Contents:
On Twitter, verified accounts are those that have a blue badge with a checkmark. These accounts often represent well-known influencers, celebrities, politicians, journalists, activists, as well as government and commercial entities.
The blue verified badge on Twitter lets people know that an account of public interest is authentic. To receive the blue badge, your account must be authentic, notable, and active.
What Happened?
Twitter verified accounts are now being targeted as part of a large phishing attempt that takes advantage of Twitter’s removal of the verified badge from numerous verified profiles.
So @Twitter has removed my blue tick verification because they can’t be sure I’m me. Fair enough, some days I’m not entirely sure myself…
— Jamie Theakston (@JamieTheakston) December 2, 2021
The campaign sends an email to users, generally to the email address listed in their Twitter profile, requesting them to help verify their identity in order to maintain their verified status.
It’s interesting to note that the phishing campaign is happening soon after Twitter’s CEO, Jack Dorsey, decided to leave the position he held for over 16 years.
How Does the Phishing Campaign Work?
As BleepingComputer editor, Ax Sharma, reports the phishing email advises the Twitter user to “update” their information to avoid losing their verified status.
The phishing email is apparently sent to verified users, many of whom may choose to list an email address in their bio for business reasons.
The phishing message first entices the user to tap the “Update here” button.
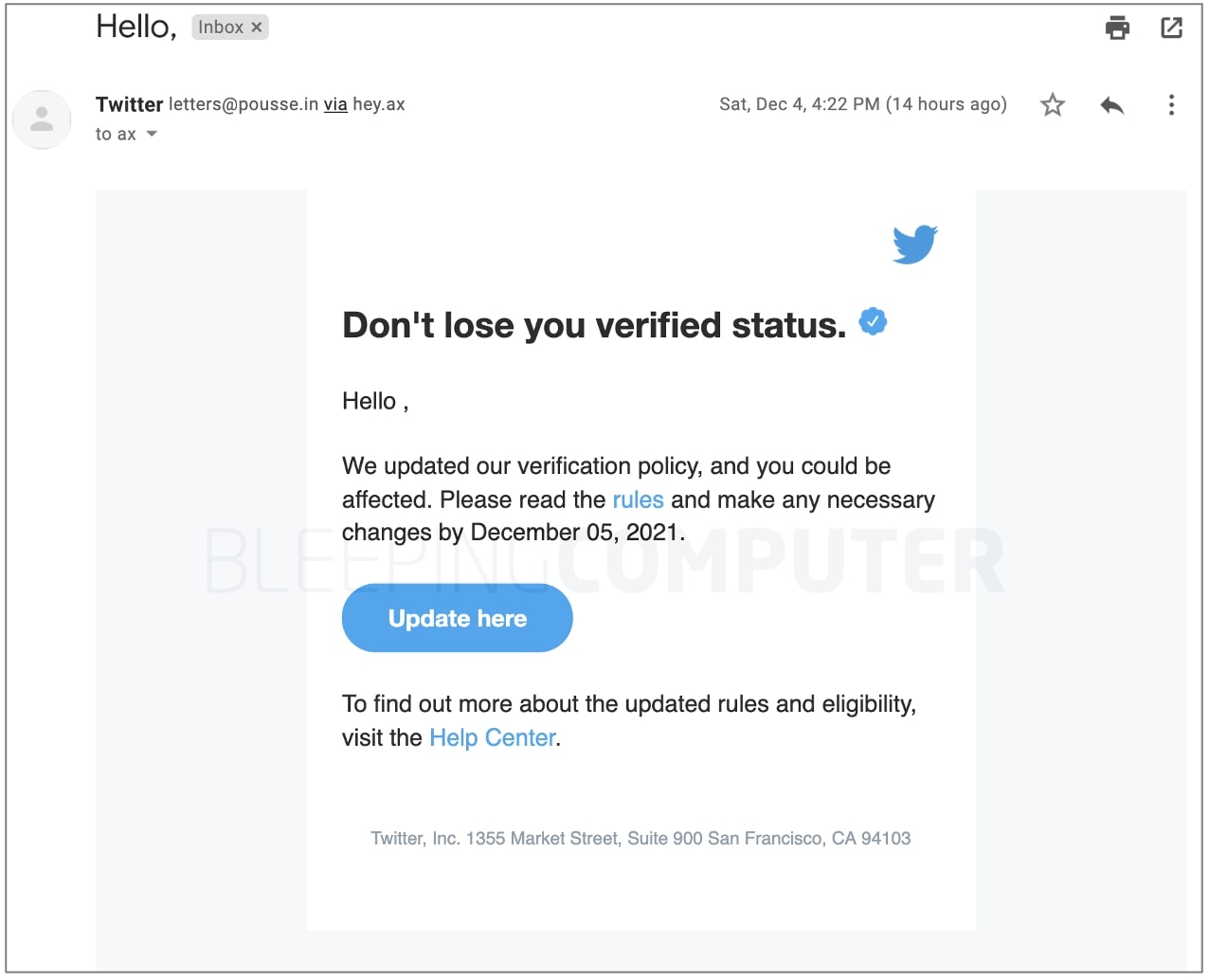
The button links to https://www.cleancredit[.]in/wp-content/uploads/2021/12/index.html which further redirects the user to a page living at: https://dublock[.]com/dublock/twitter/.
Both of these websites appear to have been hijacked and used to host phishing pages by the attackers.
Following the entry of Twitter credentials, which the form fails to validate, the user is requested to input the two-factor authentication code issued to them.
The phishing website leads the user to the Twitter homepage after obtaining the user’s Twitter username, password, and two-factor authentication code.
Twitter users, verified or not, should be cautious of such phishing communications and avoid accessing any links or files included inside.
How Can Heimdal™ Help You?
HeimdalTM Security has developed two email security software aimed against both simple and sophisticated email threats: Heimdal™ Email Security, which detects and blocks malware, spam emails, malicious URLs, and phishing attacks and Heimdal™ Email Fraud Prevention, a revolutionary email protection system against employee impersonation, fraud attempts – and BEC, in general.
By using over 125 vectors of analysis and being fully supported by threat intelligence, it detects phraseology changes, performs IBAN/Account number scanning, identifies modified attachments, malicious links, and Man-in-the-Email attacks. Furthermore, it integrates with O365 and any mail filtering solutions and includes live monitoring and alerting 24/7 by our specialists.
As Heimdal™ is always updated and keeps pace with the latest cybersecurity trends, you’ll be protected from this type of threat.
Our awarded Threat Prevention Endpoint solution uses Machine Learning, cybercrime intelligence, and artificial intelligence capabilities to help you prevent future threats with 96% accuracy on your endpoints, a very efficient threat hunting solution that makes malicious URLs, processes, and attacker’s origins no longer anonymous.
If you liked this article, follow us on LinkedIn, Twitter, Facebook, Youtube, and Instagram for more cybersecurity news and topics.










 Network Security
Network Security
 Vulnerability Management
Vulnerability Management
 Privileged Access Management
Privileged Access Management  Endpoint Security
Endpoint Security
 Threat Hunting
Threat Hunting
 Unified Endpoint Management
Unified Endpoint Management
 Email & Collaboration Security
Email & Collaboration Security








