Contents:
It was recently discovered that a U.S. No Fly list, containing over 1.5 million records of banned flyers and 250,000 ‘selectees’ has been found published on a hacking forum. According to BleepingComputer, it’s the same TSA No Fly list that was found on an unsecured CommuteAir server.
Can’t Fly No More
Per Daily Dot journalist Mikael Thalen, the list was made publicly available by Swiss hacker maia arson crimew, formerly known as Tillie Kottmann. The hacker apparently got in the possession of the list through a misconfigured AWS server belonging to Ohio-based airline CommuteAir. Steps were taken immediately to patch the leak, but the list surfaced regardless.
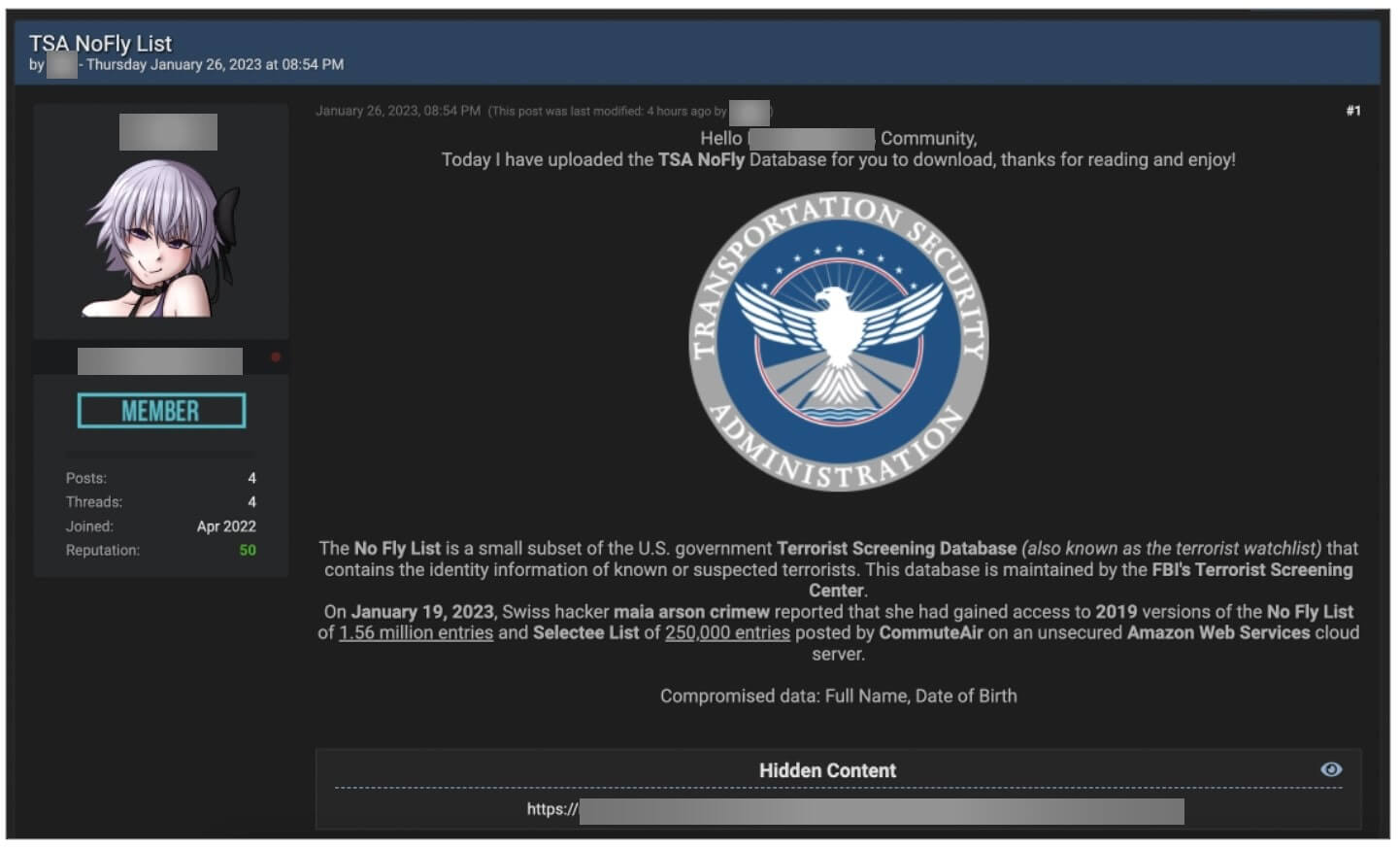
TSA NoFly List Blog Post (Source: BleepingComputer)
BleepingComputer, with support from Thalen, confronted the list posted on the blog with another one found on the CommuteAir server. Two CSV files were analysed, ‘NOFLY’ and ‘SELECTEE’, with the latter likely listing names of passengers who undergo a Secondary Security Screening Selection (SSSS) upon their arrival at U.S. airports.
The ‘NOFLY’ spread contained over 1.5 million records, including duplicates and spelling variations of some names, indicating that the number of names exposed is lower than the number of recorded entries in the spreadsheet. The ‘SELECTEE’ spread is comprised of 251,169 records. The lists from the year 2019 include first names, last names, dates of birth, and even potential aliases of the surveilled persons.
The ‘No Fly List’ is also known as the Terrorist Screening Database, and is relied upon by multiple federal agencies to manage and share consolidated info for counterterrorism purposes.
Given the crucial role they play in assisting with duties related to national security and law enforcement, even though they are not “classified,” such databases are hidden and considered to be sensitive in nature. The government may “nominate” terrorists or plausible suspects who represent a threat to national security for inclusion on the secret watchlist. One such entry discovered by Daily Dot is the Russian arms dealer Viktor Bout, together with his 16 potential aliases.
The U.S. Government Opened an Investigation
When inquired by BleepingComputer to give more detail on the incident, a TSA spokesperson declared that the organization has started an investigation to get to the bottom of the problem. A security directive was issued to airports and air carriers on the 27th of January.
According to the TSA spokesperson,
The security directive reinforces existing requirements on handling sensitive security information and personally identifiable information. We will continue to work with partners to ensure that they implement security requirements to safeguard systems and networks from cyberattacks.
TSA Spokesperson on the issue (Source)
Another source close to the matter informed BleepingComputer that no TSA information systems were compromised as part of the breach.
CommuteAir also addressed the incident in a statement shared with BleepingComputer:
CommuteAir was notified by a member of the security research community who identified a misconfigured development server. The researcher accessed files uploaded to the server in July 2022 that included outdated 2019 versions of the federal no-fly and selectee lists that contained certain individuals’ names and dates of birth. The lists were used for testing our software-based compliance process for implementing federally-mandated security requirements. Additionally, through the server, the researcher accessed a database containing personal identifiable information of CommuteAir employees. CommuteAir immediately took the affected server offline and started an investigation to determine the extent of data access. To date, our investigation indicates that no customer data was exposed. CommuteAir has reported the data exposure to the Cybersecurity and Infrastructure Security Agency, and also notified its employees.
CommuteAir Spokesperson (Source)
A Matter of National Security
U.S. Congressman Dan Bishop, alongside Dr. Mark Green, the Homeland Security Committee chairman, posted a series of questions addressed to David Peter Pekoske, the TSA Administrator.
It’s crucial to keep in mind that, given the hacker’s assertions, the incident may now involve matters of national security rather than just the discovery of a data breach.
The hacker claimed they may have been able to exploit their access to the server to cancel or delay flights and even switch out crew members. If this were to be the case, the national security implications of this are alarming,
If you liked this article, follow us on LinkedIn, Twitter, Facebook, Youtube, and Instagram for more cybersecurity news and topics.


 Network Security
Network Security
 Vulnerability Management
Vulnerability Management
 Privileged Access Management
Privileged Access Management
 Endpoint Security
Endpoint Security
 Threat Hunting
Threat Hunting
 Unified Endpoint Management
Unified Endpoint Management
 Email & Collaboration Security
Email & Collaboration Security










