Contents:
Yesterday, cybersecurity researchers stated that the Russian Advanced Persistent Threat (APT) actor Turla has been developing and employing a new backdoor used to infect systems in Afghanistan, Germany, and the U.S.
Who Is Turla?
Turla APT group, also known in the information security field as Snake, Venomous Bear, Uroburos, or WhiteBear, is an advanced operation that has been operational since at least 2004.
The infamous group has a long list of high-profile victims from all over the world in its portfolio. The APT attacked various European government entities and organizations in the U.S., Ukraine, and Arabic countries.
Turla’s attacking methods include covert exfiltration tactics using hijacked satellite connections, watering hole attacks, rootkits, and hidden channel backdoors.
TinyTurla Malware Operation Mode
According to the researchers, the new malware, dubbed TinyTurla, is probably utilized as a second-chance backdoor to carry on access to the network when the initial malware is removed.
They also said it could be employed as a second-stage dropper to infect the system with even more malware.
Anti-malware systems have a hard time detecting this backdoor as malware because of its limited functionality and simple coding style. TinyTurla’s can only download, upload, and execute files.
Security researchers at Cisco Talos have proof that malicious actors have employed the backdoor since at least 2020.
This malware specifically caught our eye when it targeted Afghanistan prior to the Taliban’s recent takeover of the government there and the pullout of Western-backed military forces.
The New Backdoor Used to Target Entities Around the World
Based on forensic evidence, the security researchers determined that TinyTurla was used to attack the previous government of Afghanistan.
Cisco Talos’ telemetry indicates that the backdoor was also used to target networks in the U.S. and Germany as the specialists stated they have seen infections in these countries.
TinyTurla malware connection to the Russian-based cybercriminals was possible as the hackers employed the same infrastructure observed in other cyberattacks the Turla APT threat actor conducted in the past.
One public reason why we attributed this backdoor to Turla is the fact that they used the same infrastructure as they used for other attacks that have been clearly attributed to their Penguin Turla infrastructure.
The security specialists have collected the following C2_command_codes for the different backdoor functions:
- 0x00:’Authentication’
- 0x01:’Execute process’
- 0x02:’Execute with output collection’
- 0x03:’Download file’
- 0x04:’Upload file’
- 0x05:’Create Subprocess’
- 0x06:’Close Subprocess ‘
- 0x07:’Subprocess pipe in/out’
- 0x08:’Set TimeLong’
- 0x09:’Set TimeShort’
- 0x0A:’Set new ‘Security’ password’
- 0x0B:’Set Host(s)’
The researchers stated that they don’t know for sure how the backdoor was installed on the target’s system. What they knew is that the hacker used a .bat file to install the TinyTurla virus.
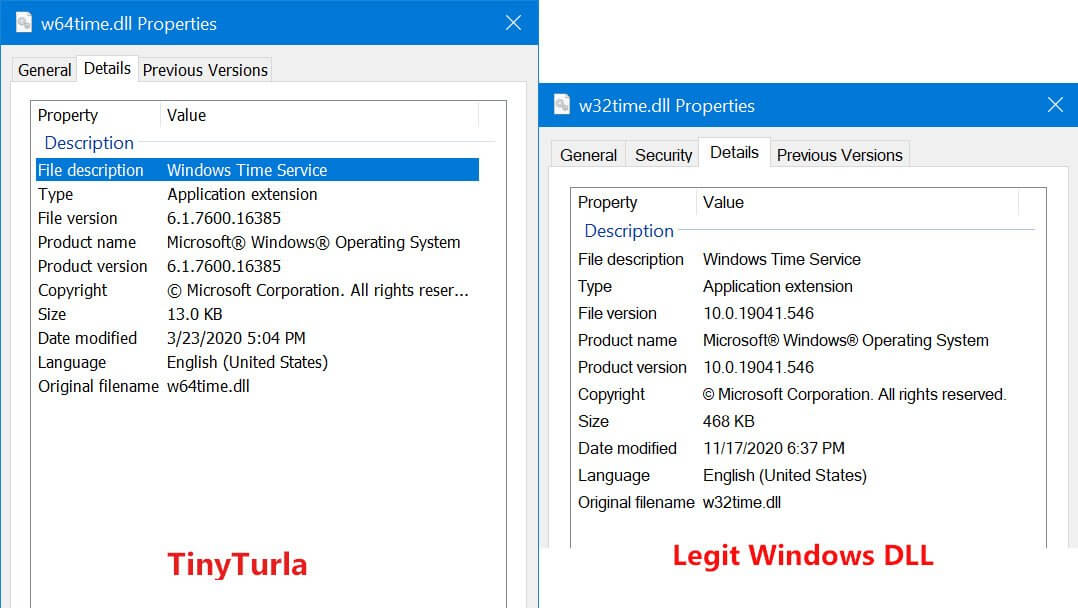
According to them, the malware poses as a service DLL called w64time.dll and tries to trick the victims into thinking that it is w32time.dll, a legitimate Windows Time Service.
It doesn’t look like the Turla APT group will disappear any time soon and yes, they are an advanced malware but they also make mistakes. Organizations must invest in a multi-layered security solution in order to detect and protect their business from these attacks.


 Network Security
Network Security
 Vulnerability Management
Vulnerability Management
 Privileged Access Management
Privileged Access Management
 Endpoint Security
Endpoint Security
 Threat Hunting
Threat Hunting
 Unified Endpoint Management
Unified Endpoint Management
 Email & Collaboration Security
Email & Collaboration Security










