Contents:
Researchers have recently discovered a new phishing scam focused on stealing information and locking out over 125 high-profile TikTok accounts belonging to influencers, brand consultants, production companies, and influencers’ managers.
How Did It Happen?
Cybersecurity experts at cloud email security provider Abnormal Security discovered the phishing campaign in which attackers attempted to take over the users’ accounts by sending emails posing as TikTok and asking them to confirm their log-in details.
While analyzing the distribution of emails in this operation, Abnormal Security specialists saw two activity peaks on October 2, 2021, and November 1, 2021, indicating that a new wave will most likely begin in a few weeks. According to them, the campaign was sent to individuals all over the world.
What Were the Emails Saying?
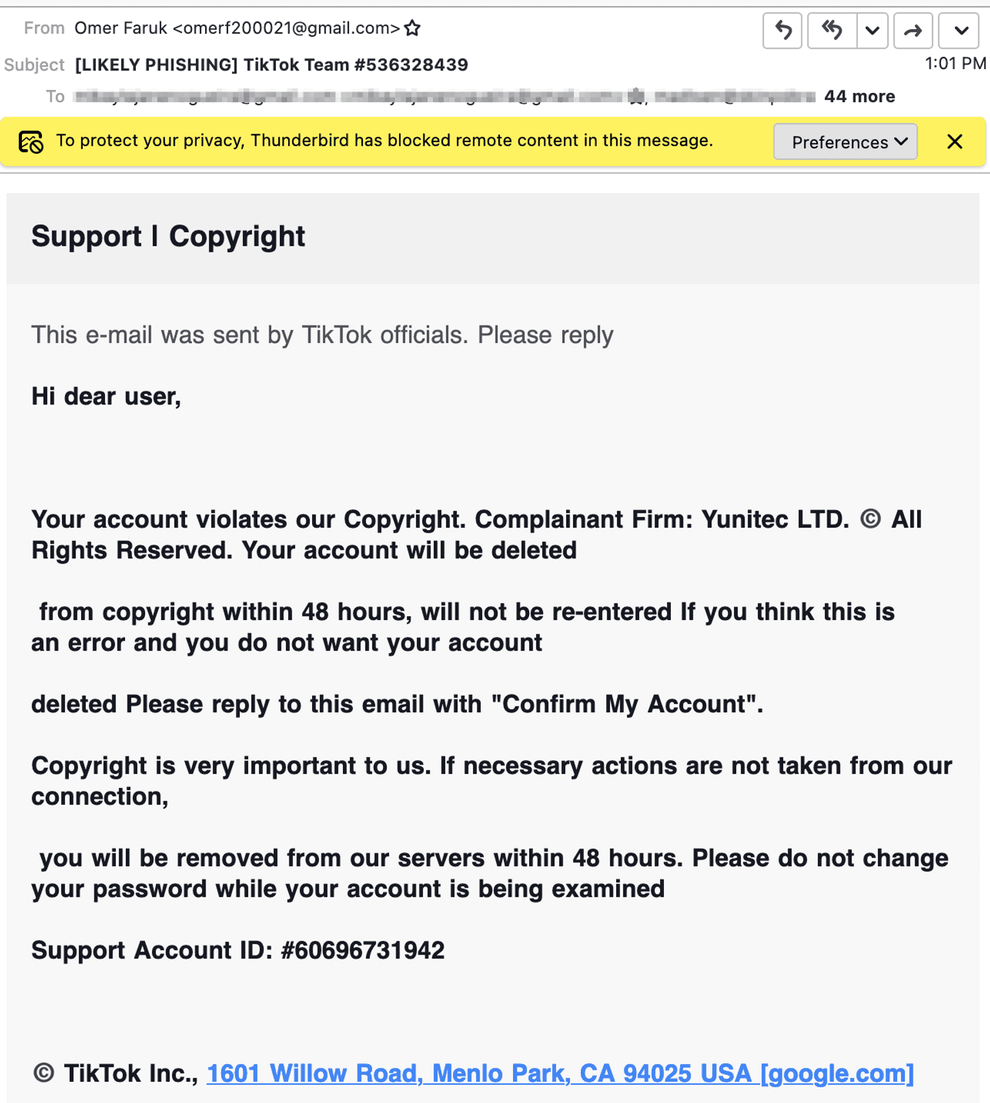
According to Abnormal Security, in some instances, the cybercriminals pretended to be TikTok personnel, trying to intimidate the user with account deactivation threats due to a supposed violation of TikTok’s terms.
In these cases, the victim was requested to respond to the email in order to confirm the account, threatening to delete the account in 48 hours if no action was taken.
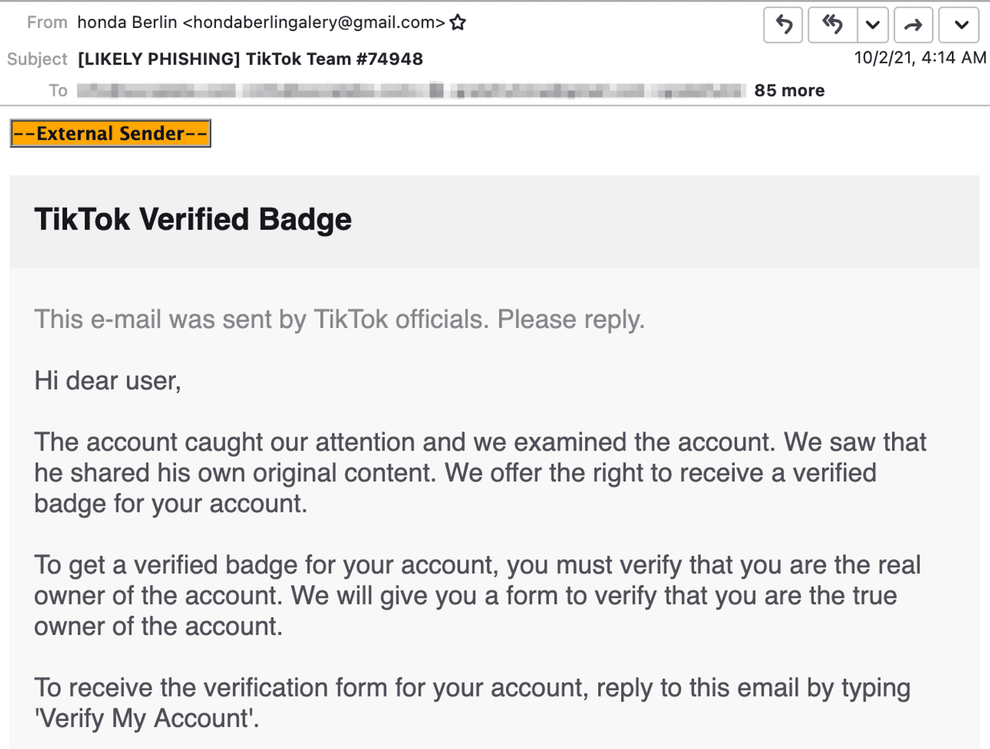
A second email, purportedly sent by “TikTok officials,” notified account owners that their account was qualified for a “verified badge” and asked them to respond so the account could be correctly verified.
The “Verified badge” tactic increases the account’s credibility and authenticity.
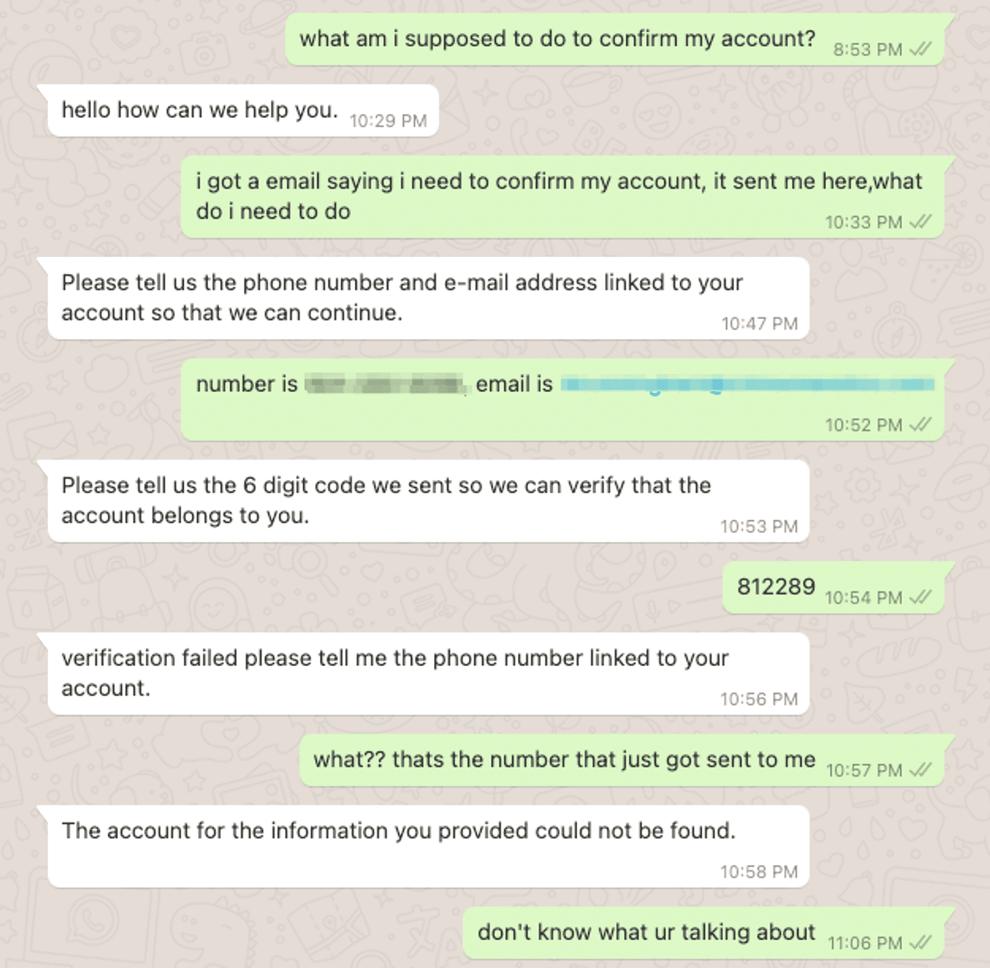
In both situations, the emails received by the victims included an embedded link they had to click on in order to confirm their accounts. Instead, they were sent to a WhatsApp chat room, where they were greeted by a scammer posing as a TikTok representative.
The fake employee then requested their email address, contact information, and the one-time code needed to bypass multi-factor authentication and reset their password.
What’s the Motive?
As explained by the researchers, multiple users who were targeted in this phishing scam had their accounts removed or taken over, and their data was stolen as a result of the attack.
However, beyond, this, specialists did not see a clear motive for the operation that would benefit phishing actors.
It could be an attempt to gain control of the victims’ accounts, or it could be an attempt to extort the account holders and make them pay a ransom in exchange for giving them back control.
Recommendations for TikTok Users
Those owning or managing important social media account should:
- make sure to backup all their content and data somewhere safe;
- always secure their account with two-factor authentication (2FA) or 2-step verification.
How Can Heimdal™ Help You?
HeimdalTM Security has developed two email security software aimed against both simple and sophisticated email threats: Heimdal™ Email Security, which detects and blocks malware, spam emails, malicious URLs, and phishing attacks and Heimdal™ Email Fraud Prevention, a revolutionary email protection system against employee impersonation, fraud attempts – and BEC, in general.
For example, you may want to consider HeimdalTM Security’s Heimdal™ Email Fraud Prevention, the ultimate email protection against financial email fraud, C-level executive impersonation, phishing, insider threat attacks, and complex email malware. How does it work? By using over 125 vectors of analysis and being fully supported by threat intelligence, it detects phraseology changes, performs IBAN/Account number scanning, identifies modified attachments, malicious links, and Man-in-the-Email attacks. Furthermore, it integrates with O365 and any mail filtering solutions and includes live monitoring and alerting 24/7 by our specialists.
If you liked this article follow us on LinkedIn, Twitter, YouTube, Facebook, and Instagram to keep up to date with everything cybersecurity.


 Network Security
Network Security
 Vulnerability Management
Vulnerability Management
 Privileged Access Management
Privileged Access Management
 Endpoint Security
Endpoint Security
 Threat Hunting
Threat Hunting
 Unified Endpoint Management
Unified Endpoint Management
 Email & Collaboration Security
Email & Collaboration Security