Contents:
The number of attacks targeting banks grew after the source code for CypherRat, a new SpyNote malware version, was offered for free on hacker groups.
CypherRat has both spyware and banking trojan features impersonating banking institutions. It was initially sold by its developer on Telegram, to more than 80 threat actors. Eventually, it was leaked on hacker forums by other threat actors and the developer decided to make its source code public.
CypherRat was sold via private Telegram channels from August 2021 until October 2022, when its author decided to publish its source code on GitHub, following a string of scamming incidents on hacking forums that impersonated the project.
Cyber researchers claim the number of SpyNote Android malware infections rapidly grew once various malicious actors snatched the source code and started launching their own campaigns. Even big brands, like HSBC and Deutsche Bank, were impersonated, as a result.
What Makes the New SpyNote Malware Version Special?
As with other banking malware, at first, SpyNote requests permission to access Android’s Accessibility Service, so that it will be able to get the two-factor authentication codes, record keystrokes so it can steal banking user and password, and take screenshots of your phone.
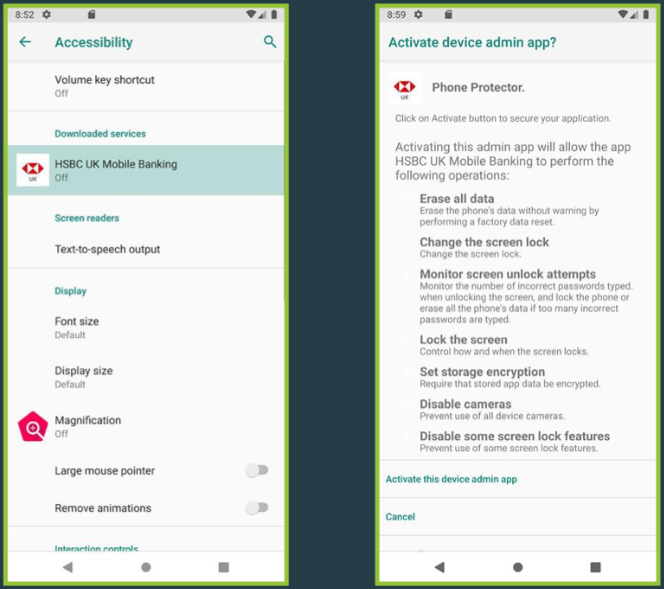
This new spyware comes with lots of distinct features and is able to get your SMS messages, spy your calls, track GPS locations, and take video and audio recordings. Also, in order to avoid detection, it uses string obfuscation and commercial packers to hide the APKs.
Although threat actors seem to prefer to focus on CypherRat`s banking trojan capabilities, this malware could also be successfully used in espionage operations.
Recommended Security Measures for Android Users
Cyber researchers did not yet reveal how the spyware is spread, but as always, phishing sites, third-party Android app sites, and social media are the likely answers to the problem.
Make sure you keep your mobile and banking data safe and avoid installing new apps from outside Google Play. Even so, be always on guard and refuse any application`s request to access the Accessibility Service. Although Google keeps working on making the Accessibility Service API safer, threat actors also keep finding ways to work around any new restrictions.
If you liked this article, follow us on LinkedIn, Twitter, Facebook, Youtube, and Instagram for more cybersecurity news and topics.


 Network Security
Network Security
 Vulnerability Management
Vulnerability Management
 Privileged Access Management
Privileged Access Management
 Endpoint Security
Endpoint Security
 Threat Hunting
Threat Hunting
 Unified Endpoint Management
Unified Endpoint Management
 Email & Collaboration Security
Email & Collaboration Security









