Contents:
When developing a risk mitigation plan, companies must consider a DLP solution (Data Loss Prevention).
Essential for compliance, DLP protects sensitive data from leaks, breaches, and unauthorized access across various platforms.
This article explores DLP solutions, their limitations, and their relevance for your business environment.
What is a DLP solution?
DLP (Data Loss Prevention) detects and prevents data leaks and exfiltration through continuous monitoring and company-defined security policies.
It operates at various levels, including network, endpoint, and storage.
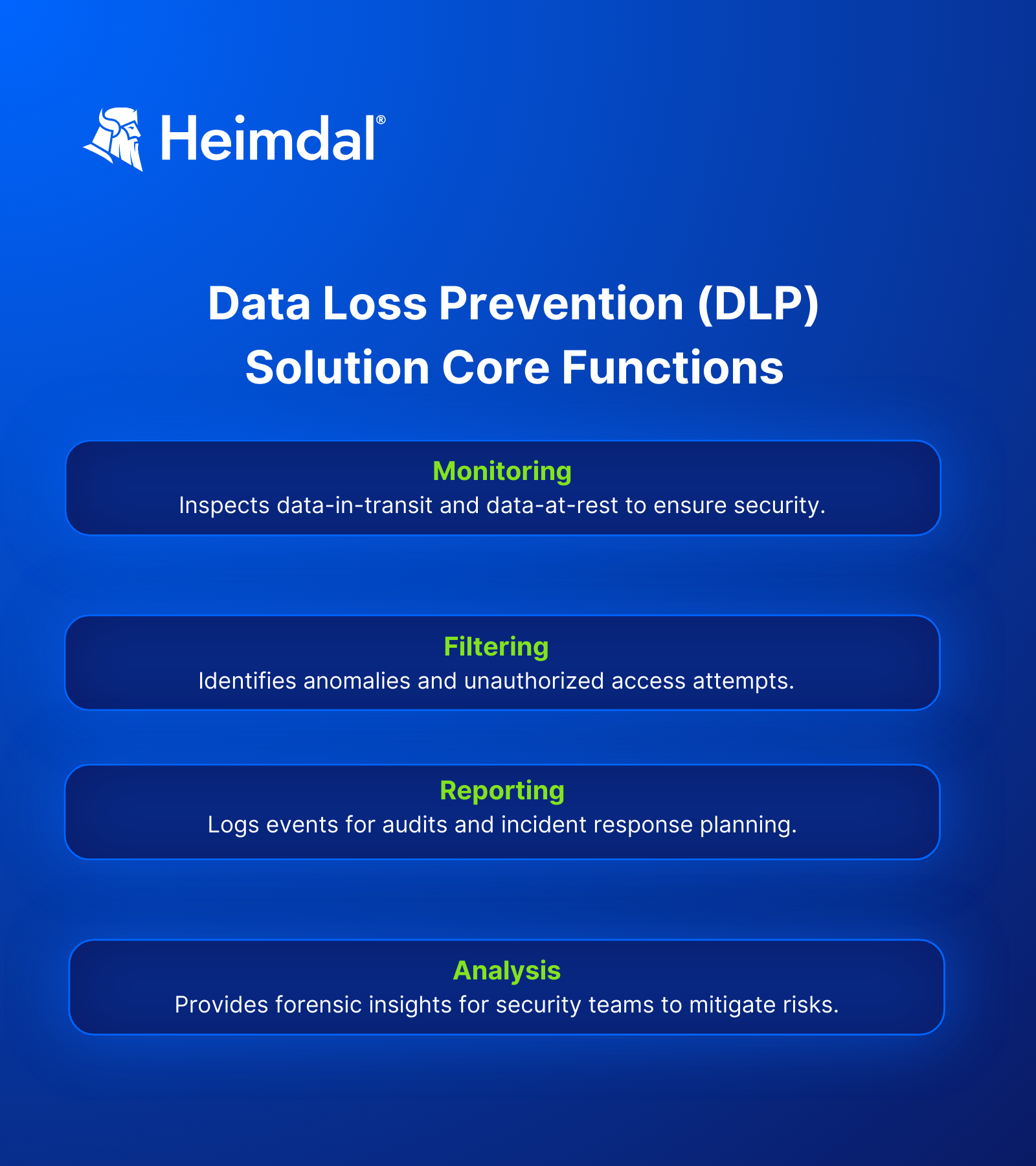
A DLP solution must fulfill four core functions.
DLP data feeds into DLP Ops, which includes triage, reporting, and escalation to enhance cybersecurity response.
Open Source and Paid DLP Solutions
Open-source DLP solutions are cost-effective but require IT expertise for customization and maintenance, potentially increasing long-term costs.
Explore this list of open-source and paid DLP solutions to find the right fit.
#Heimdal’s Privilege Elevation and Delegation Management (PEDM)
Although not a true DLP solution, Heimdal’s PEDM solution can aid in in strengthening your data loss prevention strategies by securing privileged accounts and controlling access to sensitive systems—all from a unified dashboard.
Heimdal Privilege Elevation and Delegation Management (PEDM) Key Features
- Granular Access Control. Secure remote access with encrypted connections and no additional software.
- Credential Vault & MFA. Protects privileged account credentials with multiple authentication methods.
- Automated Workflows. Just-in-time access requests ensure temporary, controlled permissions.
- Threat Analytics & Monitoring. Provides real-time session tracking, forensic data, and compliance support.
- Seamless Integration. Works with IAM, SIEM, and on-premises or cloud environments for continuous protection.
By automating access security and monitoring privileged activity, Heimdal’s PEDM reduces insider threats and data exposure risks, reinforcing DLP strategies across organizations.
Heimdal Privilege Elevation and Delegation Management (PEDM) Pros
- Granular Access Control. Enables precise management of user privileges, allowing temporary elevation of rights as needed.
- Enhanced Security. Reduces the risk of prolonged privileged access, thereby minimizing potential vulnerabilities.
- User-Friendly Interface. Facilitates easy requests for admin rights and automatic revocation after a predefined period.
Heimdal Privilege Elevation and Delegation Management (PEDM) Cons
- Dashboard Navigation. Some users find the dashboard complex, which can make locating specific features challenging.
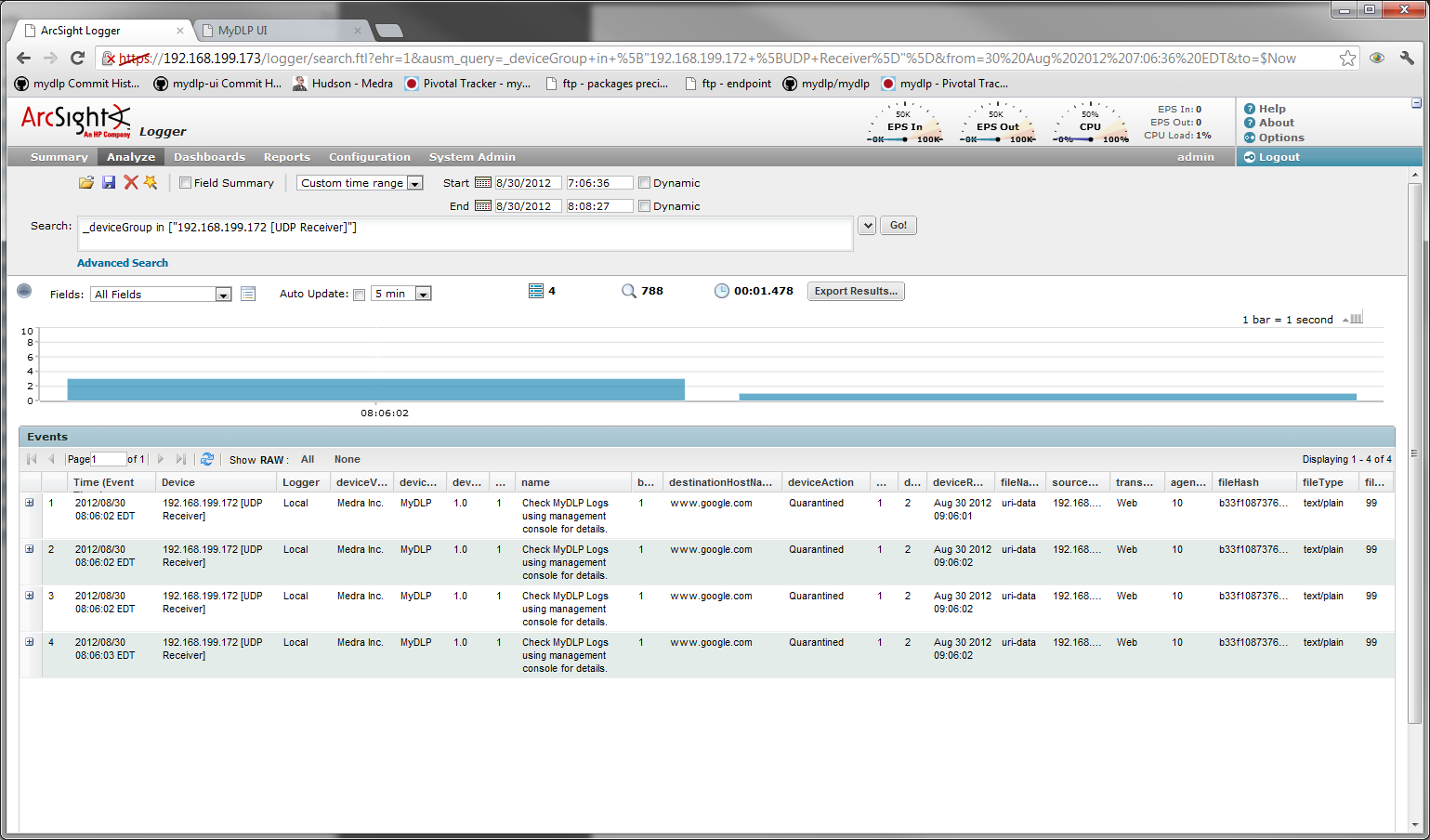
MyDLP is a free Data Loss Prevention solution that sports out various data-inspection features such as IM (Instant Messaging), FT (File Transfer), web, mail, printers, and removable storage devices.
MyDLP Key Features
- Administer and enforce Data Loss Prevention policies.
- Collect and display all event logs in a single dashboard.
- Create, edit, and manage different roles.
- Integrate with Microsoft Exchange.
- Blacklist emails that contain BCC addresses outside the company.
- Deploy or update new policies via Microsoft AD or SCCM.
- Filter and block data flow carrying sensitive information.
- Scan sensitive data to ensure compliance with data security regulations.
MyDLP Pros
- Open-Source Availability. Being open-source, it offers cost advantages and flexibility for customization.
- Centralized Management. Provides a unified console for managing data protection policies across the organization.
MyDLP Cons
- Limited Support. As an open-source solution, it may lack dedicated customer support, relying instead on community assistance.
- Scalability Challenges. May face performance issues in large-scale deployments due to resource constraints.
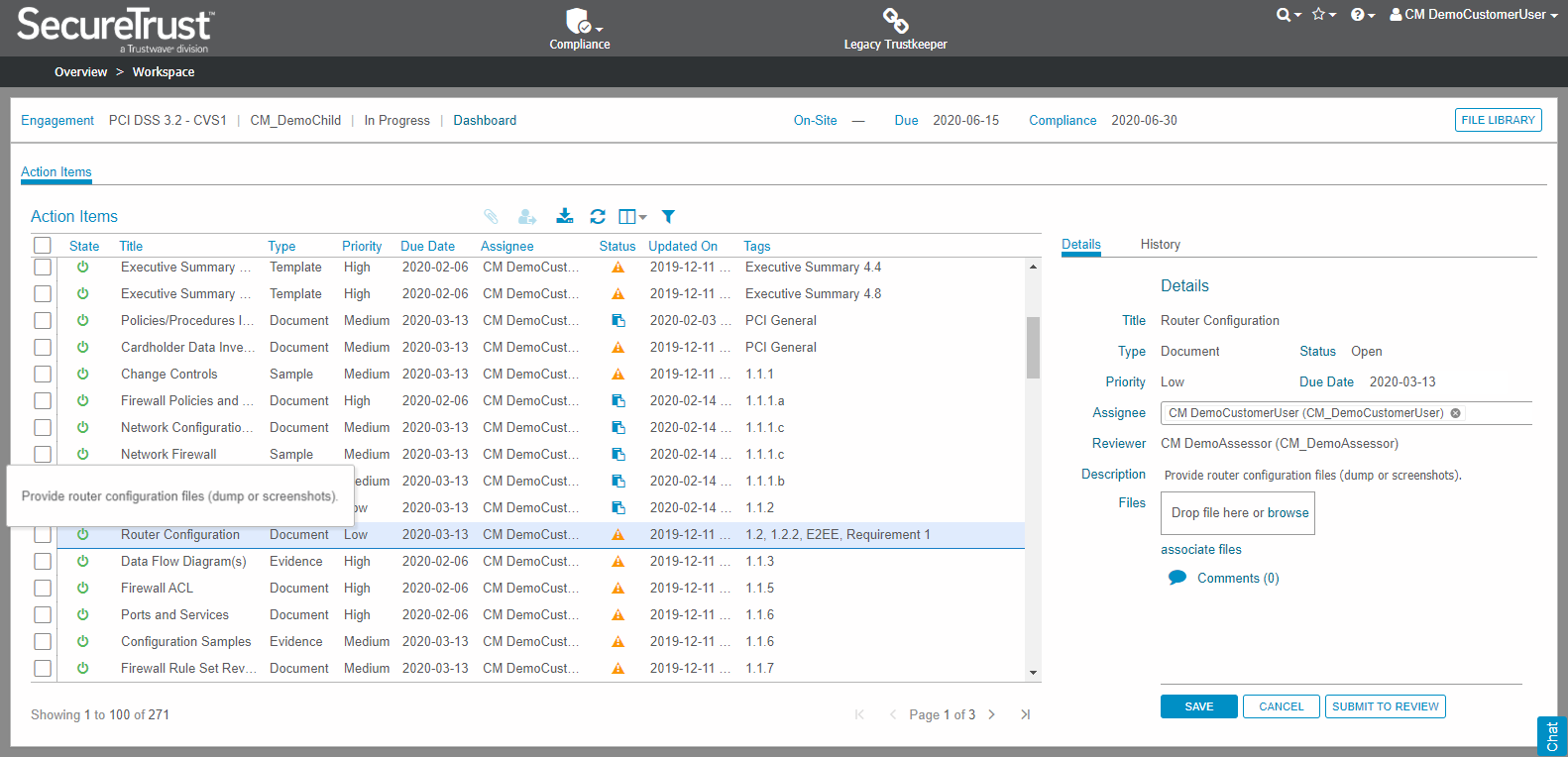
SecureTrust offers a predefined set of risk and policy settings, covering every known violation and suspicious behavior.
This DLP solution allows users to customize their rules, create new, legacy-based policies, redefine violations, add more suspicious behavior patterns, and more.
SecureTrust Key Features
- Data Discovery and Classification. Identifies and classifies sensitive data across the organization to ensure proper handling.
- Real-Time Monitoring. Continuously monitors data movement to detect and prevent unauthorized transfers.
- Compliance Management. Helps maintain compliance with various regulatory standards by enforcing data protection policies.
SecureTrust Pros
- Comprehensive Coverage. Offers extensive data protection capabilities across multiple environments.
- User-Friendly Interface. Designed for ease of use, facilitating quick deployment and management.
SecureTrust Cons
- Cost Considerations. May be relatively expensive, potentially limiting accessibility for smaller organizations.
- Complex Configuration. Initial setup and policy configuration can be intricate, requiring specialized expertise.
3. Endpoint Protector
Endpoint Protector is a Data Loss Prevention designed to identify policy violations, protect customer, employee information, and, intellectual property.
Endpoint Protector Key Features
- Content-Aware Protection. Inspects data in motion and enforces policies based on predefined and custom content.
- Device Control. Manages access to USB drives, printers, and smartphones, with granular rights set per device, user, computer, or group.
- Enforced Encryption. Automatically encrypts data copied to USB storage devices using AES 256-bit encryption.
- eDiscovery. Scans data at rest on network endpoints and applies remediation actions like encryption or deletion when confidential information is detected.
Endpoint Protector Pros
- Ease of Use and Deployment. The software can be up and running within 30 minutes and is accessible to both technical and non-technical personnel.
- Multiple Deployment Options. Options for on-premises deployment using hardware or a virtual appliance, as well as cloud-hosted solutions on platforms like AWS, Azure, and Google Cloud.
- Support for Predefined and Custom Content. Includes predefined policies and dictionaries to detect common sensitive data, and allows admins to create custom policies using advanced criteria like keywords, regular expressions, and file metadata.
- Real-Time Blocking. Immediately blocks actions that violate DLP rules in real time, preventing accidental and malicious data leaks before they occur.
Endpoint Protector Cons
- Limited Monitoring Capabilities. Focuses on device control and file transfers, lacking more granular insights into user actions within applications.
- Basic Insider Threat Prevention. Issues with sophisticated insider threats detection, such as data exfiltration through channels like emails and social media.
- Limited Application Coverage. Fails to provide adequate protection and monitoring for some third-party and proprietary applications, creating potential blind spots in data protection strategy.
- No Remote Desktop Control. Does not offer remote desktop control features, which can be valuable for incident response and user support.
Nightfall is DLP solution designed for securing IaaS and SaaS platforms, considerably reducing the chances of cloud data leakage.
The solution features over 100+ pre-tuned security policies.
Nightfall Key Features
- Machine Learning-Based Detection. Uses machine learning to identify sensitive data such as PII, PHI, and financial information across various platforms.
- Integration with Cloud Services. Seamlessly integrates with popular cloud applications like Slack, Google Drive, and GitHub to monitor and protect data.
- Real-Time Alerts and Remediation. Provides immediate notifications and automated actions to prevent data leaks.
Nightfall Pros
- Accurate Detection. Employs advanced algorithms to minimize false positives in identifying sensitive data.
- Ease of Integration. Offers straightforward integration with existing workflows and cloud services.
Nightfall Cons
- Limited to Cloud Environments. Primarily focuses on cloud applications, potentially lacking comprehensive protection for on-premises data.
- Basic Insider Threat Prevention. Lacks advanced features such as employee monitoring, screen recording, or keystroke logging, which are often essential for end-to-end insider threat detection and prevention.
- Cannot Block External Devices. Does not have robust capabilities to block or monitor data transfers to external devices, such as USB drives.
- Basic Data Protection Support. Primarily designed to protect specific types of sensitive data, such as PII, PHI, and PCI data, and may require additional resources to customize for unique or proprietary data types.
- No Remote Desktop Control. Cannot control remote devices or desktops, which is often essential for complete data protection and incident response.
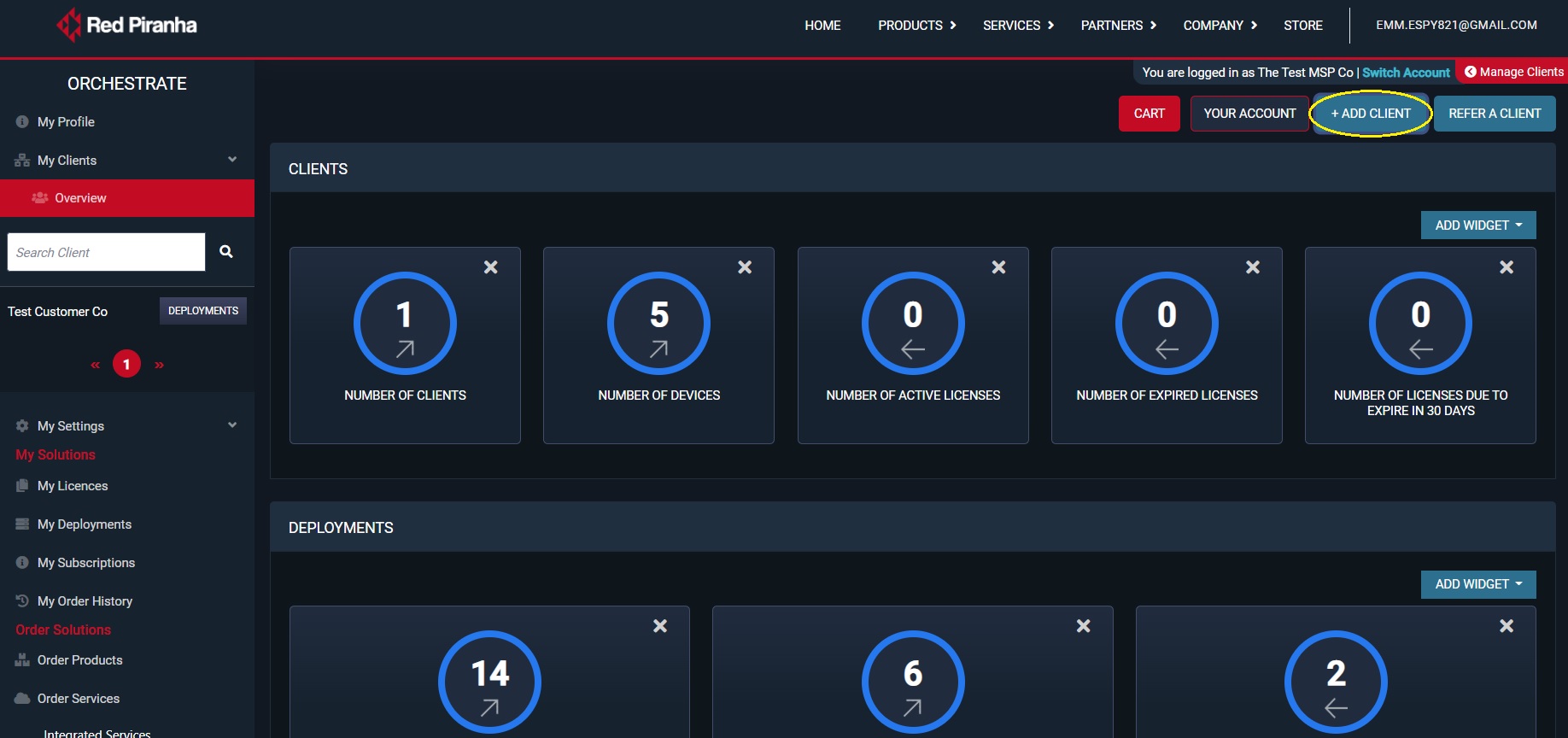
Orchestrate is a Data Loss Prevention solution that features, secure backup, containerization, data management, and recovery automation.
Orchestrate Key Features
- Automated Disaster Recovery. Streamlines recovery operations through automation, reducing manual intervention and minimizing downtime.
- Data Migration. Facilitates seamless data movement across diverse environments, supporting transitions between on-premises and cloud infrastructures.
- Data Loss Prevention (DLP). Incorporates file-level security measures to prevent unauthorized access, including periodic document encryption and secure erase functionalities.
Orchestrate Pros
- Comprehensive Automation. Enhances operational efficiency by automating complex data management tasks.
- Scalability. Capable of handling large-scale data operations, making it suitable for enterprises with extensive data assets.
- Integration Capabilities. Seamlessly integrates with various platforms and storage solutions, providing flexibility in diverse IT environments.
Orchestrate Cons
- Complex Deployment. Initial setup may require significant time and expertise due to the solution’s comprehensive capabilities.
- Resource Intensive. The extensive features and automation processes can demand substantial system resources.
- Cost Considerations. The advanced functionalities may come at a higher price point, which could be a factor for budget-conscious organizations.
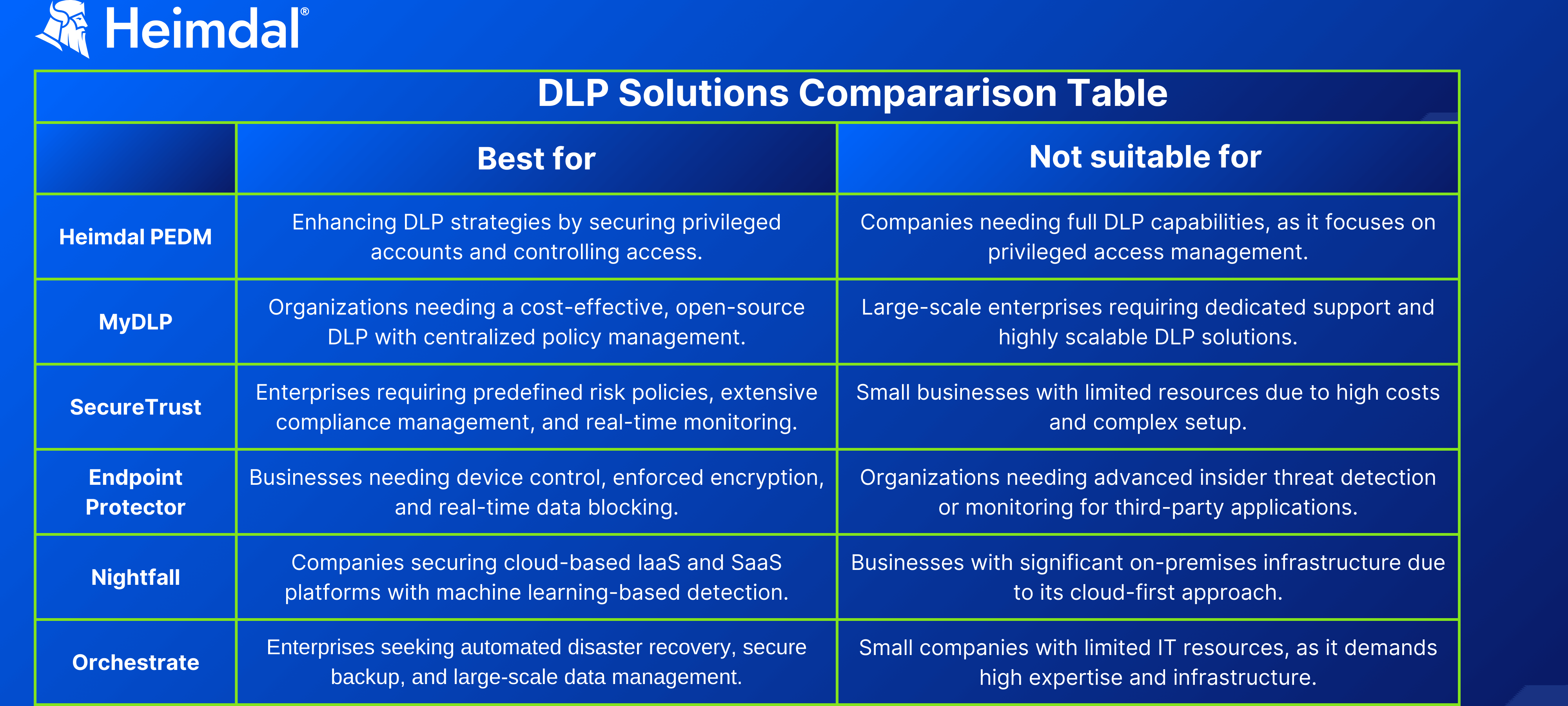
DLP Solution Comparison Table
Here’s how all of the DLP solutions stack up against each other in terms of adoption.
Conclusion
DLP complements cybersecurity by preventing data leaks and unauthorized access.
It relies on existing security frameworks for enforcement.
Before implementation, define clear policies on data classification, access controls, and endpoint security to ensure compliance and protection of sensitive information.










 Network Security
Network Security
 Vulnerability Management
Vulnerability Management
 Privileged Access Management
Privileged Access Management  Endpoint Security
Endpoint Security
 Threat Hunting
Threat Hunting
 Unified Endpoint Management
Unified Endpoint Management
 Email & Collaboration Security
Email & Collaboration Security