Contents:
Researchers discovered new version of the Vultur Android banking trojan upgraded its obfuscation and remote control features.
Reportedly, the malware masquerades the McAfee Security app to trick the victim into installing it.
The Vultur banking trojan infection chain explained
The first step of the attack is sending the victim a phishing SMS warning about an authorized transaction. The hackers pressure the target to call a given number for help.
Next, the threat actors get the victim to click a malicious link in another SMS.
The victim lands on a fake McAfee Security app download page. Downloading the forged security app leads to installing the “Brunhilda” malware dropper.
The dropper runs three Vultur payloads (APKs and a DEX file). From then on, the malware can
- access the Accessibility Services
- use remote control features
- connect to the Command-and-control server
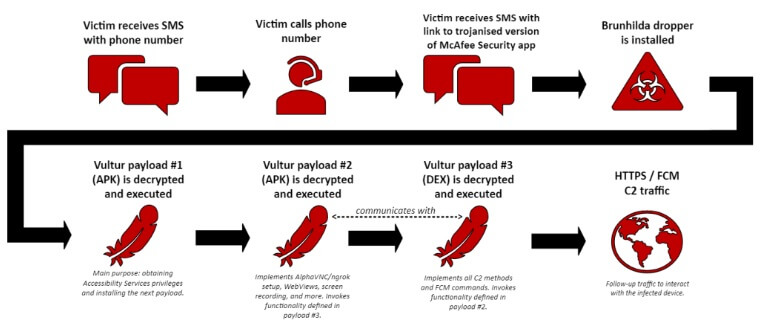
Source: Fox-IT
What are Vultur’s new technical features?
Researchers say the Android banking trojan uses AES and Base64 encryption to stealthily communicate with its C2. Besides, the new Vultur malware can:
- Deploy, install and delete files
- Command the victim’s device to scroll, swipe, click, mute/unmute audio, etc. For this, it uses the Android Accessibility Services
- Block apps
- Show a custom notification in the status bar
- Evade lock screen security measures by disabling Keyguard
How to prevent a Vultur malware infection
Avoid falling victim to the new Vultur banking trojan by following a few cybersecurity best practices:
- Always download apps from Android’s official app store, Google Play
- Beware of social engineering and smishing techniques
- Don’t click on URLs in messages. Use a DNS filtering solution to block communication to and from malicious domains.
- When installing a new app, only allow those permissions that it needs to work properly. Block access to any other functionality, like accessing the camera or microphone
If you liked this article, follow us on LinkedIn, Twitter, Facebook, and Youtube, for more cybersecurity news and topics.


 Network Security
Network Security
 Vulnerability Management
Vulnerability Management
 Privileged Access Management
Privileged Access Management
 Endpoint Security
Endpoint Security
 Threat Hunting
Threat Hunting
 Unified Endpoint Management
Unified Endpoint Management
 Email & Collaboration Security
Email & Collaboration Security









