Contents:
User access review software is essential for ensuring secure and compliant access management in any organization.
This article provides you with a comprehensive overview of the 10 best user access review software of 2025 to help you make your decision easier.
The Importance of Choosing the Right User Access Review Solution
The right user access review (UAR) solution will safeguard your organization, while the wrong one will break it.
The big danger of not having proper identity management is the potential for errors, leading to security breaches.
Mikkel P, Head of Global Sales Enablement, Heimdal®
Here’s how choosing the right solution helps your company:
Security Enhancements:
- Identifies and promptly revokes unnecessary access.
- Enables proactive security against security breaches.
Risk Mitigation:
- Reduces the cybersecurity risks associated with privilege concerns.
- Regularly modifies access rights to limit the risk of data breaches and insider threats.
Compliance Assurance:
- Streamlines security compliance with industry standards (e.g., HIPAA, ISO 27001).
- Demonstrates compliance with regulations while avoiding legal penalties.
Enhanced Efficiency:
- Streamlines access reviews, decreasing the workload of IT professionals.
- Provides suitable access levels quickly, optimizing resource utilization.
Continuous Monitoring:
- Supports constant monitoring to ensure that access rights are aligned with organizational changes.
- Identifies and addresses policy deviations promptly.
How to Choose the Right User Access Review Solution for Your Business
Now that you know the importance of choosing the right UAR software, you’d want to know how to choose one as well. So, here’s a step-by–step guide for you:
Define Requirements
Start by clearly outlining your organization’s requirements.
Research Compliance Standards
Understand the compliance standards that apply to your industry, such as PCI DSS, HIPAA, or SOX. Ensure that the UAR software adheres to these criteria.
Evaluate Integration Needs
Assess your present identity and access management, authentication, and authorization solutions. To improve procedures and reduce disruptions, use UAR software that integrates seamlessly with these platforms.
Assess Scalability
Consider the software’s scalability. Determine whether it can support your organization’s expansion in terms of authorized users, applications, and sensitive data.
Evaluate the User Interface
Test the UAR software’s user interface. A user-friendly interface is critical for improving your IT team’s efficiency and increasing user engagement in the access review process.
Check the Automation Capability
Investigate the automation aspects of the software. Look for capabilities that can automate workflows, lowering manual errors, saving time, and increasing accuracy.
Check for RBAC Support
Ensure that UAR software supports Role-Based Access Control. This feature simplifies access control and ensures proper segregation of duties.
Do an Audit Trail and Reporting Assessment
Assess the audit trail and reporting features. The tool should keep a complete record of changes, access decisions, and compliance reports.
Check Risk Assessment and Analytics
Look for UAR software that includes risk assessments and analytics features. These features aid in detecting high-risk access scenarios, prioritizing reviews, and improving overall security.
Review Customization Options
Analyze the customization options available. Choose software that allows you to customize workflows, review criteria, and reports to meet your organization’s specific requirements.
Check Security Measures
Investigate the software’s security procedures, which include encryption, multi-factor authentication, and other security standards. Ensure that the software meets your company’s security standards.
Do Vendor Support and Reputation Analysis
Research the software vendor’s reputation. Read reviews and testimonials to determine their track record. Also, assess the degree of support and training given by the vendor.
Consider Costs
Understand the pricing structure of the UAR software. Consider license fees, installation costs, and ongoing maintenance expenses. Make sure the charges are within your budget, and clarify any potential hidden fees.
Having an identity management tool automates the process, preventing manual errors and reducing the risk of security breaches.
Mikkel P, Head of Global Sales Enablement, Heimdal®
To give you a concise view of what’s an absolute requirement in terms of UAR software, here is an overview of the key features it must have:
Centralized User Access Control:
User access review solutions provide a unified dashboard with detailed information about user access privileges across various systems, apps, and resources.
Automated Access Review Management:
Streamline and schedule regular access reviews, specify parameters, and automate stakeholder notifications to reduce workload and increase monitoring efficiency.
Simplified Role-Based Access Controls (RBAC):
With RBAC, you can easily implement and monitor access privileges, ensuring the right users have the right access privileges while reducing the risk of data breaches.
Enhanced Segregation of Duties (SoD) Compliance:
Support adherence to SoD policies by identifying conflicting access privileges and limiting security risks associated with unauthorized activities.
Robust Audit Trail and Compliance Reporting:
Empower IT teams with user access review solutions that capture comprehensive activity logs and user access changes, making it easy to generate detailed compliance reports for audits.
The Top 10 User Access Review Software
Since there are various options available in the market, choosing the right UAR software can be overwhelming. Here’s a list of top products in the industry today, along with a comprehensive overview to understand which one fits your business.
Heimdal®
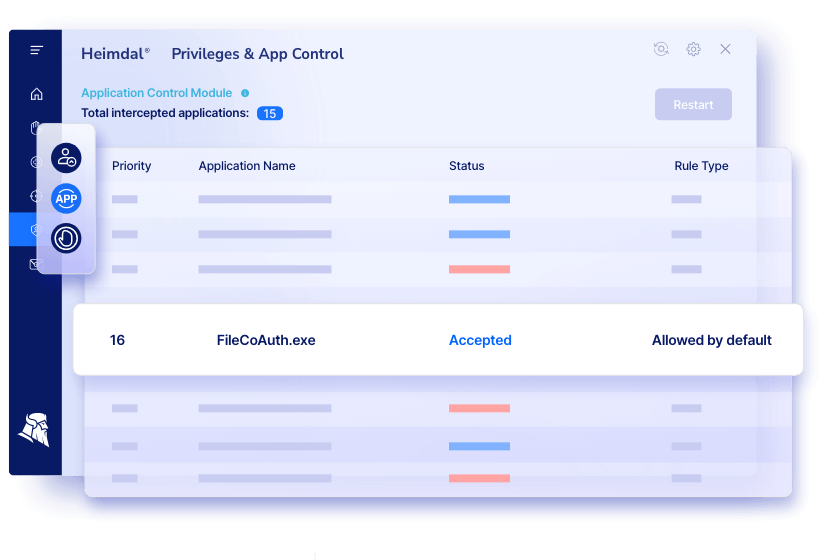
If your organization needs a solution that exceeds the covering of your regular user access review software, Heimdal®’s Privilege Elevation and Delegation Management & Application Control solution could be right for you.
It is the world’s only bundled product that combines both functionalities.
The line-up proactively secures your entire environment, ensuring compliance with the most common industry standards such as NIST, HIPAA, PCI-DSS, and many more.
Moreover, it helps in boosting the productivity of users and admins while being completely transparent.
Heimdal® Top Features
- It allows or blocks requests for escalations in just one click;
- Easy to enable Auto-approval flow with defined rules and automatic de-escalation on threat;
- Admins can define and control rule-based systems;
- Define individual rights per AD group;
- RBAC support;
- Allow or block the execution of apps based on File Path, MD5, Publisher, Certificate, or Software Name criteria;
- See what apps users have executed in Passive, Allowed, or Blocked mode.
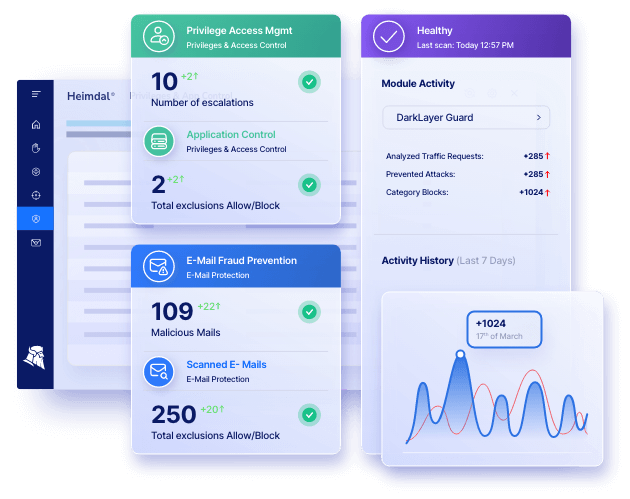
The user access review software in the Privileges and Application Control line-up secures effectively all three major areas of your IT access infrastructure: management of privileges, application control, and auditing, ensuring everything works smoothly and threats are kept away.
Heimdal® Pros
- Heimdal®’s solution is infinitely customizable. You can set filters, create white and blacklists, engage passive mode as defined by admins, and more;
- Easy implementation and configuration;
- User-friendly interface;
- Heimdal® offers full, granular audit trails to assist you in cybersecurity standard compliance;
- Heimdal® lets you expand your suite with cross-functional modules, that you can control all in a single interface and dashboard.
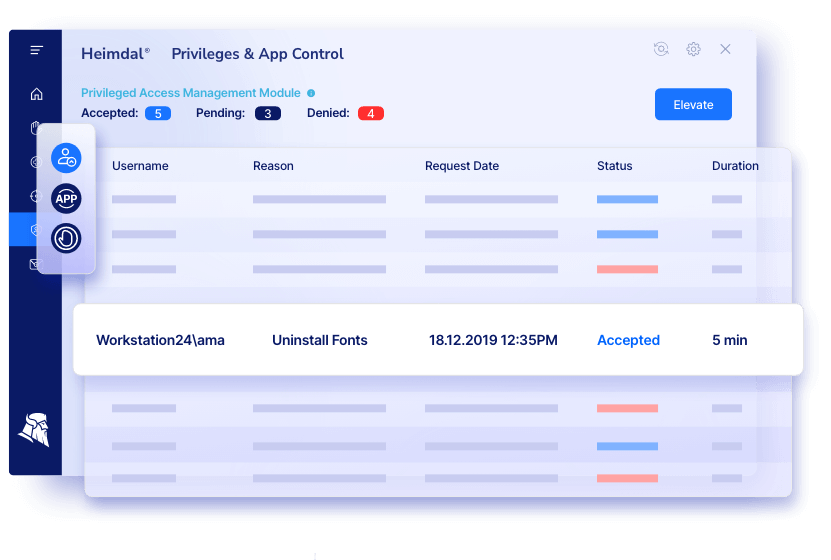
Heimdal®’s Privileged Access Management supports PEDM-type non-privileged user account curation features for AD (Active Directory), Azure AD, or hybrid setups.
Under PEDM, the PAM solution allows for the retention of administrative permissions for specific users and/or domain groups that can be traced back to specific endpoints or groups. Its TIL (Time-to-Live) feature acts as JIT (Just-in-Time).
Heimdal® Cons
As a con, Heimdal®’s solution is not able to send real-time alerts in case of anomalies for user activities. Instead, every request will be reviewed case-by-case and approved or not by the admins.
Heimdal® Pricing
Book a demo with Heimdal® experts and take the solution for a spin! Then receive an offer tailored specifically on your organization’s needs.
SecurEnds
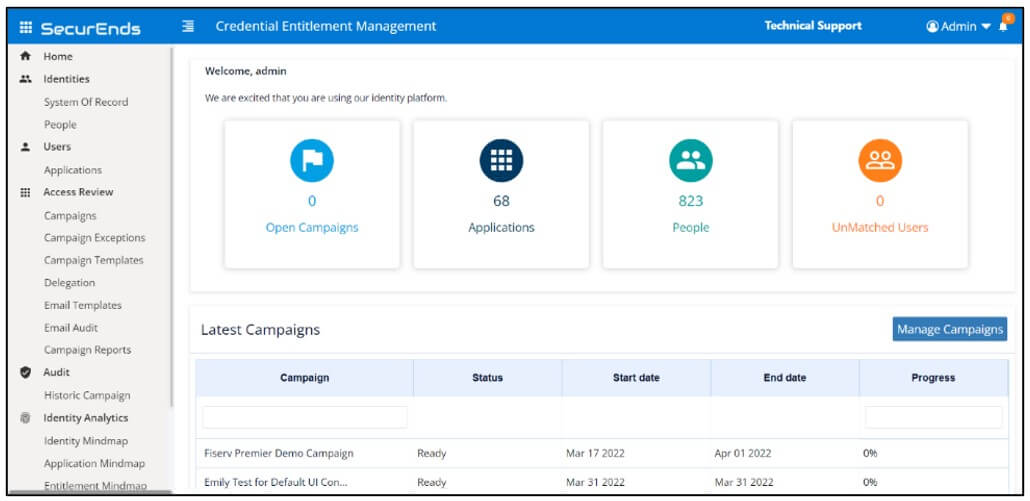
SecurEnds streamlines thorough user access reviews by offering a centralized platform for automating access rights assessments across organizational systems. The software provides granular access analysis, detects excessive privileges and dormant accounts, and improves security by minimizing unauthorized activities.
Top Features
Here are the top features of SecurEnds:
Automated Notification and Remediation:
- Immediate alerts for important access-related events.
- Quick remediation capabilities for modifying or revoking user access rights.
Regulatory Compliance and Audit Support:
- Creates detailed reports for user access reviews and activities.
- Simplifies audit processes and facilitates compliance needs to help stay compliant.
Customizable dashboards:
- Create metrics and visuals that are tailored to the specific needs of the IT professional.
- A clear picture of access review progress, metrics, and compliance status.
Pros
- Automated user access reviews improve compliance and reduce security concerns.
- Built-in interfaces for various applications enable rapid implementation.
- Flexible options, including on-premises and SAAS versions, as well as mobile access.
Cons
- The user interface is not intuitive.
- Alerting systems are not advanced enough.
- Doesn’t offer enough integrations.
Pricing
The pricing is not public, nor do they offer a free trial. You need to book a demo to get the pricing information.
Zluri
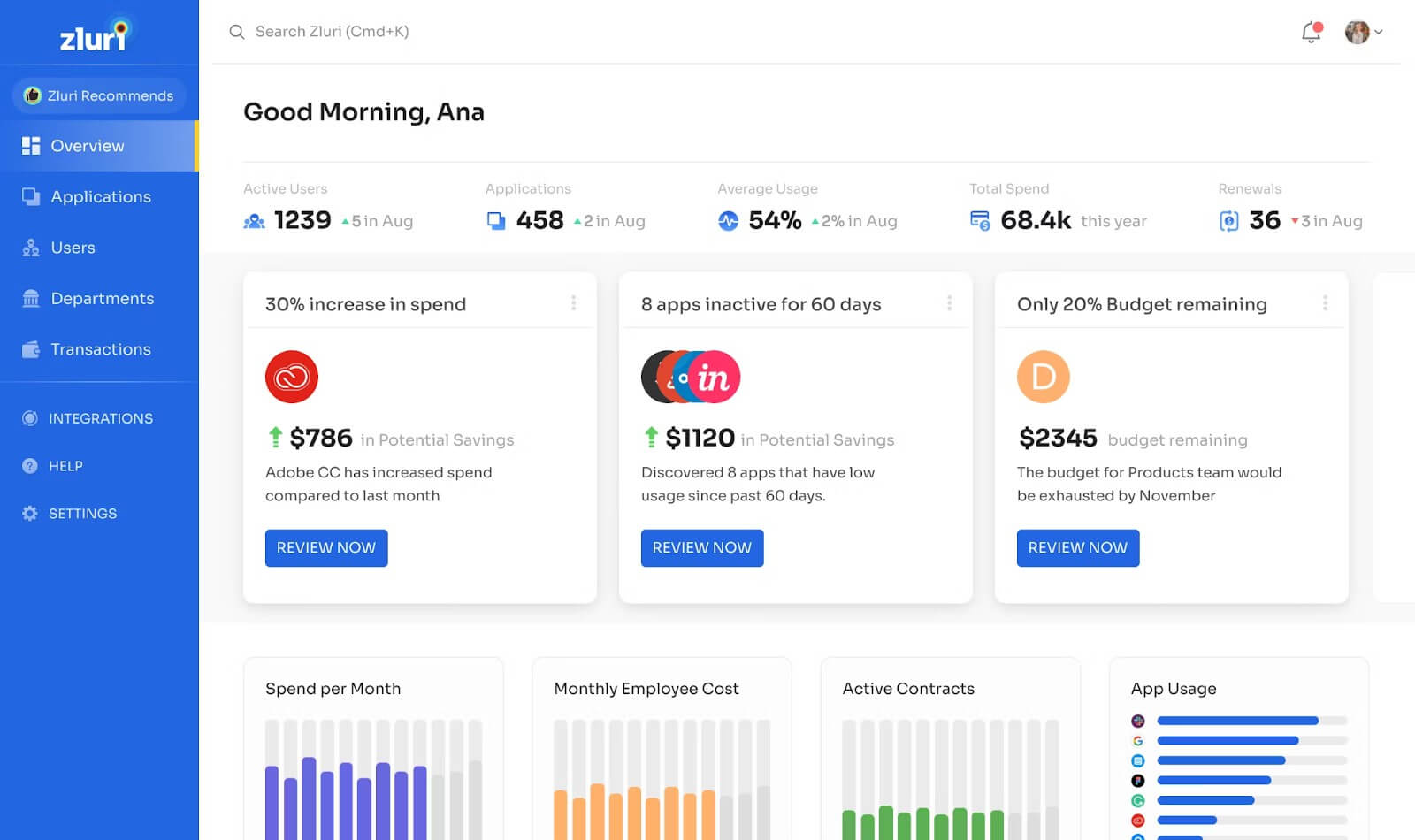
Zluri’s Identity Governance and Administration (IGA) solution prioritizes security and compliance by efficiently managing access rights. The tool simplifies IT audits, ensures regulatory compliance, and provides effective user access control.
Top Features
The top features of Zluri include:
SaaS Application Discovery:
- Utilizes five discovery strategies to distinguish between active and inactive SaaS applications.
- Provides deep insight for IT professionals to review and manage access.
Automated Access Management:
- Makes it easier to provide and revoke employee access rights.
- Customizable processes and scheduled tasks for future provisioning and de-provisioning.
Role-Based Access Control:
- Allows authorized users to access only the applications they need based on their job roles.
- Continuously monitor and update users and devices.
Proactive Auditing:
- Regular audits to identify apps and users who require special attention.
- Enables essential security measures to prevent unwanted user permissions, ensuring that sensitive information is only accessed by authorized individuals.
Pros
- Detailed reporting and an easy-to-use interface improve the overall experience.
- Zluri provides complete visibility into the SaaS stack, yielding useful insights.
Cons
- An issue with broken links on the task completions.
- The time required to set it up can be quite extensive.
- Less affordable for small businesses or organizations with limited IT budgets.
Pricing
Zluri offers tailor-made pricing plans — you need to contact the sales team.
LogicManager
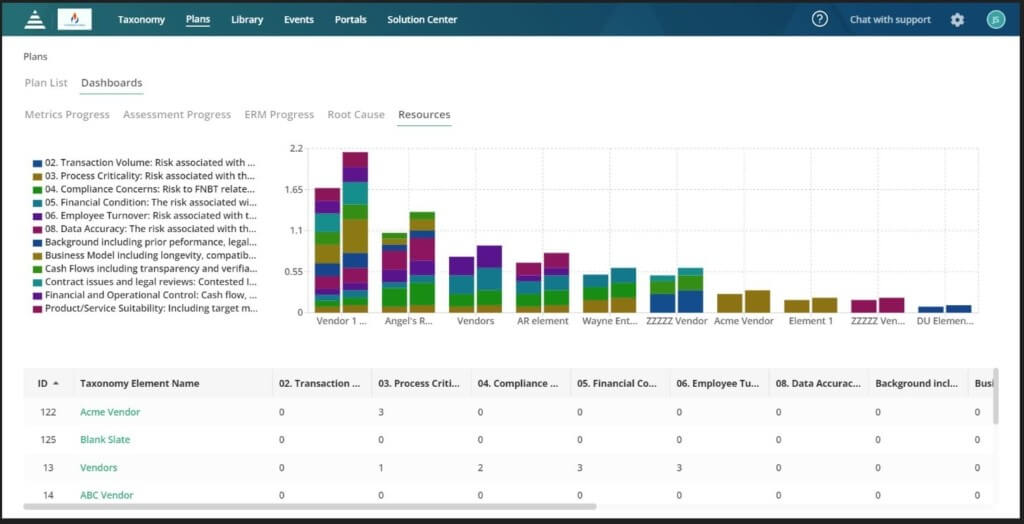
LogicManager is a comprehensive user access review solution that simplifies the management of user privileges through a centralized dashboard. This tool provides rapid assessment of potential security risks and immediate mitigation action, eventually enhancing compliance and lowering the risk of unauthorized access.
Top Features
LogicManager has got some great features, such as:
Fine-Grained Access Control:
- Role-based controls provide exact privilege allocation.
- Access permissions are customizable to improve task efficiency and data security.
Insight and Compliance Tracking:
- Reports highlight issues such as excessive privileges and inactive accounts.
- The audit trail promotes transparency and regulatory compliance.
Smooth Integration and Scalability:
- Seamless integration reduces disruptions.
- Scalability is suitable for businesses of all sizes.
Pros
- Offers centralized location for all vendor processes and documents.
- Provides great customer support.
Cons
- Doesn’t offer self-service resources.
- It offers only 3 levels for risk and controls, which makes it more difficult to get more granular.
Pricing
It offers custom pricing, and for that, you need to request a quote by filling out a form through its website.
ConductorOne Access Review
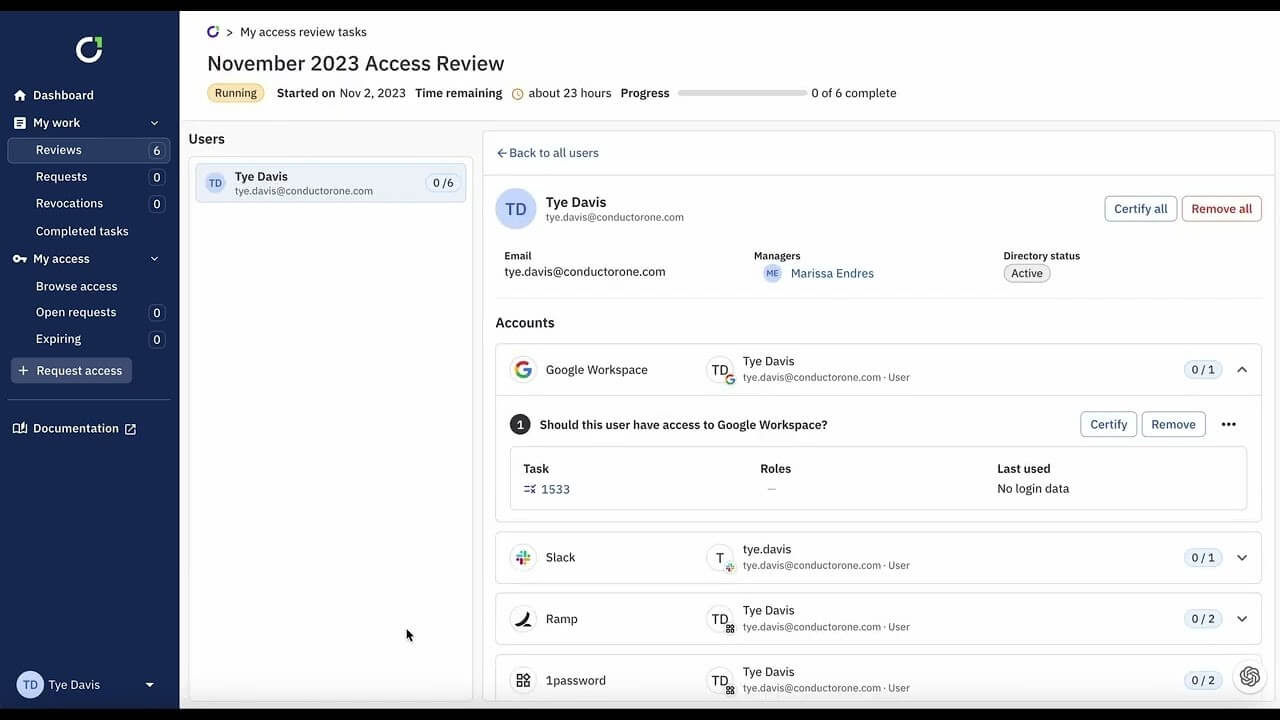
ConductorOne streamlines the user access review process by providing a sophisticated platform for efficient access control, enhanced security, and compliance fulfillment.
It saves time by systematically identifying access privileges via an automated approach. The platform centralizes access permissions and integrates easily with existing systems to provide a unified view, resulting in a streamlined and integrated management structure.
Top Features
It has some great features that include:
RBAC (Role-Based Access Control):
- Incorporates RBAC capabilities for defining roles and access rights based on responsibilities and hierarchy.
Offers User-Friendly Interface:
- Simplifies navigation using an easy-to-use interface.
- Allows for convenient access, review, and informed decision-making regarding user access rights.
Comprehensive auditing and compliance reporting:
- Offers comprehensive auditing and reporting capabilities.
- Creates detailed reports that capture access review activities, changes, and approvals and serve as crucial evidence during audits.
Pros
- Provides a streamlined and intuitive user interface.
- Provides various integrations and also adds up new ones at customers’ requests.
Cons
- Simplicity in earlier versions, particularly in attribute creation, has become more challenging.
- The vendor’s documentation is unclear, which might hinder effective utilization.
- Users report performance issues that affect the tool’s efficiency and responsiveness.
Pricing
It offers a 14-day free trial and custom pricing — for that, you need to request a quote.
Rippling
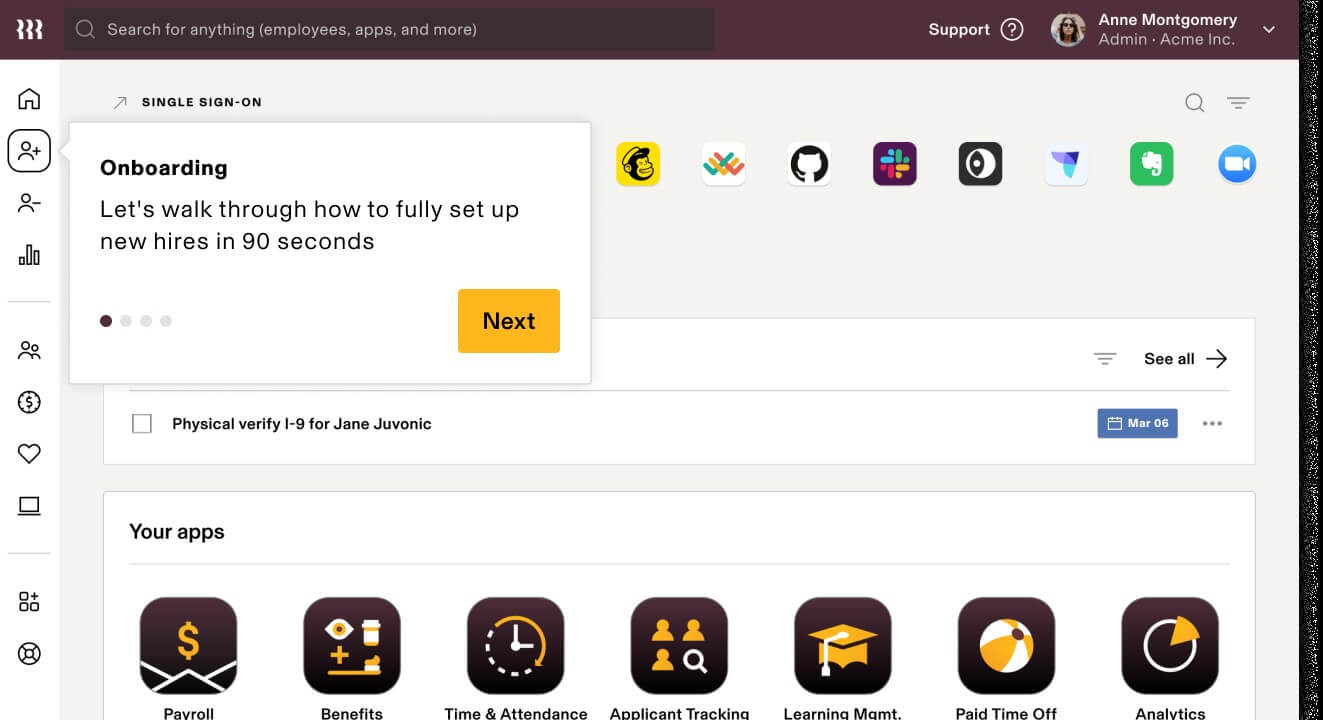
Rippling’s Access Control Report allows users to monitor and report on employees’ service access and permissions, as well as details on administrative access inside an organization.
To restrict employees’ access to important data, the platform uses role-based permissions across Rippling and third-party applications. Furthermore, Rippling provides a unified location for configuring, managing, and disabling employee apps and services.
Top Features
Access Control Report:
- Users may quickly examine and generate reports about employees’ service access and associated permissions.
- Detailed information is supplied about admin access, including who in the organization has administrative privileges for specific services.
Role-based permissions:
- Rippling uses role-based permissions for its platform and third-party applications.
- This ensures that employees have personalized access, restricting their interactions to data and functionalities relevant to their roles.
Unified Management Hub:
- Rippling provides a unified platform for easily setting up, managing, and disabling employee apps.
- This single hub simplifies the review process of managing user access across several services.
Pros
- Modern user experience and interface design.
- Easy to navigate from an admin standpoint.
- Makes onboarding and offboarding easy and intuitive.
Cons
- Integration and contractual issues.
- Poor customer service upon cancelling.
- Complicated reporting and employee profile difficulties.
Pricing
Rippling starts at $8 a month per user. However, you need to request a custom quote based on your requirements.
ManageEngine ADAudit Plus
ManageEngine ADAudit Plus improves user access controls by providing a streamlined solution that makes access management easier and more secure. The unified dashboard displays user accounts, related permissions, and access history, making it easier to detect and mitigate unwanted access for increased security and compliance.
Furthermore, the solution automates the review cycle, removing human processes and increasing overall productivity.
ManageEngine ADAudit Plus Top Features
Its top features include:
Granular User Access Controls:
- Define role-based access controls to ensure exact permission distribution based on job responsibilities.
Real-Time Anomaly Detection:
- Continuously monitor user actions for any questionable conduct.
- Set up notifications for illegal access attempts or odd data transfers, allowing you to respond quickly to any security incidents.
Comprehensive Compliance and Audit Reports:
- Provide detailed reports as concrete proof of effective user access controls during audits.
- Transparent reporting helps to ensure compliance and establish stakeholder trust.
Pros
- Provides alerts for anomalies and unexpected events.
- Provides valuable reporting features for specific scenarios and custom report generation.
- Intuitive UI and simple implementation help to provide a favorable user experience.
Cons
- Some features may feel clunky.
- Configuring custom alerts, especially for complex situations, can be challenging.
- Integration with other ManageEngine solutions, such as Log360 Suite, is confusing.
Pricing
ManageEngine’s pricing starts at US$595 for 2 domain controllers and goes up to US$29,995 for 200 domain controllers.
Cypago
Cypago’s user access review solution improves control over user access management by providing a consolidated platform that allows for the monitoring of user access privileges across multiple systems and apps via a single dashboard. This simplified method reduces the need to navigate several interfaces, providing rapid, thorough user access reviews.
Top Features
The key features of Cypago includes the following:
Automated Access Review Management:
- Regular reviews can be easily scheduled and conducted.
- Customizable cycles and automated notifications for ongoing review.
Precise Role-Based Access Controls (RBAC):
- Robust functionality for accurately defining roles and permissions.
- Users are assigned to predetermined roles in order to simplify access reviews.
Auditing and Compliance Tracking:
- Strong auditing capabilities for tracking and documenting access review activities.
- Simple report production to demonstrate compliance during internal and external audits.
Pros
- Provides templates to write policies.
- The integration to cloud and CI/CID systems is smooth.
Cons
- Doesn’t provide enough integrations.
- Some of the controls are semi-automated and require some manual work from the tech side.
Pricing
Cypago offers custom pricing, and for that, you need to request a quote from their sales team.
Zilla Security
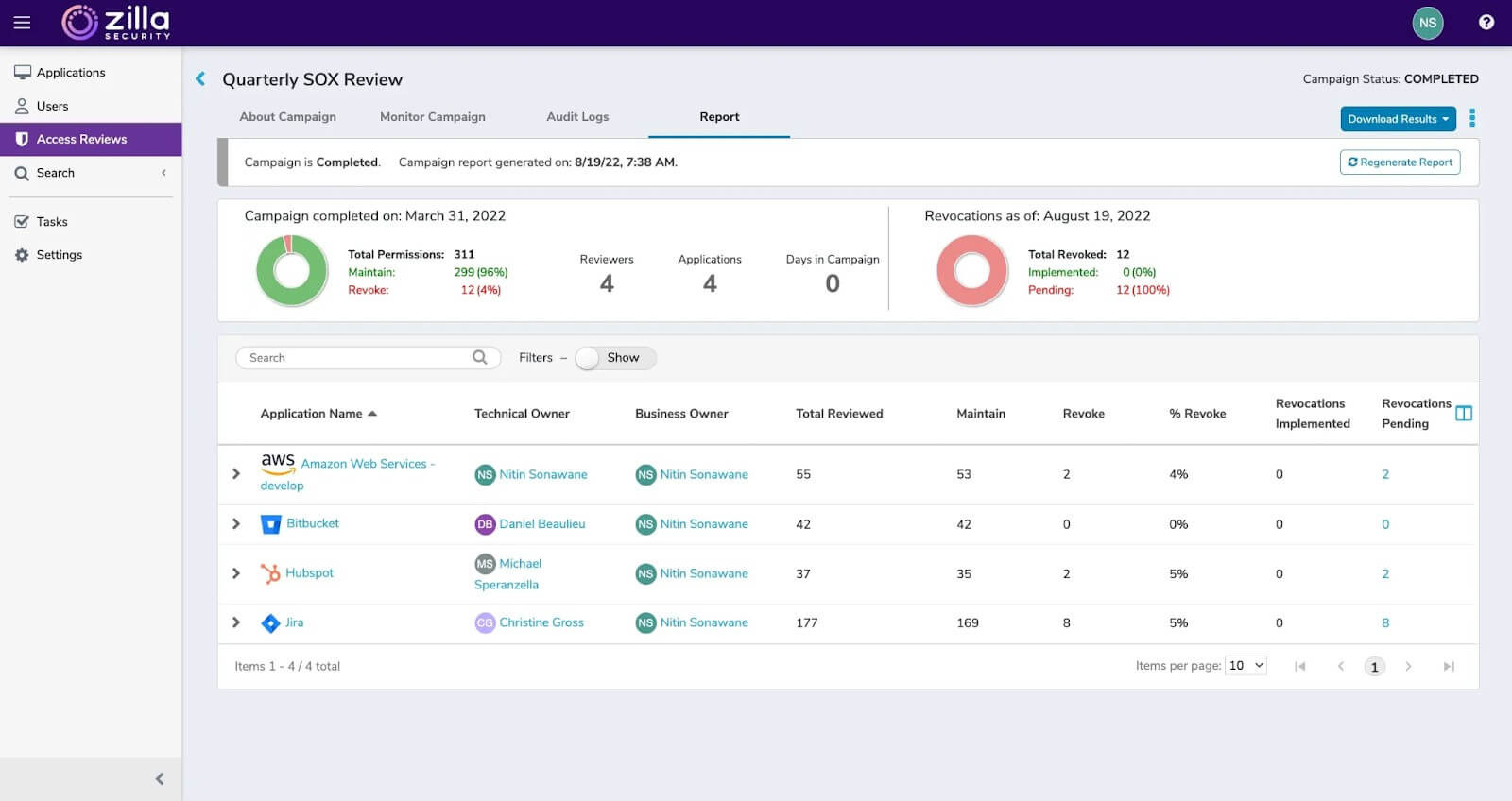
Zilla Security provides a user access review solution that automates and streamlines the review workflow, allowing for the efficient assessment and validation of user permissions across various systems and applications.
The platform has a centralized dashboard with a comprehensive view of user access, allowing for immediate identification of inconsistencies and potential security concerns for proactive mitigation, which is critical for maintaining a strong security posture.
Top Features
Here are the top features of Zilla Security:
Role-Based Access Control (RBAC):
- Integrates RBAC features for establishing and allocating access rights based on work responsibilities.
- Provides a scalable and consistent approach to ease access control.
Real-time Alerting System:
- Provides immediate alerts for crucial access-related events such as user access requests and authorization modifications.
- Ensures prompt responses to access-related incidents while maintaining organizational security.
Thorough Auditing and Compliance Reporting:
- Creates detailed reports that document access review actions, revisions, and approvals.
- Serves as valuable audit evidence, assisting in demonstrating compliance with regulatory standards.
Pros
- Rapid deployment, reliable support, and a responsive team.
- Rapid policy deployment for identifying “findings.”
- Easy integration with various apps.
Cons
- Dashboards and reporting are not intuitive.
- Difficulty identifying “movers” and privileged roles.
- Manual procedure for deactivating users during reviews.
Pricing
It offers a 30-day free trial and custom pricing; for that, you need to request a quote.
Threatlocker
ThreatLocker is a security platform that provides enterprise-level cybersecurity to enterprises worldwide. It prevents misuse and vulnerabilities in software, as well as controlling application elevation, storage, and network traffic.
Threatlocker Top Features
Some top features of ThreatLocker include:
Application Control:
- Whitelists only trusted programs and scripts while blocking the rest.
- Stops malware that evades traditional antivirus signatures.
Ringfencing™:
- Limits the actions that authorized applications can perform, even if compromised.
- Prevents attackers from using legitimate software for wider attacks.
Storage Control:
- Granular control over data access and copying rights.
- Protects sensitive information from unauthorized access or disclosure.
Elevation Control:
- Removes local admin access for users, improving overall security.
- Provides granular, on-demand elevation for specialized applications.
Operations:
- A cloud-based security monitoring and response system.
- Proactive threat detection and response capabilities.
Pros
- Effective in preventing unknown and known threats.
- Learning, installation, and elevation modes improve control and user experience.
- Easy to implement and use, suitable for diverse IT setups.
Cons
- Some issues were noted when utilizing Unified Audit, such as a need for saved filters.
- While it is available, the mobile interface should be improved further.
- Issues with limiting downloads from the Microsoft Store require fixing.
Pricing
Threatlocker offers a 30-day free trial and custom pricing for which you need to book a demo with their sales team.
Get the Right UAR Software for Your Organization
The whole foundation of identity management and privileged access management overall is to take away a user’s right to make any significant changes.
Mikkel P, Head of Global Sales Enablement, Heimdal®
That’s why you need to ensure the UAR software you choose — fits your organizational needs.
Choose a tool that:
- Aligns with your requirements
- Provides with the right automation, reporting, and integration capabilities
- Adheres to your industry’s compliances, and
- Offers great customer support.
FAQs
What happens during access review?
During an access review, a security officer synchronizes users’ access permissions with their current roles and limits individuals’ privileges to minimize the risks of data breaches such as privilege creep, misuse, and abuse.
How often should user access reviews be performed?
It depends on the size and personal requirements of your company. You can build a routine of weekly, monthly, quarterly, or annually, whichever suits you the best.
What is the risk of a lack of user access review?
The lack of user access review creates security vulnerabilities, raises the risk of data breaches, violates compliance requirements, allows insider threats, and wastes resources due to outdated or unnecessary access privileges.










 Network Security
Network Security
 Vulnerability Management
Vulnerability Management
 Privileged Access Management
Privileged Access Management  Endpoint Security
Endpoint Security
 Threat Hunting
Threat Hunting
 Unified Endpoint Management
Unified Endpoint Management
 Email & Collaboration Security
Email & Collaboration Security








