Contents:
Last month, the Ukrainian government announced the formation of a new Information Technology Army.
The initiative is made of volunteers from across the globe who will perform cyberattacks and distributed denial of service assaults against Russian targets.
This endeavor has sparked an outpouring of support from a large number of individuals all over the world who have been assisting in the targeting of Russian groups and sites, despite the fact that this conduct is deemed illegal.
What Happened?
Taking advantage of people’s eagerness to assist Ukraine’s cyberwarfare against Russia, a new malware campaign is attempting to infect them with password-stealing Trojans, according to the FBI.
Like many malware distributors, threat actors are taking advantage of the IT Army by marketing a bogus DDoS tool on Telegram that infects users with a password and an information-stealing Trojan that steals their credentials and information.
A new study from Cisco Talos warns that threat actors are imitating a distributed denial of service (DDoS) tool known as the “Liberator,” which is a website bomber designed for use against Russian propaganda websites.
The ongoing situation in Ukraine has quickly changed the cyber threat landscape, introducing an influx of actors of varying skill and a variety of new threats to Cisco customers and users globally. Many of these changes have been brought about by the rise in attacks being outsourced to sympathetic people on the internet, which brings about its own unique challenges and threats that Cisco Talos outlined in a recent blog.
In one of these new developments, we are seeing cybercriminals take advantage of the conflict by exploiting unwitting users seeking tools to carry out their own cyber attacks against Russian entities. A variety of these tools are advertised as ways to target Russian or pro-Russian websites and have quickly spread on various social media platforms over the last few days as the interest in crowdsourced attacks grows. A simple search for “Ukraine” or “Russia” on some popular open-source platforms returns a wide array of results. Most of the tools that have been released thus far are meant to disrupt various state-affiliated targets through distributed denial-of-service (DDoS) attacks. However, downloading any of these tools can be risky. In addition to the obvious potential legal implications of conducting a self-directed cyber attack, there is no way to know what other hidden features the tool may have or if it’s going to operate in its advertised fashion.
As BleepingComputer explained. while the versions downloaded from the official website are “clean,” and it is likely that they are illegal to use, the versions circulated in Telegram contain malware payloads, and there is no way to tell the difference before executing them because neither is digitally signed before being executed.
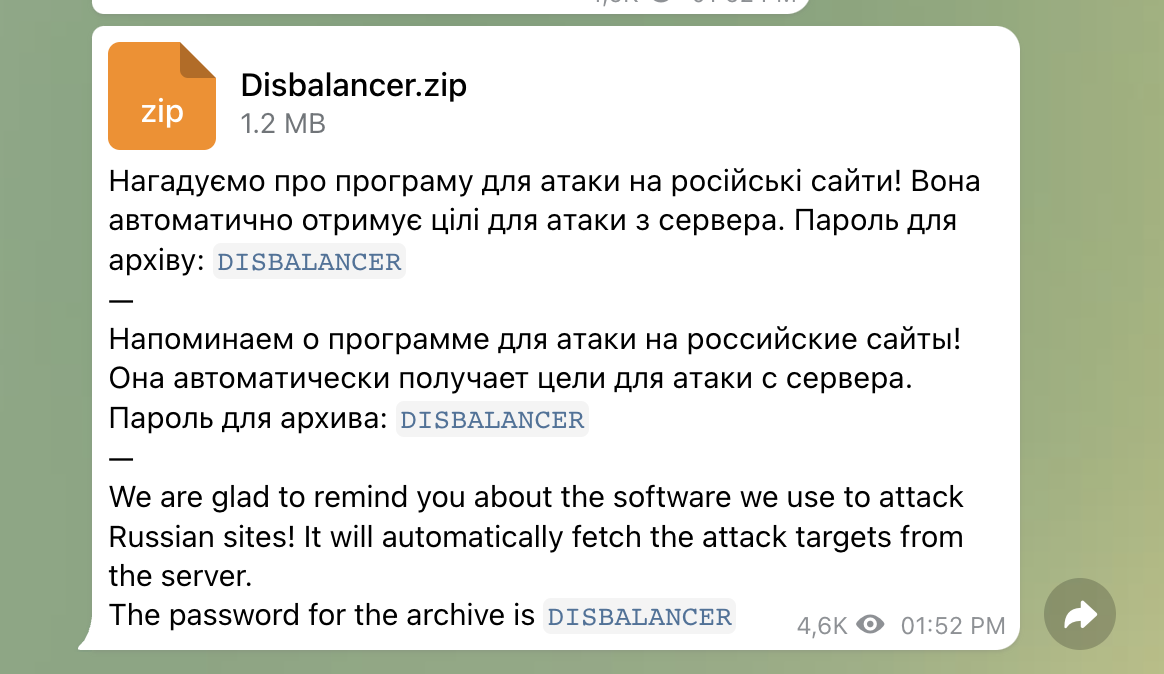
According to the Telegram postings, the application downloads a list of Russian targets to attack from a server, so the user doesn’t have to do anything other than run it on their computer.
Those who support Ukraine but are not particularly technically savvy or who do not know how to conduct their own “bombing” operations against Russian targets will certainly find this feature appealing.
If you liked this article, follow us on LinkedIn, Twitter, Facebook, Youtube, and Instagram for more cybersecurity news and topics.










 Network Security
Network Security
 Vulnerability Management
Vulnerability Management
 Privileged Access Management
Privileged Access Management  Endpoint Security
Endpoint Security
 Threat Hunting
Threat Hunting
 Unified Endpoint Management
Unified Endpoint Management
 Email & Collaboration Security
Email & Collaboration Security








