Contents:
While the nature of cyberattacks is constantly changing, and our lives are more and more influenced – if not affected – by global health problems, thus leaving our cybersecurity even more vulnerable, information remains the most powerful tool we have. When it comes to the cybersecurity of your business, the so-called man-in-the-middle attack is one of the threats you must be aware of.
What Is a Man-in-the-Middle Attack?
A man-in-the-middle attack represents a cyberattack in which a malicious player inserts himself into a conversation between two parties, impersonates both of them, and gains access to the information that the two parties were trying to share. The malicious player intercepts, sends, and receives data meant for someone else – or not meant to be sent at all, without either outside party knowing until it’s already too late.
You might find the man-in-the-middle attack abbreviated in various ways: MITM, MitM, MiM, or MIM.
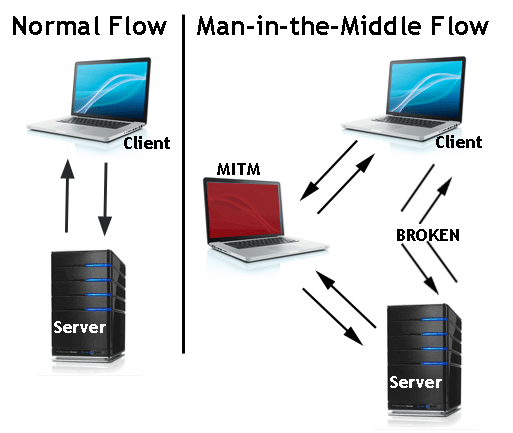
Image Source: veracode.com
Public Wi-Fi networks are most likely to be used during a man-in-the-middle attack because they usually are less secure than private Internet connections. Criminals get in the middle by compromising the Internet router, by scanning for unpatched flaws or other vulnerabilities. The next step is to intercept and decrypt the victim’s transmitted data using various techniques.
The most susceptible for a man-in-the-middle attack are the financial sites, other sites that require a login and any connection meant to be secured by a public or private key.
How Does a Man-in-the-Middle Attack Work?
As mentioned above, during a man-in-the-middle attack, a malicious player inserts himself between two parties and gains access to the information that the two parties were trying to share.
Usually, a man-in-the-middle attack has two phases:
Interception
To gain access to a network, attackers usually use open or not properly secured Wi-Fi routers. They can also manipulate DNS servers. Their goal is to find weak passwords, but they may also take advantage of IP spoofing or cache poisoning. Once they get access, the victim’s data will be collected by deploying data capture tools.
Decryption
During this phase, the intercepted data is decoded and ready to be used for the infelicitous purposes of the cybercriminals, which can vary from identity theft to plain disruption of business operations.
Man-in-the-Middle Attack Types
A man-in-the-middle attack can come in many shapes, yet the most common are the following:
1. IP spoofing
The Internet Protocol Address (IP) refers to a numerical label that is assigned to each device that connects to a computer network that uses the Internet Protocol for communication. IP addresses have two main functions: host or network interface identification and location addressing. By spoofing an IT address, attackers make you think that you’re interacting with a reliable website or entity, which allows them to access the information you’d otherwise keep for yourself.
2. HTTPS spoofing
The HyperText Transfer Protocol (HTTP) represents the foundation of data communication for the World Wide Web, hypertext documents including hyperlinks to other resources that users can access. HTTPS means that a particular website is secure and can be trusted, but attackers can still find ways to convince your browser that a website is safe, even if it’s not.
3. DNS Spoofing
The Domain Name System (DNS) is a hierarchical and decentralized naming system for computers, services, or other resources that are connected to the Internet, which translates more readily memorized domain names to the numerical IP addresses needed for localization and identification. By DNS spoofing, an attacker will redirect traffic to a fake website, in an attempt to pick up your credentials.
4. SSL hijacking
SSL stands for Secure Sockets Layers and is a type of protocol that enacts encrypted links between your browser and the webserver. When you connect to a secure server (guaranteed by HTTPS), you expect standard security protocols to be in place, protecting whatever data is shared between it and your devices. When someone hijacks SSL, the information shared between the victim’s device and the server is intercepted by another endpoint and another secure server.
5. E-mail hijacking
E-mail hijacking is a type of man-in-the-middle attack used by cybercriminals to target banks’ email accounts or other financial institutions. After they obtain access, all the transactions between an institution and its clients can be supervised. What’s even more dangerous – the clients will follow the attackers’ instructions while thinking they are performing regular banking operations.
6. Browser cookies theft
In technical language, cookies refer to small pieces of information – like the items you add in the cart of an online store or your address information – that websites save on your devices. By stealing cookies from your browsing sessions, cybercriminals can obtain passwords and various other types of exclusive data.
7. Wi-Fi eavesdropping
This type of man-in-the-middle attack is particularly dangerous: hackers can set up Wi-Fi connections that sound legitimate, almost just like the ones you probably already know. If users connect to them, they can literally say farewell to their online privacy: their whole online activity (including login credentials and payment card information) will be at the command of the cybercriminals.
Famous Man-in-the-Middle Examples
a. The Marconi Case
The first recorded man-in-the-middle attack in history took place long before the Internet was even invented and it involves Guglielmo Marconi, a Nobel prize winner considered to be the inventor of the radio. What happened? When a legal advisor to Marconi, Professor Fleming, was making a demonstration of wireless transmission from one location to another, a Mr. Maskelyne, with his own receiver, intercepted the message that was supposed to be sent from Cornwall to the Royal Institute and then transmitted his own message.
b. World War II Interceptions
Several years after the Marconi case, during World War II, man-in-the-middle attacks orchestrated by the British intelligence targeted the Nazi forces. Aspidistra (a British medium wave radio transmitter) operators used to transmit fake messages to German listeners, with the intent of demoralizing them.
Even the Enigma decoding can be considered a case of man-in-the-middle.
c. The Lenovo Incident
Closer to our times, since December 2014, Lenovo endpoints had pre-installed software called Superfish Visual Search on them that facilitated the placements of advertisement even on encrypted pages. The software could be removed by Windows Defender thanks to an update released by Microsoft in February 2015.
A man-in-the-middle attack is dangerous. End users can carry on with their business for days or even weeks without noticing that something is wrong. Consequently, it’s almost impossible to know, during that time, what data was exposed to malicious actors. Finding out more about what happened often requires good knowledge of the internet or mobile communication protocol and security practices. Fortunately, there are some security measures you can take in order to be safe.
How to Prevent a Man-in-the-Middle Attack
1. Use a VPN
A Virtual Private Network (VPN) is used to extend a private network across a public one, enabling users to share and receive data as if their devices were directly connected to that private network. Particularly useful when talking about preventing a man-in-the-middle attack is that VPN connections can mask your IP address by bouncing it through a private server. Plus, they can encrypt the data as it’s transmitted over the Internet.
2. Access only HTTPS websites
HTTPS websites prevent attackers from intercepting communications by encrypting data.
An excellent method to go around HTTPS spoofing is by manually typing the web address you need instead of relying on links.
You can also check if the link you want to access begins with ‘https://’ or has a lock symbol, suggesting it’s secure.
3. Watch out for phishing scams
There are lots of tips that we can give you when regarding phishing precautions.
– check grammar and punctuation. Suspicious e-mails might include poor grammar or punctuation or might show an illogical flow of content.
– remember that established banks never ask you for sensitive information via e-mail. You should consider as big red flags any e-mails that ask you to enter or verify personal details or bank/credit card information.
– pay special attention to alarming e-mail content and messages where you are told that one of your accounts has been hacked, that your account has expired or other extreme issues that may provoke panic. Do not take immediate action!
– don’t fall for urgent deadlines either. This kind of e-mails usually leads the users to data harvesting websites, where sensitive personal or financial information is stolen.
– beware of shortened links. They don’t show the real name of a website, so they are a perfect way to trick users into clicking. Get used to always place your cursor on shortened links to see the target location.
If you want to learn more, check https://www.phishprotection.com/content/phishing-prevention/ .
4. Use strong router credentials
Make sure that not only your Wi-Fi password but also router credentials are changed. If these credentials are found by an attacker, they can be used to change your DNS servers to their malicious ones or to infect your router with malware.
5. Make sure your company has a software update policy
A software update policy helps you seal potential access points for a man-in-the-middle attack because up-to-date systems include all current security patches for known issues. The same should be considered for any routers or IoT devices connected to your network.
Heimdal® Patch & Asset Management Software
6. Adopt a zero-trust security model
Although it might seem a little too much, requiring your colleagues to authenticate themselves each time they connect to your network regardless of where they are will make it more difficult for hackers to pretend to be someone else. They would need to prove their identity before accessing the network in the first place.
7. Prevent cookie stealing
Saving passwords on web browsers or storing credit card information on shopping websites might save you a bit of time, but it also leaves you more vulnerable to hackers. You should try to avoid storing sensitive information on websites and also get used to clear your cookies regularly. If you use Chrome, you can do this by accessing History > Clear Browsing History and ticking the checkbox “Cookies and other site data”.
Heimdal ™ Security can also help. Here’s how!
As we have already seen, a man-in-the-middle attack can take various forms: IP, HTTPS or DNS Spoofing, SSL or e-mail hijacking, browser cookie theft, or Wi-Fi eavesdropping.
Some of the Heimdal™ solutions are perfect for protecting your business from them:
Heimdal Threat Prevention offers DNS and DoH security, plus a powerful and scalable Automated Patch Management system. Its Dark Layer Guard™ mitigates ransomware, next-gen attacks, and data leakage. Its Vector Detection™ tracks device to infrastructure communication and its XPloit Resilience feature closes vulnerabilities and deploys updates anywhere in the world.
For paramount protection, you can combine it with Heimdal Next-gen Endpoint Antivirus, our antivirus solution with unparalleled threat intelligence, EDR, forensics, and firewall integration.
When it comes to email security, Heimdal™ Email Security can help you detect malware, and stop spam, malicious URLs, and phishing with simple integration and highly customizable control. If you want to take one step further, Heimdal™ Fraud Prevention will make sure that no e-mails containing fraud attempts, business e-mail compromise, or impersonation reach your inbox.
Wrapping Up
When trying to prevent a man-in-the-middle attack, there are three major aspects you must consider:
– awareness & education. People are the ones who unknowingly click on bad links or use their login data on a compromised website, allowing hackers access to their information, so making sure that your colleagues and employees know the basic principles of preventing MITM attacks is essential.
– encryption & VPNs. Use encryption on all of your company’s devices and use VPNs whenever you connect to public networks, for extra protection.
– software update policy. Make sure that all your systems are up-to-date. Even a single point of failure can put your entire network in danger.
Also, please remember that Heimdal™ Security always has your back and that our team is here to help you protect your company and your home against cyber threats and to create a cybersecurity culture to the benefit of anyone who wants to learn more about it.










 Network Security
Network Security
 Vulnerability Management
Vulnerability Management
 Privileged Access Management
Privileged Access Management  Endpoint Security
Endpoint Security
 Threat Hunting
Threat Hunting
 Unified Endpoint Management
Unified Endpoint Management
 Email & Collaboration Security
Email & Collaboration Security