Contents:
Microsoft declares that Iranian cybercrime organizations have been trying to breach IT services businesses more frequently this year to collect credentials that they could further use to compromise the networks of downstream customers.
According to cybersecurity experts at Microsoft Threat Intelligence Center (MSTIC) and Digital Security Unit (DSU), this operation is part of a larger espionage strategy to hack organizations of interest to the Iranian government.
This activity is notable because targeting third parties has the potential to exploit more sensitive organizations by taking advantage of trust and access in a supply chain.
Microsoft has observed multiple Iranian threat actors targeting the IT services sector in attacks that aim to steal sign-in credentials belonging to downstream customer networks to enable further attacks.
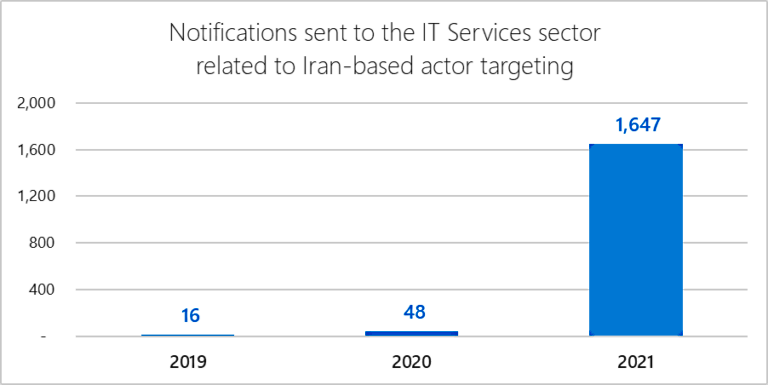
According to BleepingComputer, more than 1,600 notifications were sent by Redmond to over 40 IT services organizations, alerting them of hacking attempts conducted by Iran-based Advanced Persistent Threat (APT) gangs. When compared to 2020, when Microsoft only sent 48 notifications throughout the year, we notice that it has been a significant increase.
Israel and the United Arab Emirates Firms Also Targeted
The majority of these attacks target Indian IT services companies, with a few of them also focusing on organizations located in Israel and the United Arab Emirates.
As per Microsoft, in July and September, two Iranian cybercrime gangs known as DEV-0228 and DEV-0056 managed to compromise organizations in the IT sector in Israel and Bahrain.
In July 2021, a group that MSTIC tracks as DEV-0228 and assesses as based in Iran compromised a single Israel-based IT company that provides business management software. Based on MSTIC’s assessment, DEV-0228 used access to that IT company to extend their attacks and compromise downstream customers in the defense, energy, and legal sectors in Israel.
In September, we detected a separate Iranian group, DEV-0056, compromising email accounts at a Bahrain-based IT integration company that works on IT integration with Bahrain Government clients, who were likely DEV-0056’s ultimate target. DEV-0056 also compromised various accounts at a partially government-owned organization in the Middle East that provide information and communications technology to the defense and transportation sectors, which are targets of interest to the Iranian regime. DEV-0056 maintained persistence at the IT integration organization through at least October.
Iranian Threat Actors, a Real Threat
Lately, multiple advisories and reports have warned of Iranian operations targeting companies around the world, with the Iran-based threat actors getting a great deal of public attention.
The FBI, CISA, ACSC, and the United Kingdom’s National Cyber Security Centre recently warned of a state-backed Iranian hacker who has been using various CVEs to establish a foothold within networks before moving laterally and unleashing BitLocker ransomware, and other malicious tools including both critical Fortinet vulnerabilities and a Microsoft Exchange ProxyShell flaw.
Also, the Microsoft Threat Intelligence Center (MSTIC) reported that six Iranian cybercrime orgs began deploying ransomware and exfiltrating information from targets’ networks in September last year.
Earlier this month, the Federal Bureau of Investigation (FBI) issued a warning for private business partners about an Iranian cybercriminal’s attempt to purchase stolen data belonging to the US and international companies.
The federal law enforcement agency stated that attackers will probably use stolen material such as email messages and network information purchased from clear and dark websites to compromise the systems of related organizations.
If you liked this article, follow us on LinkedIn, Twitter, Facebook, Youtube, and Instagram for more cybersecurity news and topics.


 Network Security
Network Security
 Vulnerability Management
Vulnerability Management
 Privileged Access Management
Privileged Access Management
 Endpoint Security
Endpoint Security
 Threat Hunting
Threat Hunting
 Unified Endpoint Management
Unified Endpoint Management
 Email & Collaboration Security
Email & Collaboration Security










