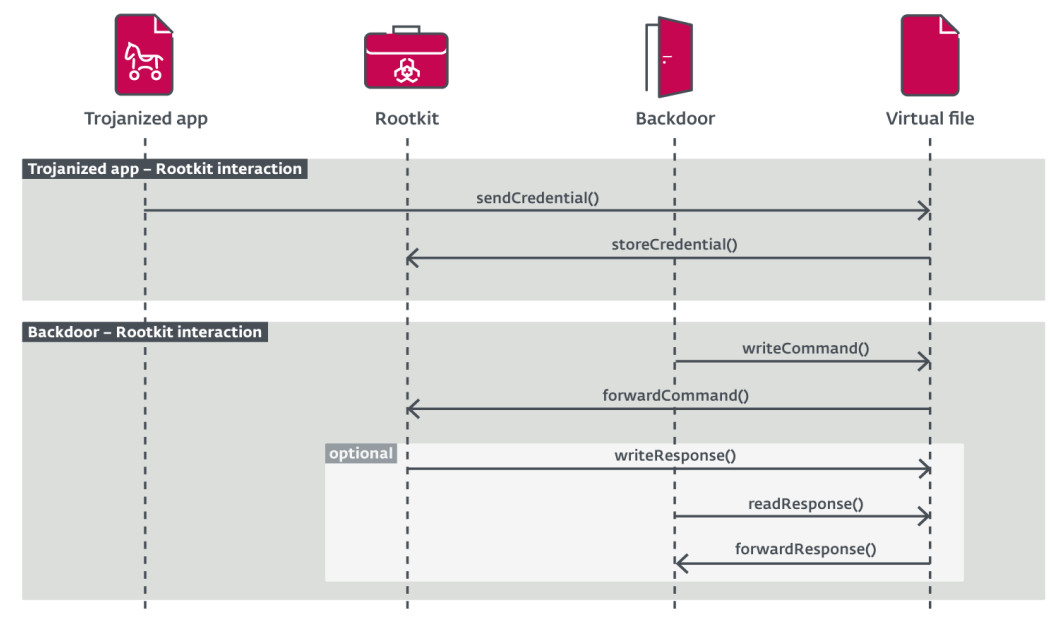
According to the researchers, FontOnLake’s presence on a compromised system is hidden by a rootkit component, which is also responsible for updates and for the delivery of fallback backdoors.
The researchers discovered rootkit samples for kernel versions 2.6.32-696.el6.x86 64 and 3.10.0-229.el7.X86 64. The two versions identified are based on Suterusu, an open-source rootkit project that has been around for eight years and can hide programs, files, and network connections.
The rootkit and trojanized applications communicate through a virtual file that the latter generates. The backdoor component can read or write data to this file, which can then be exported by the operator.
The researchers think the creator of FontOnLake is “well-versed in cybersecurity,” and after they heard of the upload, they disabled the C2 servers utilized in the samples identified on VirusTotal.


 Network Security
Network Security
 Vulnerability Management
Vulnerability Management
 Privileged Access Management
Privileged Access Management
 Endpoint Security
Endpoint Security
 Threat Hunting
Threat Hunting
 Unified Endpoint Management
Unified Endpoint Management
 Email & Collaboration Security
Email & Collaboration Security










